2024春秋杯冬季赛Day3
12 Misc 音频的秘密
Deepsound弱密码123,直接猜到了
然后png头明文攻击
.\bkcrack.exe -C flag.zip -c flag.png -p 1.txt -o 0
bkcrack 1.7.1 - 2024-12-21
[16:30:13] Z reduction using 9 bytes of known plaintext
100.0 % (9 / 9)
[16:30:13] Attack on 734325 Z values at index 6
Keys: 29d29517 0fa535a9 abc67696
20.4 % (150044 / 734325)
Found a solution. Stopping.
You may resume the attack with the option: –continue-attack 150044
[16:30:52] Keys
29d29517 0fa535a9 abc67696
.\bkcrack.exe -C .\flag.zip -k 29d29517 0fa535a9 abc67696 -D dec.zip
然后stegsolve看lsb
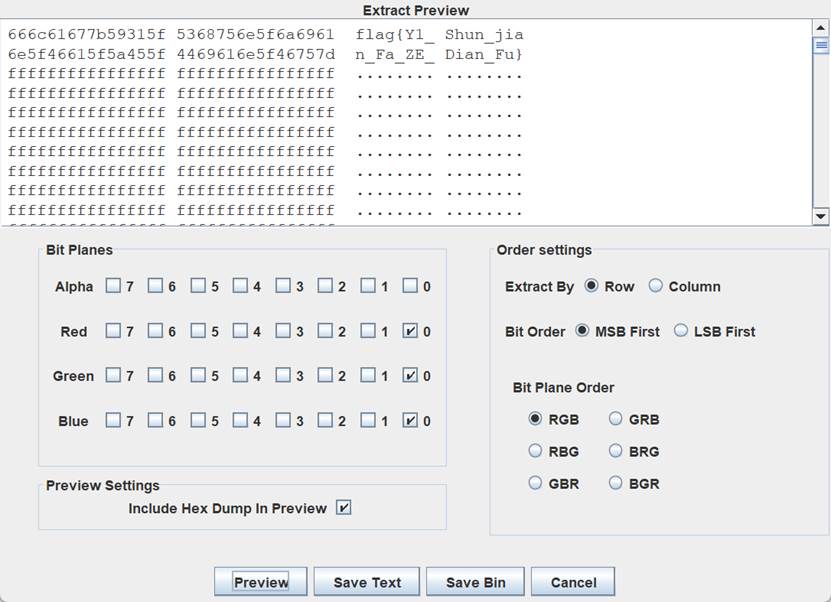
flag{Y1_Shun_jian_Fa_ZE_Dian_Fu}
