1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
| import os
import subprocess
mem_file = "E:\\BaiduNetdiskDownload\\1.mem"
profile = "Linuxubuntu-5_4_0-205-genericx64"
volatility_path = "D:\\Software\\LovelyMem\\Tools\\volatility-master\\vol.py"
python_path = "D:\\Software\\LovelyMem\\Tools\\python27\\python27.exe"
output_dir = "."
if not os.path.exists(output_dir):
os.makedirs(output_dir)
files_to_extract = [
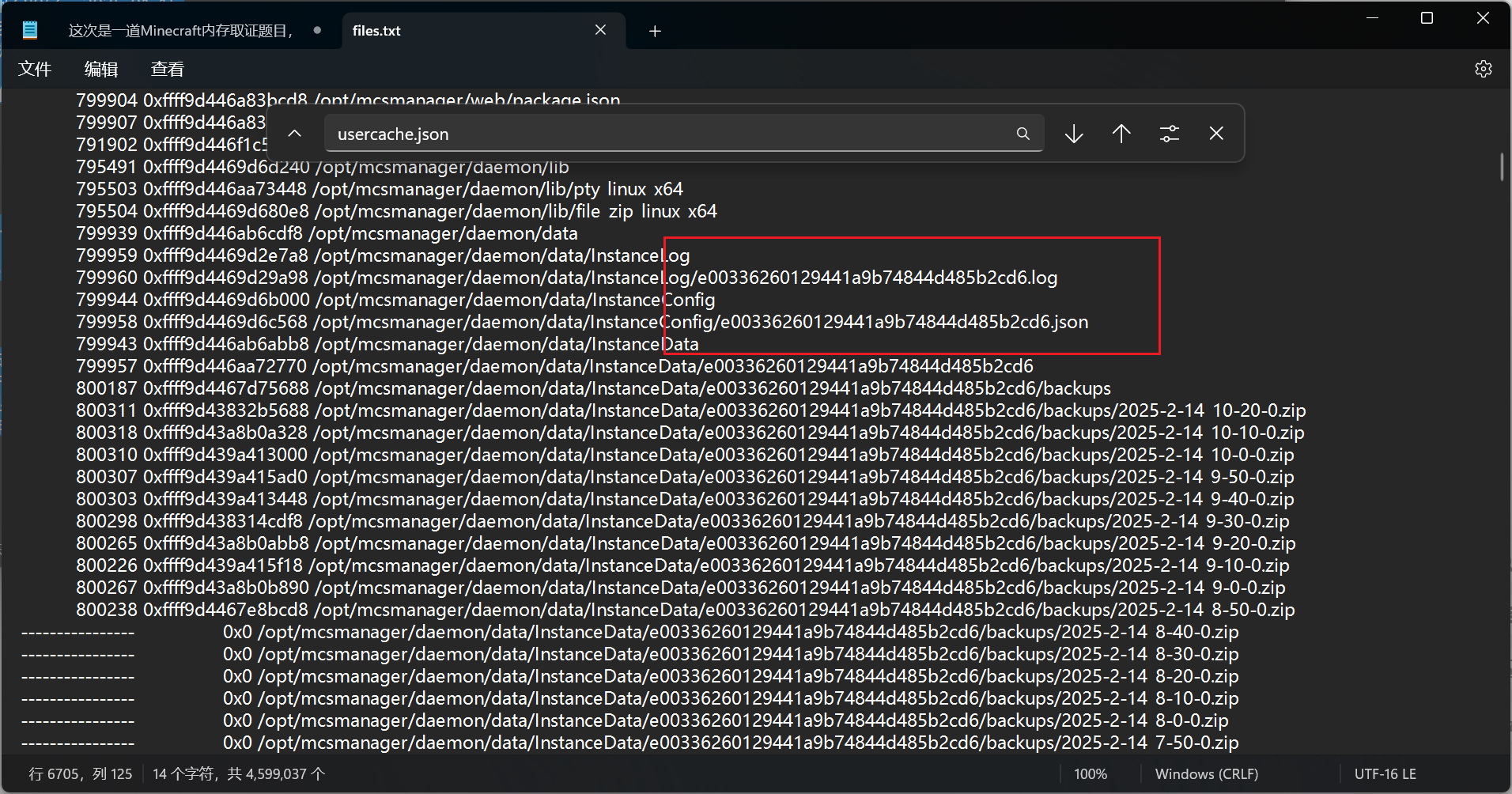
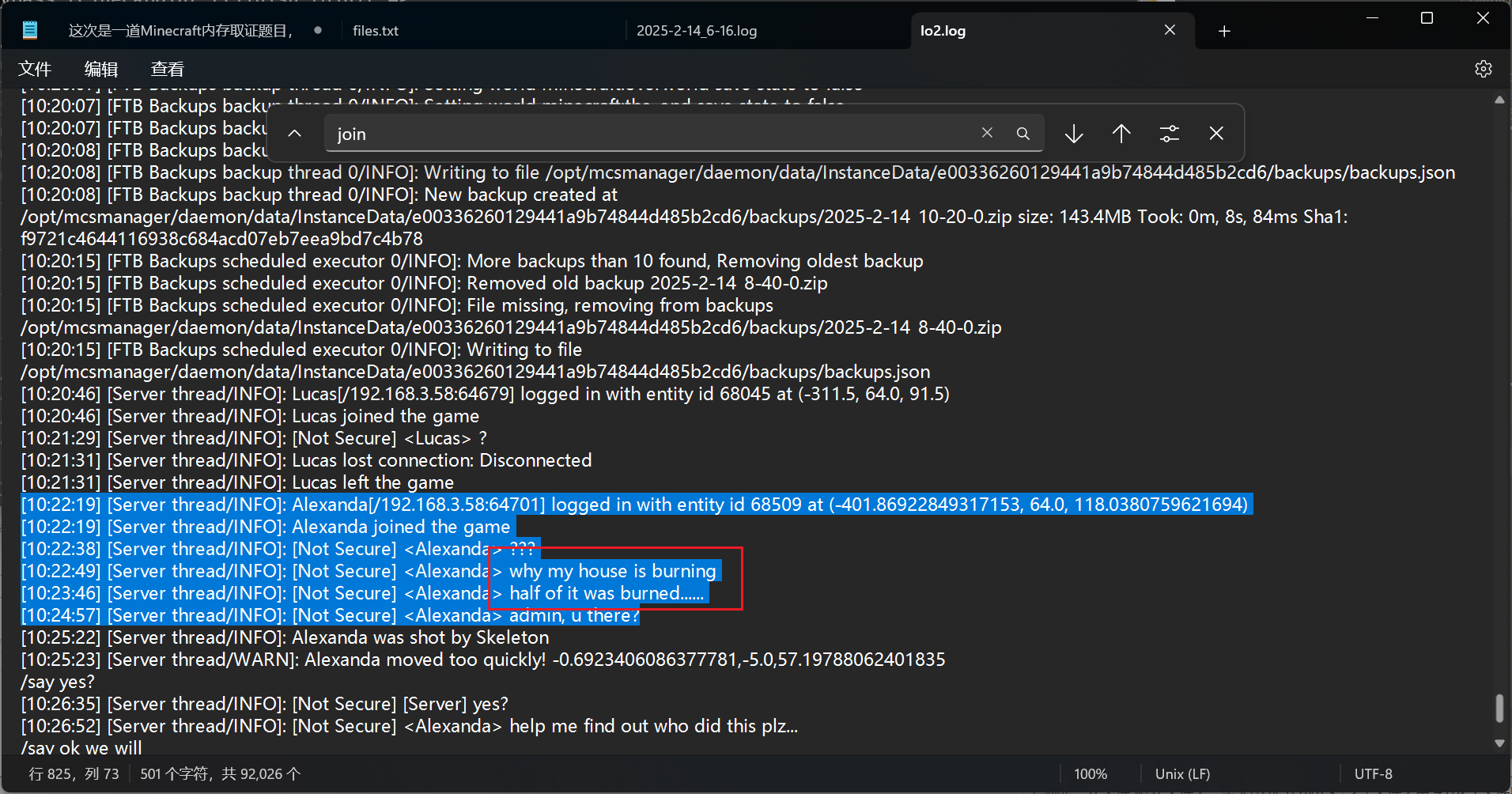
("0xffff9d4469d29a98", "/opt/mcsmanager/daemon/data/InstanceLog/e00336260129441a9b74844d485b2cd6.log"),
("0xffff9d43832b3890",
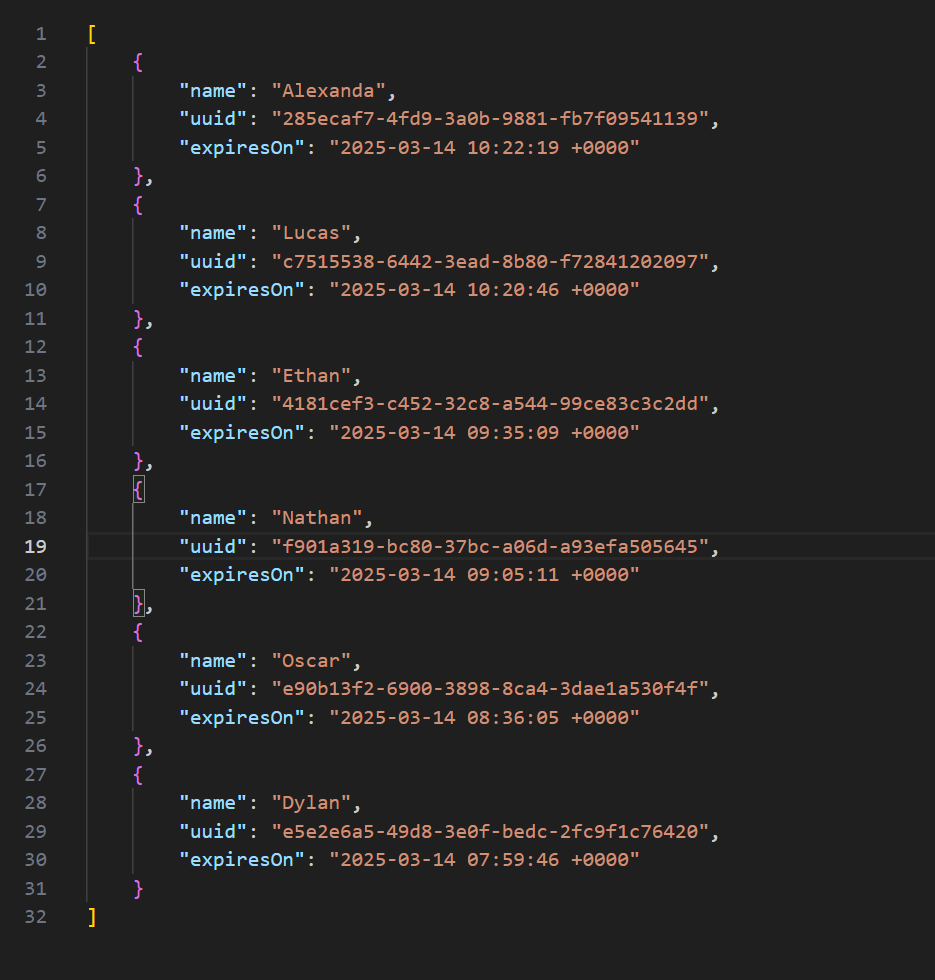
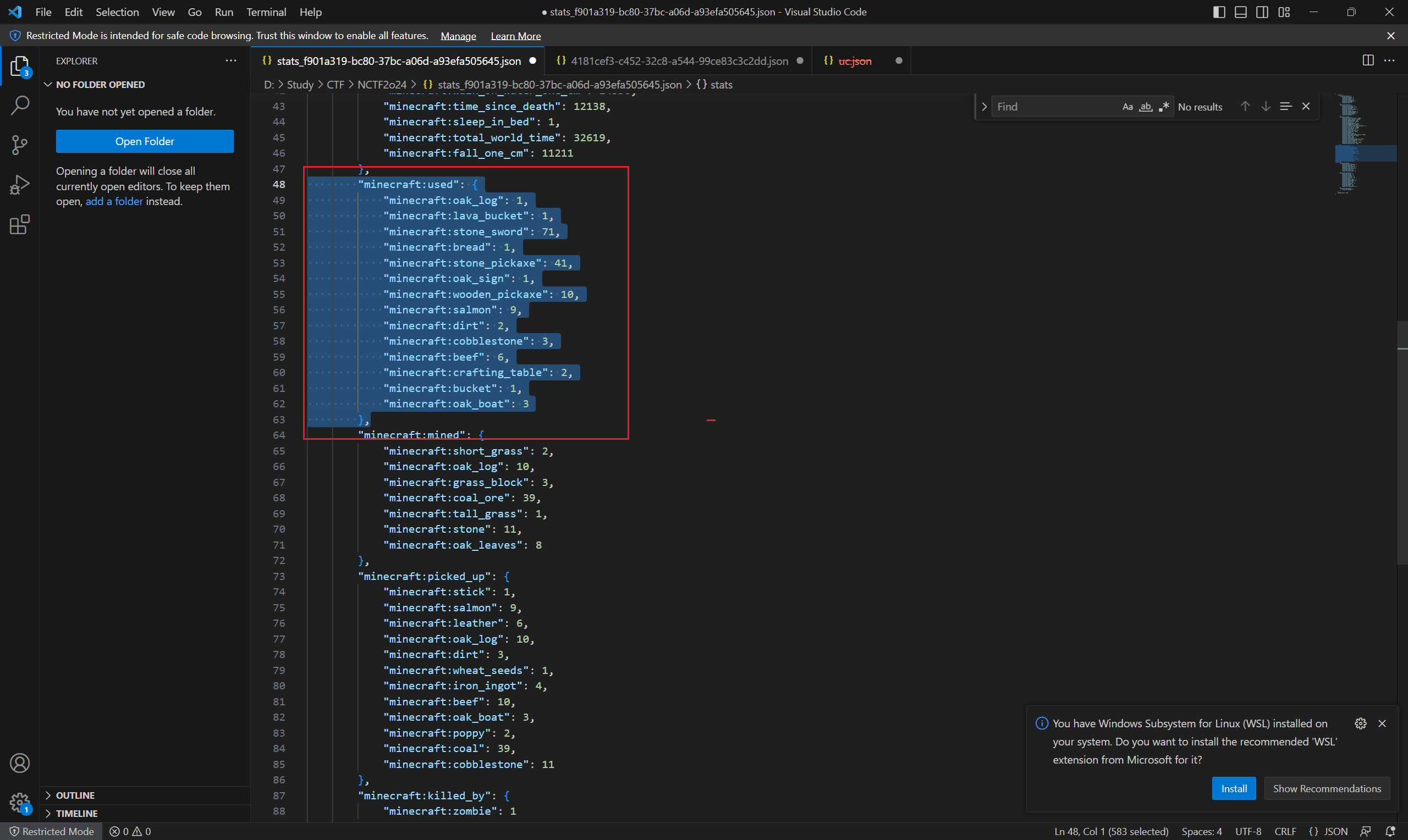