13 Crypto funny_rsa
真难绷,fakeflag里面是flag
1 | |
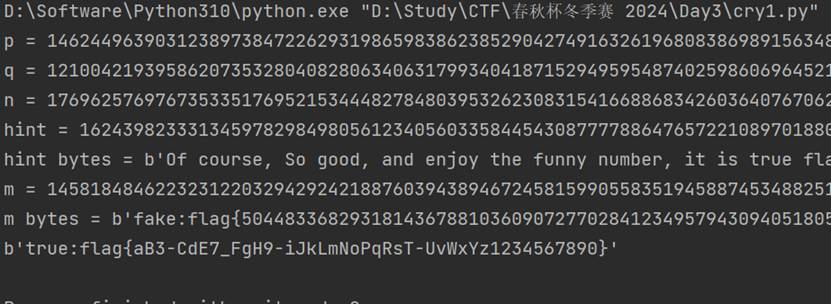
flag{aB3-CdE7_FgH9-iJkLmNoPqRsT-UvWxYz1234567890}
14 Web easy_php
给了源码,看了一下file.php可以读文件,直接file.php?file=/flag
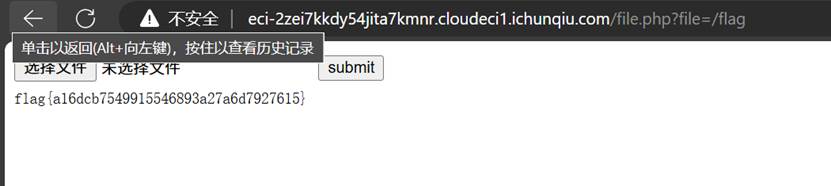
flag{a16dcb7549915546893a27a6d7927615}
15 Reverse easyasm
16位DOS
看了汇编代码发现主要有两个关键部分
程序开始时对一段数值(密钥)进行了预处理,做了一个冒泡排序,每次操作双字节
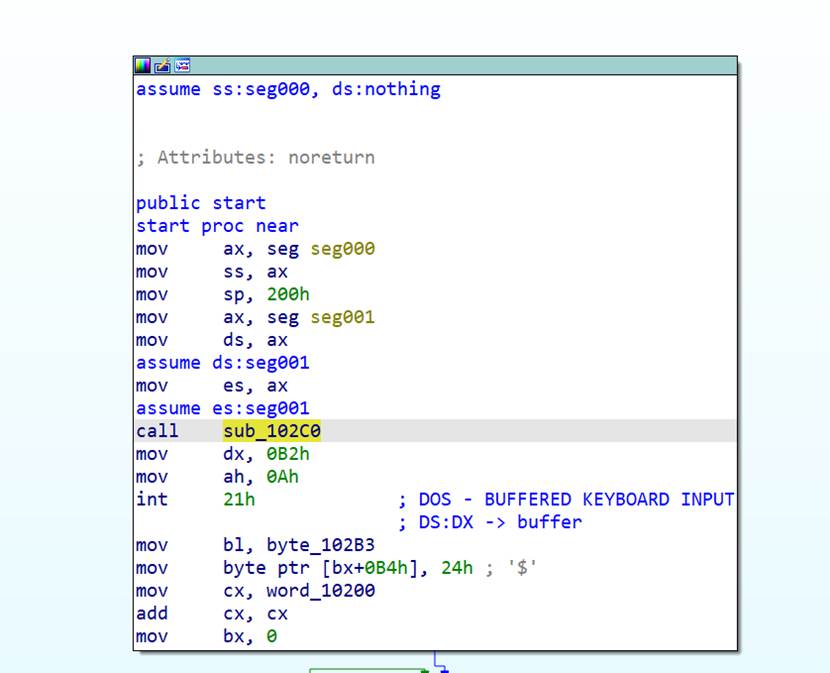
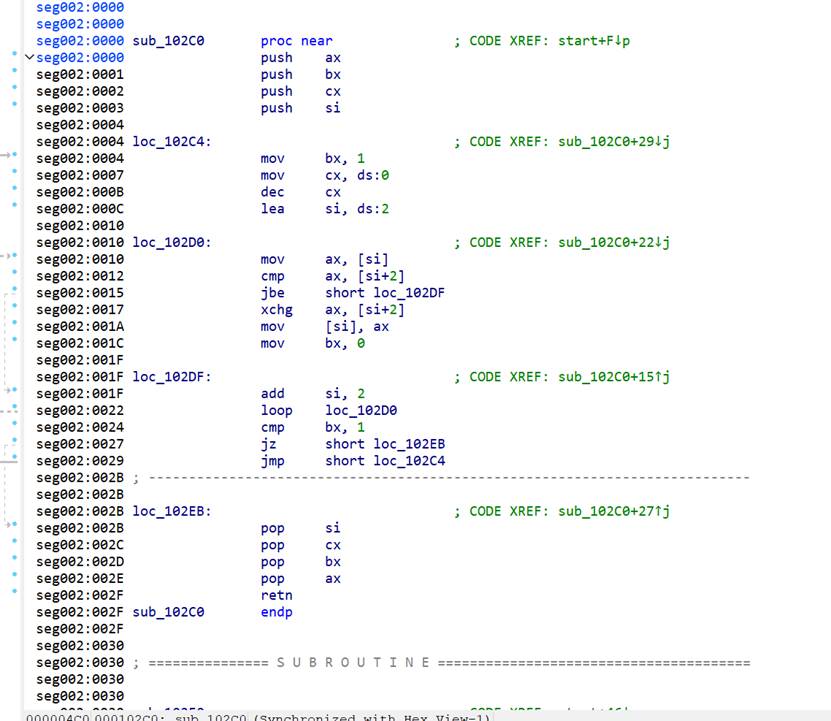
排序后的密钥会被拆分成高字节和低字节,然后与密文进行异或操作
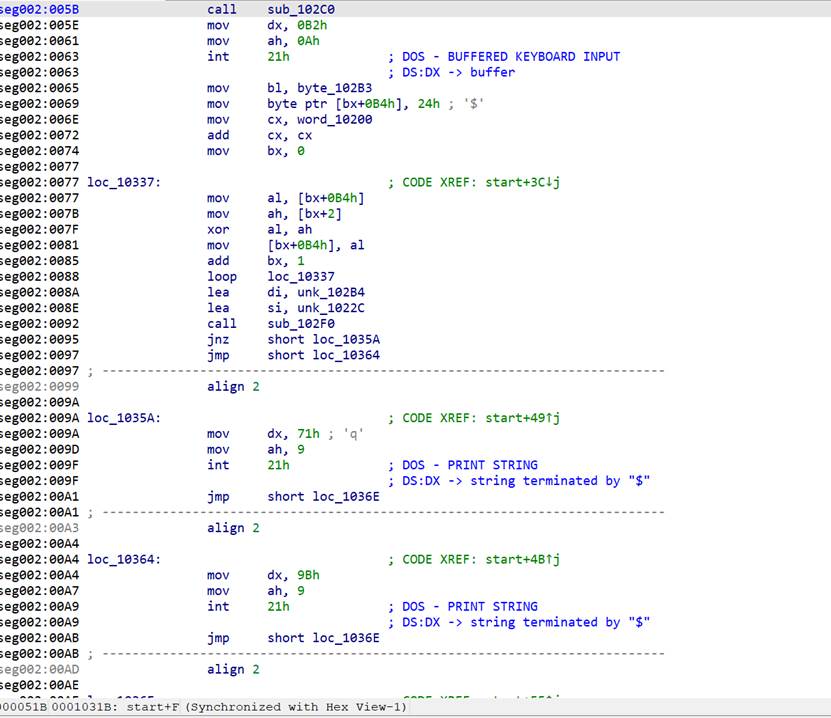
所以编写代码对密钥数组进行冒泡排序,将排序后的每个双字节值拆分成高字节和低字节,按顺序与密文进行异或运算
Exp:
1 | |
flag{dea54885-92b4-11ef-b153-3c0af33af908}