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/stats/c7515538-6442-3ead-8b80-f72841202097.json"),
("0xffff9d43832b1650",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/stats/4181cef3-c452-32c8-a544-99ce83c3c2dd.json"),
("0xffff9d43a8b08978",
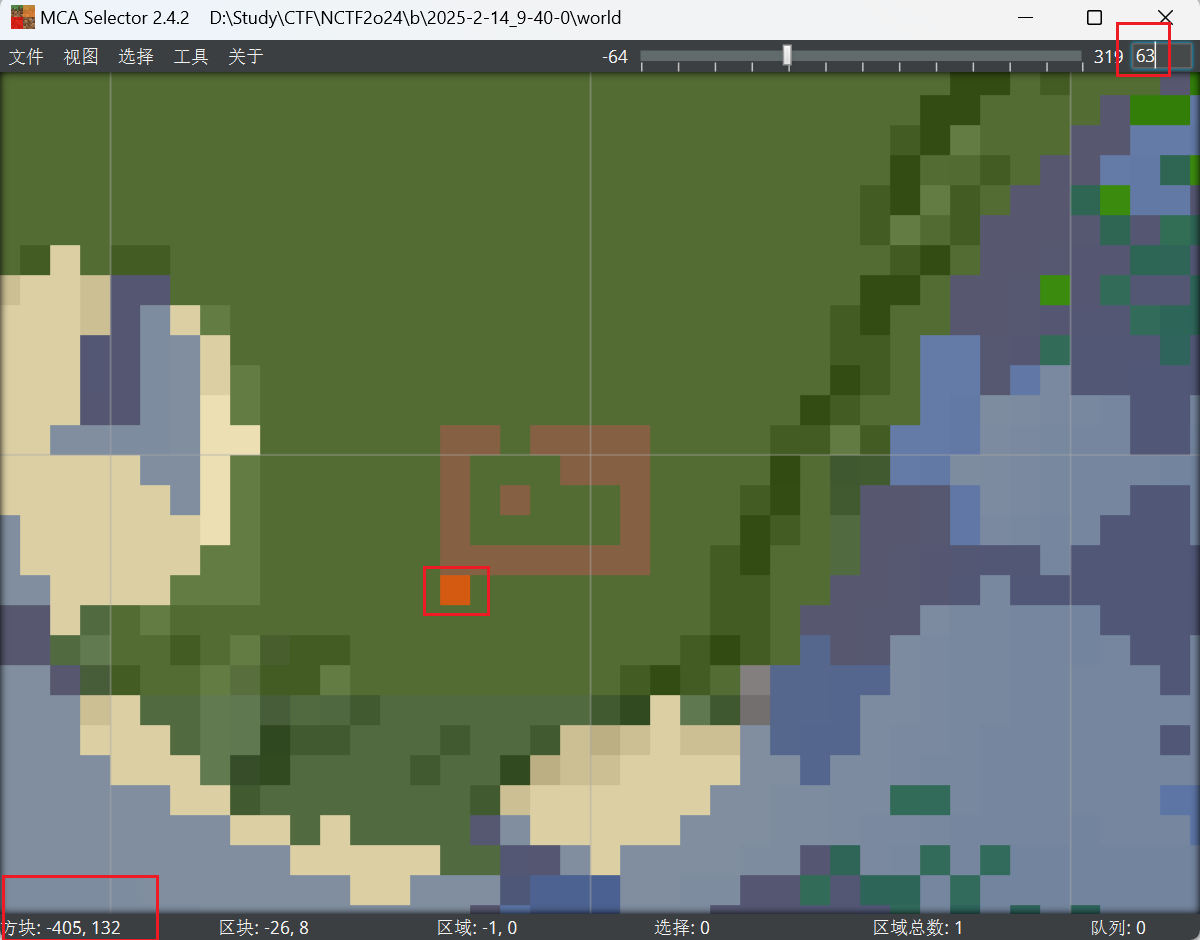
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/stats/f901a319-bc80-37bc-a06d-a93efa505645.json"),
("0xffff9d43a8b0b000",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/stats/e90b13f2-6900-3898-8ca4-3dae1a530f4f.json"),
("0xffff9d4467ea2bb8",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/stats/e5e2e6a5-49d8-3e0f-bedc-2fc9f1c76420.json"),
("0xffff9d4467e8e7a8",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/stats/285ecaf7-4fd9-3a0b-9881-fb7f09541139.json"),
("0xffff9d43832b3cd8",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/advancements/c7515538-6442-3ead-8b80-f72841202097.json"),
("0xffff9d43832b5ad0",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/advancements/4181cef3-c452-32c8-a544-99ce83c3c2dd.json"),
("0xffff9d43a8b09208",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/advancements/f901a319-bc80-37bc-a06d-a93efa505645.json"),
("0xffff9d43a8b0c568",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/advancements/e90b13f2-6900-3898-8ca4-3dae1a530f4f.json"),
("0xffff9d4467ea0dc0",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/advancements/e5e2e6a5-49d8-3e0f-bedc-2fc9f1c76420.json"),
("0xffff9d4467e8b448",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/world/advancements/285ecaf7-4fd9-3a0b-9881-fb7f09541139.json"),
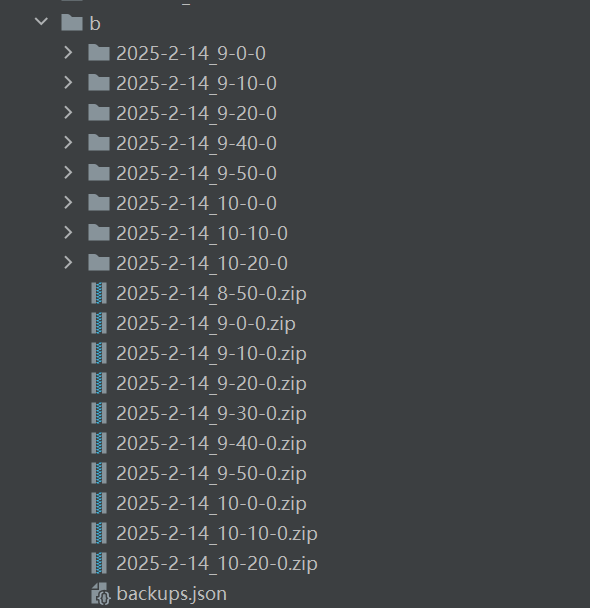
("0xffff9d43a8b0b890",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/backups/2025-2-14_9-0-0.zip"),
("0xffff9d4467e8bcd8",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/backups/2025-2-14_8-50-0.zip"),
("0xffff9d4467e5c9b0", "/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/whitelist.json"),
("0xffff9d4467e5f480", "/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/ops.json"),
("0xffff9d4467e580e8", "/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/banned-ips.json"),
("0xffff9d4467e5d240",
"/opt/mcsmanager/daemon/data/InstanceData/e00336260129441a9b74844d485b2cd6/banned-players.json")
]
for offset, file_path in files_to_extract:
filename = os.path.basename(file_path)
dir_name = os.path.dirname(file_path).split('/')[-1]
output_filename = f"{dir_name}_{filename}" if dir_name else filename
output_path = os.path.join(output_dir, output_filename)
cmd_extract = f'{python_path} {volatility_path} -f {mem_file} --profile={profile} linux_find_file -O "{output_path}" -i {offset}'
print(f"提取: {cmd_extract}")
try:
subprocess.call(cmd_extract, shell=True)
print(f"已提取: {file_path} -> {output_path}")
except Exception as e:
print(f"提取失败: {file_path}, 错误: {str(e)}")
print("-" * 60)
|